diff --git a/app-install/main.tf b/app-install/main.tf
index 04c314e..e501326 100644
--- a/app-install/main.tf
+++ b/app-install/main.tf
@@ -26,6 +26,7 @@ resource "null_resource" "application-install" {
provisioner "remote-exec" {
inline = [
+ "apt-get update",
"apt-get install apache2 -y"
]
}
diff --git a/docs/README.md b/docs/README.md
index 2c0a915..f1c133d 100644
--- a/docs/README.md
+++ b/docs/README.md
@@ -1,18 +1,30 @@
-# Seamless App Deployment with IBM Cloud's Secure Landing Zone
+# Seamless Deployment: From Provisioning to Runtime With the IBM Cloud VPC landing zone
-With the release of IBM Cloud Deployable Architectures, it is easy to provision an exisiting pre-defined architecture or customize and import.
+The introduction of IBM Cloud [deployable architectures](https://cloud.ibm.com/docs/secure-infrastructure-vpc?topic=secure-infrastructure-vpc-faqs) makes it easy to provision predefined architecture in no time.
-In this hands-on lab, you will learn to:
+## 📖 What you will learn
-1. Create a customized VPC-based topology using the VPC Landing Zone Deployable Architecture
-2. Deploy and expose a web application on top of this secure topology. For this lab, we will use an Apache service as an example.
-3. Share this deployable pattern with your enterprise through the IBM Cloud Private Catalog
+In this hands-on lab, you will learn how to work with the VPC landing zone deployable architecture to accomplish these goals.
-The objective of this lab is split into two distinct parts. The first part is built as a stepping stone for the second part.
+1. Create a customized VPC-based topology from the VPC landing zone deployable architecture.
+2. Deploy and expose a web application on this secure topology. For this lab, we use an Apache service as an example.
+3. Share this deployable pattern with your enterprise through the IBM Cloud private catalog.
-- Part 1 shows how the end-to-end steps to deploy a sample web application on top of a secure VPC-topology in your own account.
- - The secure VPC-based topology will be deployed using the Landing Zone Deployable Architecture.
- - Operator access will be provided through a manually deployed jump box VSI
- - An Apache server will be deployed in a secure VSI workload VPC
- - The web application will be exposed for outside access.
-- Part 2 shows how to automate the manual steps in Part 1, and then, how to package, and share the automation as a “Deployable Architecture” with other user through a private IBM Cloud Catalog
+The lab also introduces some concepts and background to help you to better get the "bigger" picture at the beginning. However, the hands-on steps are designed to be independent from the concepts and background information.
+
+## Lab structure
+
+Two labs are available. The two labs are independent. However, the first lab is a stepping stone in term of knowledge to the second lab.
+
+In [Lab 1](./part1/00-objectives), you take the perspective of a cloud infrastructure engineer:
+
+1. Use the [landing zone deployable architecture](https://cloud.ibm.com/docs/secure-infrastructure-vpc?topic=secure-infrastructure-vpc-overview) to automatically deploy a secure VPC-based topology in an IBM Cloud account.
+2. Manually customize the deployed infrastructure in the account in the following ways:
+ a. Provide operator access through a "jump box" VSI.
+ b. Install an Apache server in one of the workload VPCs that serves the web pages.
+ c. Expose the web pages that are served by the Apache server through a public VPC load balancer.
+
+In [Lab 2](./part2/00-objectives), you are a DevOps/automation engineer:
+
+1. Automate all the manual steps in lab 1.
+2. Package, and share the automation with other users as a **Deployable architecture** through a private IBM Cloud catalog. This packaging in a private catalog helps specific users to find and consume your automation.
diff --git a/docs/about/10-fs-cloud.md b/docs/about/10-fs-cloud.md
index 5996fb8..9c1583b 100644
--- a/docs/about/10-fs-cloud.md
+++ b/docs/about/10-fs-cloud.md
@@ -1,25 +1,9 @@
-# VPC Landing Zone
+# IBM Cloud for Financial Cloud Services Framework
-IBM VPC Landing Zone (“SLZ”) is a set of [Infrastructure-As-Code](https://en.wikipedia.org/wiki/Infrastructure_as_code) automation that enables creating a fully customizable VPC environment within a single region. The VPC Landing Zone is implemented in terraform and automates the provisioning, configuring, and integration of several services that participates in the realization of a compliant VPC-based topology:
+IBM Cloud Framework for Financial Services provides comprehensive and detailed guidance around regulatory compliance, security, and resiliency to help address the needs of enterprises both during initial deployment and with ongoing operations. For more information, see [Getting started with IBM Cloud for Financial Services](https://cloud.ibm.com/docs/framework-financial-services?topic=framework-financial-services-about).
-- A resource group for cloud services and for each VPC.
-- Cloud Object Storage instances for flow logs and Activity Tracker
-- Encryption keys in either a Key Protect or Hyper Protect Crypto Services instance
-- A management and workload VPC connected by a transit gateway
-- A flow log collector for each VPC
-- All necessary networking rules to allow communication.
-- Virtual Private Endpoint (VPE) for Cloud Object Storage in each VPC
-- A VPN gateway in the management VPC
+The framework was initially based on the needs of financial institutions, as its name indicates. However, it can be used as a compliance and security starting point and baseline for most industries.
-[Available VPC Landing Zone terraform modules](https://github.com/terraform-ibm-modules/terraform-ibm-landing-zone)
-
-VPC Landing Zone comes with four fully functional patterns that are strictly following the IBM Cloud Financial Services reference architecture:
-
-- VPC pattern
-- VPC with Virtual Servers (“VSIs”) – which the lab will use.
-- VPC with OpenShift
-- VPC with VSIs and OpenShift (“mixed”) pattern.
-
-Each of the patterns can be used as a starting point to create your own customizable VPC-based topology that matches your enterprise or customer exact needs.
+The framework provides secure [VPC reference architectures](https://cloud.ibm.com/docs/framework-financial-services?topic=framework-financial-services-vpc-architecture-about) that meet a number of regulatory controls.

diff --git a/docs/about/20-vpc-landing-zone.md b/docs/about/20-vpc-landing-zone.md
index a388bc0..e3ed6e9 100644
--- a/docs/about/20-vpc-landing-zone.md
+++ b/docs/about/20-vpc-landing-zone.md
@@ -1,9 +1,29 @@
-# IBM Cloud for Financial Cloud Services Framework
+# VPC landing zone
-The IBM Cloud Financial Cloud Services Framework provides comprehensive and detailed guidance to help address the needs of enterprises with regulatory compliance, security, and resiliency during the initial deployment phase and with ongoing operations.
+IBM VPC landing zone (also referred to as "SLZ" for secure landing zone) is [Infrastructure-As-Code](https://en.wikipedia.org/wiki/Infrastructure_as_code) automation that enables you to create a fully customizable VPC environment within a single region. The VPC landing zone is implemented in Terraform and automates the provisioning, configuring, and integration of several services that participate in the realization of a compliant VPC-based topology that is aligned with the documented [IBM Cloud for Financial Cloud Services Framework](./about/10-fs-cloud).
-Whilst the framework was initially based on the needs of financial institutions, as its name indicates, it can be used as a starting point and baseline for meeting compliance and security for most industries.
+The automation is available as a set of [Terraform modules on GitHub](https://github.com/terraform-ibm-modules/terraform-ibm-landing-zone). The automation creates and configures all of the resources necessary to create a secure and compliant topology:
+- A resource group for cloud services and for each VPC
+- Cloud Object Storage instances for flow logs and Activity Tracker (access and audit logs)
+- Encryption keys in either a Key Protect or Hyper Protect Crypto Services instance
+- A management and workload VPC connected by a transit gateway
+- A flow log collector for each VPC
+- All necessary networking rules to allow communication.
+- Virtual Private Endpoint (VPE) for Cloud Object Storage in each VPC
+- A VPN gateway in the management VPC
-[Getting started with IBM Cloud for Financial Services](https://cloud.ibm.com/docs/framework-financial-services?topic=framework-financial-services-about)
+# Landing zone patterns
-The framework provides secure [VPC reference architectures](https://cloud.ibm.com/docs/framework-financial-services?topic=framework-financial-services-vpc-architecture-about) meeting with a number of regulatory controls.
+
+VPC landing zone comes with four fully functional patterns that follow the IBM Cloud Framework for Financial Services reference architecture:
+
+- VPC pattern
+- VPC with Virtual Servers ("VSIs") – which the lab uses.
+- VPC with Red Hat OpenShift ("ROKS")
+- VPC with VSIs and Red Hat OpenShift ("mixed") pattern.
+
+| VPC pattern | Virtual server pattern | Red Hat OpenShift pattern | Mixed pattern |
+| ------------------------------ | -------------------------------- | -------------------------------- | ---------------------------------- |
+| [](https://github.com/terraform-ibm-modules/terraform-ibm-landing-zone/blob/main/patterns/vpc/README.md) | [](https://github.com/terraform-ibm-modules/terraform-ibm-landing-zone/blob/main/patterns/vsi/README.md) | [](https://github.com/terraform-ibm-modules/terraform-ibm-landing-zone/blob/main/patterns/roks/README.md) | [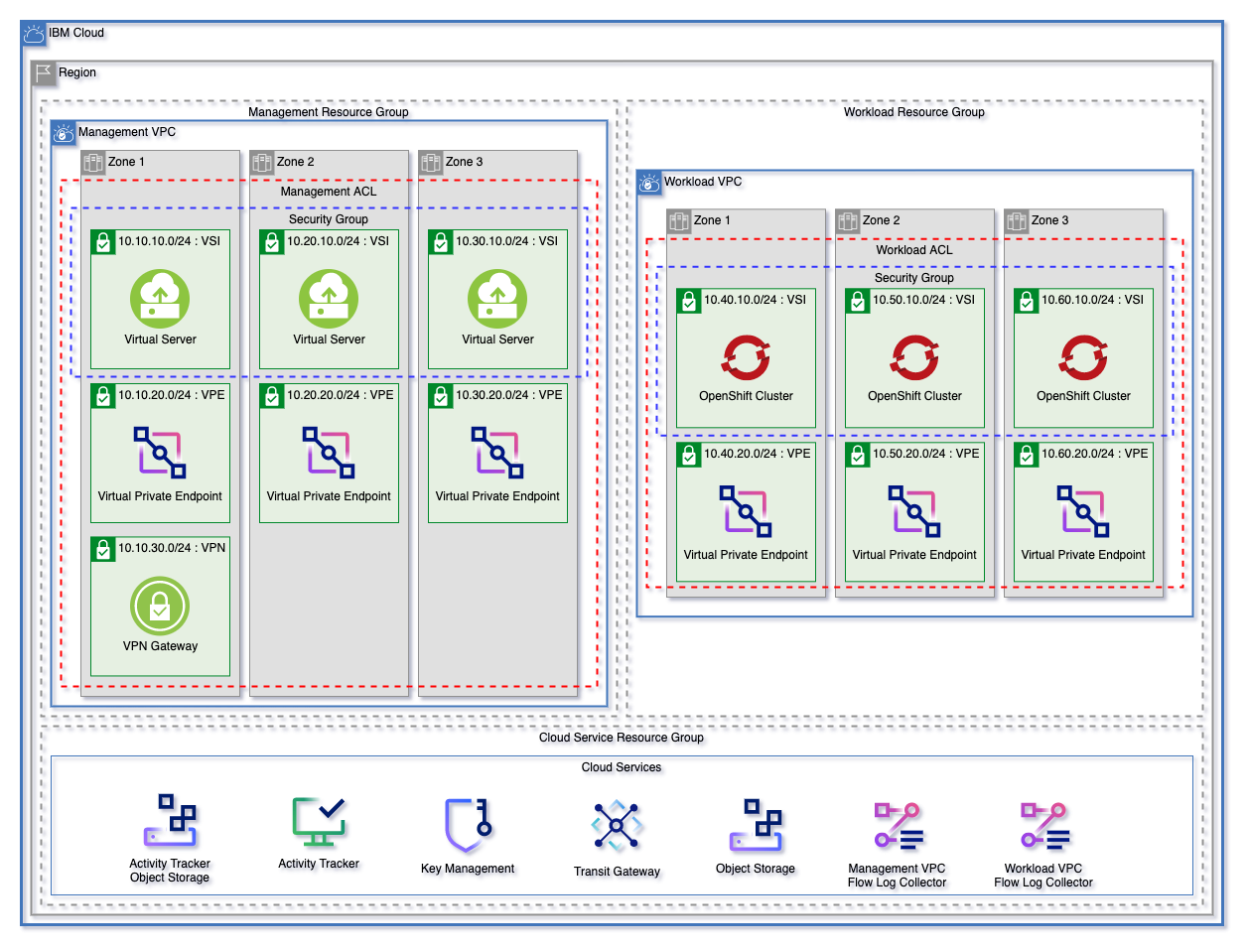](https://github.com/terraform-ibm-modules/terraform-ibm-landing-zone/blob/main/patterns/mixed/README.md) |
+
+You can use any pattern as a starting point to create a customizable VPC-based topology that supports your customer needs or the needs of your enterprise.
diff --git a/docs/about/30-deployable-arch.md b/docs/about/30-deployable-arch.md
index 4ca16a2..1a3d96a 100644
--- a/docs/about/30-deployable-arch.md
+++ b/docs/about/30-deployable-arch.md
@@ -1,21 +1,21 @@
-# Deployable Architecture
+# Deployable architecture
-“Deployable Architecture” is officially defined as “Cloud automation for deploying a common architectural pattern that combines one or more cloud resources that is designed for easy deployment, scalability, and modularity.”
+A deployable architecture is defined as "Cloud automation for deploying a common architectural pattern that combines one or more cloud resources that is designed for easy deployment, scalability, and modularity.
-More specifically, and concretely, from a technical perspective, “Deployable Architectures” are essentially terraform modules that are fully integrated into the IBM Cloud experience. Deployable Architecture are:
+From a technical perspective, deployable architectures are essentially Terraform modules that are fully integrated into the IBM Cloud experience. Deployable architectures have these characteristics:
-- Discoverable and available through the IBM Cloud Catalog (and through IBM Cloud search)
-- Fully integrated in IBM Cloud Projects and Schematics.
+- Discoverable and available through the IBM Cloud catalog (and through IBM Cloud search)
+- Fully integrated in IBM Cloud projects and Schematics
- Integrated with [IBM Cloud Risk Analyzer](https://cloud.ibm.com/docs/code-risk-analyzer-cli-plugin?topic=code-risk-analyzer-cli-plugin-cra-cli-plugin#terraform-command)
-In other words, it is possible for an end-user to execute the terraform automation behind a “Deployable Architecture” just from a few clicks and inputs in the IBM Cloud console.
+In other words, a user can run the Terraform automation behind a deployable architecture just from a few clicks and inputs in the IBM Cloud console.
-
+
-The Landing Zone terraform module and patterns described just above have a corresponding [Deployable Architecture](https://cloud.ibm.com/docs/secure-infrastructure-vpc?topic=secure-infrastructure-vpc-overview) in IBM Cloud. In this lab, the Secure Landing Zone is consumed through the Deployable Architecture experience for ease of use, rather than using the terraform CLI against the open-source github version.
+The landing zone Terraform module and patterns that are described in [🌍 VPC landing zone](./about/20-vpc-landing-zone.md) have a corresponding [deployable architecture](https://cloud.ibm.com/docs/secure-infrastructure-vpc?topic=secure-infrastructure-vpc-overview) in IBM Cloud. To help you learn about deployable architectures, this lab provides steps for deploying the deployable architecture in IBM Cloud rather than by running Terraform commands against the open source GitHub version.
-IBM-maintained Deployable Architectures, like the Landing Zone Deployable Architecture:
+IBM-maintained deployable architectures are just like the landing zone deployable architecture in these ways:
- Provide the same level of customer support as any other IBM Cloud product
-- [Come with extensive documentation](https://cloud.ibm.com/docs/secure-infrastructure-vpc?topic=secure-infrastructure-vpc-overview)
-- Are maintained and remains current over time
+- Come with extensive [documentation](https://cloud.ibm.com/docs/secure-infrastructure-vpc?topic=secure-infrastructure-vpc-overview)
+- Are maintained to stay current
diff --git a/docs/about/40-projects.md b/docs/about/40-projects.md
index 28c3333..4ad30f9 100644
--- a/docs/about/40-projects.md
+++ b/docs/about/40-projects.md
@@ -1,18 +1,19 @@
-# IBM Cloud Projects
+# IBM Cloud projects
-IBM Cloud Projects make it easy to manage Infrastructure-As-Code deployments across accounts, collaborate with team members, and maintain compliance.
+IBM Cloud projects make it easy to manage Infrastructure-As-Code (IaC) deployments across accounts, collaborate with team members, and maintain compliance.
-At its core, an IBM Cloud Project is made up of a collection of configurations that are used to manage related Infrastructure as Code (IaC) deployments (and associated resources) across accounts.
+At its core, an IBM Cloud project is made up of a collection of configurations that are used to manage related Infrastructure as Code (IaC) deployments (and associated resources) across accounts.
-As a concrete example, let’s imagine the scenario of a SRE team responsible for setting up the infrastructure supporting the web application. That SRE team wants to follow best practices and deploy the following environments, all based on the same Deployable Architecture template (but with slight configuration differences for each environment):
+For example, let’s imagine the scenario of a SRE team that is responsible for setting up the infrastructure that supports the web application. That SRE team wants to follow best practices and deploy the following environments, which are based on the same deployable architecture template (but with slight configuration differences for each environment):
-1. A development environment – with scaled down compute resources and no audit event tracking.
-2. A staging environment – as close as possible to the production environment
-3. 2 production environments: one in America and another one in Europe.
+1. A development environment: with scaled down compute resources and no audit event tracking.
+2. A staging environment: as close as possible to the production environment
+3. Two production environments: one in North America and another one in Europe.
-That SRE team can group configurations, and thus centralize the governance, for the 4 different environments in one single Project.
+That SRE team can group configurations, and thus centralize the governance and supervision, for the four different environments in one single Project.
-Beyond the core configuration grouping capability, IBM Cloud Projects is designed with an IaC and a compliance-first approach. Projects also seemingly integrate with IBM Cloud Schematics to deploy, update, and manage the resources created by the IaC automation.
-Each project also includes tools to scan for potentially harmful resource changes, compliance, security, and cost, as well as tracking configuration versioning and governance.
+Beyond the core configuration grouping capability, IBM Cloud projects is designed with an IaC and a compliance-first approach. Projects also seemingly integrates with IBM Cloud Schematics to deploy, update, and manage the resources that are created by the IaC automation.
-
+Each project also includes tools to scan for potentially harmful resource changes, compliance, security, and cost issues, and to track configuration versioning and governance.
+
+
diff --git a/docs/cover.md b/docs/cover.md
index d887025..872f3a6 100644
--- a/docs/cover.md
+++ b/docs/cover.md
@@ -1,7 +1,7 @@
-> Seamless App Deployment with
-> IBM Cloud's Secure Landing Zone
+> Seamless Deployment: From Provisioning to Runtime
+> with IBM Cloud VPC landing zone
_Session 2448_
diff --git a/docs/images/favicon.svg b/docs/images/favicon.svg
index 4f05647..7c8f876 100644
--- a/docs/images/favicon.svg
+++ b/docs/images/favicon.svg
@@ -1 +1 @@
-
+
diff --git a/docs/images/part-1/10-configuration.png b/docs/images/part-1/10-configuration.png
new file mode 100644
index 0000000..6b6cfe9
Binary files /dev/null and b/docs/images/part-1/10-configuration.png differ
diff --git a/docs/images/part-1/10-deployment.png b/docs/images/part-1/10-deployment.png
new file mode 100644
index 0000000..23c2c1c
Binary files /dev/null and b/docs/images/part-1/10-deployment.png differ
diff --git a/docs/images/part-1/10-deployment.png:Zone.Identifier b/docs/images/part-1/10-deployment.png:Zone.Identifier
new file mode 100644
index 0000000..2dac2bc
--- /dev/null
+++ b/docs/images/part-1/10-deployment.png:Zone.Identifier
@@ -0,0 +1,3 @@
+[ZoneTransfer]
+LastWriterPackageFamilyName=Microsoft.MSPaint_8wekyb3d8bbwe
+ZoneId=3
diff --git a/docs/images/part-1/10-overview-page.png b/docs/images/part-1/10-overview-page.png
new file mode 100644
index 0000000..c68f936
Binary files /dev/null and b/docs/images/part-1/10-overview-page.png differ
diff --git a/docs/images/part-1/10-validation.png b/docs/images/part-1/10-validation.png
new file mode 100644
index 0000000..8d91edc
Binary files /dev/null and b/docs/images/part-1/10-validation.png differ
diff --git a/docs/images/part-1/20-floating-ip.png b/docs/images/part-1/20-floating-ip.png
new file mode 100644
index 0000000..616f87a
Binary files /dev/null and b/docs/images/part-1/20-floating-ip.png differ
diff --git a/docs/images/part-1/20-network-int-pencil.png b/docs/images/part-1/20-network-int-pencil.png
new file mode 100644
index 0000000..624bed4
Binary files /dev/null and b/docs/images/part-1/20-network-int-pencil.png differ
diff --git a/docs/images/part-1/20-ssh-acl-inbound.png b/docs/images/part-1/20-ssh-acl-inbound.png
new file mode 100644
index 0000000..97ff07d
Binary files /dev/null and b/docs/images/part-1/20-ssh-acl-inbound.png differ
diff --git a/docs/images/part-1/20-ssh-acl-outbound.png b/docs/images/part-1/20-ssh-acl-outbound.png
new file mode 100644
index 0000000..5a631ff
Binary files /dev/null and b/docs/images/part-1/20-ssh-acl-outbound.png differ
diff --git a/docs/images/part-1/20-ssh-sg.png b/docs/images/part-1/20-ssh-sg.png
new file mode 100644
index 0000000..b4d9db2
Binary files /dev/null and b/docs/images/part-1/20-ssh-sg.png differ
diff --git a/docs/images/part-1/30-mgmt-ssh-acl-inbound.png b/docs/images/part-1/30-mgmt-ssh-acl-inbound.png
new file mode 100644
index 0000000..89b9521
Binary files /dev/null and b/docs/images/part-1/30-mgmt-ssh-acl-inbound.png differ
diff --git a/docs/images/part-1/30-mgmt-ssh-acl-outbound.png b/docs/images/part-1/30-mgmt-ssh-acl-outbound.png
new file mode 100644
index 0000000..c8b4dbe
Binary files /dev/null and b/docs/images/part-1/30-mgmt-ssh-acl-outbound.png differ
diff --git a/docs/images/part-1/30-private-ip.png b/docs/images/part-1/30-private-ip.png
new file mode 100644
index 0000000..5119780
Binary files /dev/null and b/docs/images/part-1/30-private-ip.png differ
diff --git a/docs/images/part-1/30-workload-ssh-acl-inbound.png b/docs/images/part-1/30-workload-ssh-acl-inbound.png
new file mode 100644
index 0000000..7e9e7dc
Binary files /dev/null and b/docs/images/part-1/30-workload-ssh-acl-inbound.png differ
diff --git a/docs/images/part-1/30-workload-ssh-acl-outbound.png b/docs/images/part-1/30-workload-ssh-acl-outbound.png
new file mode 100644
index 0000000..4e54f15
Binary files /dev/null and b/docs/images/part-1/30-workload-ssh-acl-outbound.png differ
diff --git a/docs/images/part-1/40-acl-inbound.png b/docs/images/part-1/40-acl-inbound.png
new file mode 100644
index 0000000..0986589
Binary files /dev/null and b/docs/images/part-1/40-acl-inbound.png differ
diff --git a/docs/images/part-1/40-acl-outbound.png b/docs/images/part-1/40-acl-outbound.png
new file mode 100644
index 0000000..be0909b
Binary files /dev/null and b/docs/images/part-1/40-acl-outbound.png differ
diff --git a/docs/images/part-1/40-sg.png b/docs/images/part-1/40-sg.png
new file mode 100644
index 0000000..afd35b5
Binary files /dev/null and b/docs/images/part-1/40-sg.png differ
diff --git a/docs/images/part-1/50-c2s.png b/docs/images/part-1/50-c2s.png
new file mode 100644
index 0000000..fa8398e
Binary files /dev/null and b/docs/images/part-1/50-c2s.png differ
diff --git a/docs/images/part-2/16ac8f7add0155eacbc958df9b14489264e9574b.png b/docs/images/part-2/16ac8f7add0155eacbc958df9b14489264e9574b.png
new file mode 100644
index 0000000..a2220c7
Binary files /dev/null and b/docs/images/part-2/16ac8f7add0155eacbc958df9b14489264e9574b.png differ
diff --git a/docs/images/part-2/366e1c7205147143b2bf25c68e2dc30deed8679c.png b/docs/images/part-2/366e1c7205147143b2bf25c68e2dc30deed8679c.png
new file mode 100644
index 0000000..45b0c31
Binary files /dev/null and b/docs/images/part-2/366e1c7205147143b2bf25c68e2dc30deed8679c.png differ
diff --git a/docs/images/part-2/520e1108848d01be4e7f9a8b40b36435dcecaa02.png b/docs/images/part-2/520e1108848d01be4e7f9a8b40b36435dcecaa02.png
new file mode 100644
index 0000000..a80bc3b
Binary files /dev/null and b/docs/images/part-2/520e1108848d01be4e7f9a8b40b36435dcecaa02.png differ
diff --git a/docs/images/part-2/708ba95b2a76860568ee6d085b47d4d7777d748b.png b/docs/images/part-2/708ba95b2a76860568ee6d085b47d4d7777d748b.png
new file mode 100644
index 0000000..27dbf46
Binary files /dev/null and b/docs/images/part-2/708ba95b2a76860568ee6d085b47d4d7777d748b.png differ
diff --git a/docs/images/part-2/72a9d91f4543d58261951b90512784e62d4df141.png b/docs/images/part-2/72a9d91f4543d58261951b90512784e62d4df141.png
new file mode 100644
index 0000000..fb61a36
Binary files /dev/null and b/docs/images/part-2/72a9d91f4543d58261951b90512784e62d4df141.png differ
diff --git a/docs/images/part-2/8189e32b5ed54528a3fe0cd0ab18af214555cc7d.png b/docs/images/part-2/8189e32b5ed54528a3fe0cd0ab18af214555cc7d.png
new file mode 100644
index 0000000..ee52113
Binary files /dev/null and b/docs/images/part-2/8189e32b5ed54528a3fe0cd0ab18af214555cc7d.png differ
diff --git a/docs/images/part-2/8d1be5e148980da96710b4ede30117ae9babd529.png b/docs/images/part-2/8d1be5e148980da96710b4ede30117ae9babd529.png
new file mode 100644
index 0000000..c48b61f
Binary files /dev/null and b/docs/images/part-2/8d1be5e148980da96710b4ede30117ae9babd529.png differ
diff --git a/docs/images/part-2/8ede5141765f7fc8fc5d8f1c669613227075a83c.png b/docs/images/part-2/8ede5141765f7fc8fc5d8f1c669613227075a83c.png
new file mode 100644
index 0000000..670fe3a
Binary files /dev/null and b/docs/images/part-2/8ede5141765f7fc8fc5d8f1c669613227075a83c.png differ
diff --git a/docs/images/part-2/c4a6c586954e853f8fa36d097f311cf25c71ba09.png b/docs/images/part-2/c4a6c586954e853f8fa36d097f311cf25c71ba09.png
new file mode 100644
index 0000000..4e90338
Binary files /dev/null and b/docs/images/part-2/c4a6c586954e853f8fa36d097f311cf25c71ba09.png differ
diff --git a/docs/images/part-2/cdbc891686d226024c1d5da0aef003a858508460.png b/docs/images/part-2/cdbc891686d226024c1d5da0aef003a858508460.png
new file mode 100644
index 0000000..2c759d9
Binary files /dev/null and b/docs/images/part-2/cdbc891686d226024c1d5da0aef003a858508460.png differ
diff --git a/docs/images/part-2/e49d98bdf9d5c5fe23d2f0f3b04b2e0b271b50e4.png b/docs/images/part-2/e49d98bdf9d5c5fe23d2f0f3b04b2e0b271b50e4.png
new file mode 100644
index 0000000..87c61ad
Binary files /dev/null and b/docs/images/part-2/e49d98bdf9d5c5fe23d2f0f3b04b2e0b271b50e4.png differ
diff --git a/docs/images/part-2/eb92cfbd40e4d346943f162d58a9c509f2262efc.png b/docs/images/part-2/eb92cfbd40e4d346943f162d58a9c509f2262efc.png
new file mode 100644
index 0000000..f69cac0
Binary files /dev/null and b/docs/images/part-2/eb92cfbd40e4d346943f162d58a9c509f2262efc.png differ
diff --git a/docs/images/part-2/ee8a02736dedaaec38f6826ef5e454765563da63.png b/docs/images/part-2/ee8a02736dedaaec38f6826ef5e454765563da63.png
new file mode 100644
index 0000000..bf44cdd
Binary files /dev/null and b/docs/images/part-2/ee8a02736dedaaec38f6826ef5e454765563da63.png differ
diff --git a/docs/images/part-2/ef502cb9edd49d7f1c226268ea4099d1d21ee566.png b/docs/images/part-2/ef502cb9edd49d7f1c226268ea4099d1d21ee566.png
new file mode 100644
index 0000000..15b1765
Binary files /dev/null and b/docs/images/part-2/ef502cb9edd49d7f1c226268ea4099d1d21ee566.png differ
diff --git a/docs/images/part-2/f35f2e7ea685311f9ff32b22d3ec33dc86a5cd7e.png b/docs/images/part-2/f35f2e7ea685311f9ff32b22d3ec33dc86a5cd7e.png
new file mode 100644
index 0000000..b146158
Binary files /dev/null and b/docs/images/part-2/f35f2e7ea685311f9ff32b22d3ec33dc86a5cd7e.png differ
diff --git a/docs/images/part-2/fe1c405a22514718df660e8e3ce13f96060e0065.png b/docs/images/part-2/fe1c405a22514718df660e8e3ce13f96060e0065.png
new file mode 100644
index 0000000..466d49c
Binary files /dev/null and b/docs/images/part-2/fe1c405a22514718df660e8e3ce13f96060e0065.png differ
diff --git a/docs/images/part-2/ffbd5d3eb533623f2b7e3196d9947c898928fbbf.png b/docs/images/part-2/ffbd5d3eb533623f2b7e3196d9947c898928fbbf.png
new file mode 100644
index 0000000..95e857d
Binary files /dev/null and b/docs/images/part-2/ffbd5d3eb533623f2b7e3196d9947c898928fbbf.png differ
diff --git a/docs/images/part-2/media/image1.jpg b/docs/images/part-2/media/image1.jpg
new file mode 100644
index 0000000..f6f51a9
Binary files /dev/null and b/docs/images/part-2/media/image1.jpg differ
diff --git a/docs/images/part-2/media/image10.png b/docs/images/part-2/media/image10.png
new file mode 100644
index 0000000..f037f73
Binary files /dev/null and b/docs/images/part-2/media/image10.png differ
diff --git a/docs/images/part-2/media/image11.png b/docs/images/part-2/media/image11.png
new file mode 100644
index 0000000..3fbbee1
Binary files /dev/null and b/docs/images/part-2/media/image11.png differ
diff --git a/docs/images/part-2/media/image12.png b/docs/images/part-2/media/image12.png
new file mode 100644
index 0000000..2efb7f5
Binary files /dev/null and b/docs/images/part-2/media/image12.png differ
diff --git a/docs/images/part-2/media/image13.png b/docs/images/part-2/media/image13.png
new file mode 100644
index 0000000..2308d8b
Binary files /dev/null and b/docs/images/part-2/media/image13.png differ
diff --git a/docs/images/part-2/media/image14.png b/docs/images/part-2/media/image14.png
new file mode 100644
index 0000000..c1c0f0e
Binary files /dev/null and b/docs/images/part-2/media/image14.png differ
diff --git a/docs/images/part-2/media/image15.png b/docs/images/part-2/media/image15.png
new file mode 100644
index 0000000..04096e1
Binary files /dev/null and b/docs/images/part-2/media/image15.png differ
diff --git a/docs/images/part-2/media/image16.png b/docs/images/part-2/media/image16.png
new file mode 100644
index 0000000..89b7479
Binary files /dev/null and b/docs/images/part-2/media/image16.png differ
diff --git a/docs/images/part-2/media/image17.png b/docs/images/part-2/media/image17.png
new file mode 100644
index 0000000..aa560cb
Binary files /dev/null and b/docs/images/part-2/media/image17.png differ
diff --git a/docs/images/part-2/media/image18.png b/docs/images/part-2/media/image18.png
new file mode 100644
index 0000000..8bcb5d3
Binary files /dev/null and b/docs/images/part-2/media/image18.png differ
diff --git a/docs/images/part-2/media/image19.png b/docs/images/part-2/media/image19.png
new file mode 100644
index 0000000..f685a91
Binary files /dev/null and b/docs/images/part-2/media/image19.png differ
diff --git a/docs/images/part-2/media/image2.png b/docs/images/part-2/media/image2.png
new file mode 100644
index 0000000..5bbd7c3
Binary files /dev/null and b/docs/images/part-2/media/image2.png differ
diff --git a/docs/images/part-2/media/image21.png b/docs/images/part-2/media/image21.png
new file mode 100644
index 0000000..ee0eec9
Binary files /dev/null and b/docs/images/part-2/media/image21.png differ
diff --git a/docs/images/part-2/media/image24.png b/docs/images/part-2/media/image24.png
new file mode 100644
index 0000000..4c5ad19
Binary files /dev/null and b/docs/images/part-2/media/image24.png differ
diff --git a/docs/images/part-2/media/image25.png b/docs/images/part-2/media/image25.png
new file mode 100644
index 0000000..8fd9d70
Binary files /dev/null and b/docs/images/part-2/media/image25.png differ
diff --git a/docs/images/part-2/media/image26.png b/docs/images/part-2/media/image26.png
new file mode 100644
index 0000000..b0a6bb3
Binary files /dev/null and b/docs/images/part-2/media/image26.png differ
diff --git a/docs/images/part-2/media/image29.png b/docs/images/part-2/media/image29.png
new file mode 100644
index 0000000..7efb7df
Binary files /dev/null and b/docs/images/part-2/media/image29.png differ
diff --git a/docs/images/part-2/media/image3.png b/docs/images/part-2/media/image3.png
new file mode 100644
index 0000000..38f7361
Binary files /dev/null and b/docs/images/part-2/media/image3.png differ
diff --git a/docs/images/part-2/media/image30.png b/docs/images/part-2/media/image30.png
new file mode 100644
index 0000000..6353886
Binary files /dev/null and b/docs/images/part-2/media/image30.png differ
diff --git a/docs/images/part-2/media/image4.png b/docs/images/part-2/media/image4.png
new file mode 100644
index 0000000..20ce48a
Binary files /dev/null and b/docs/images/part-2/media/image4.png differ
diff --git a/docs/images/part-2/media/image5.png b/docs/images/part-2/media/image5.png
new file mode 100644
index 0000000..68df0cb
Binary files /dev/null and b/docs/images/part-2/media/image5.png differ
diff --git a/docs/images/part-2/media/image6.png b/docs/images/part-2/media/image6.png
new file mode 100644
index 0000000..ef250de
Binary files /dev/null and b/docs/images/part-2/media/image6.png differ
diff --git a/docs/images/part-2/media/image7.png b/docs/images/part-2/media/image7.png
new file mode 100644
index 0000000..f7db2b2
Binary files /dev/null and b/docs/images/part-2/media/image7.png differ
diff --git a/docs/images/part-2/media/image8.png b/docs/images/part-2/media/image8.png
new file mode 100644
index 0000000..d7b3007
Binary files /dev/null and b/docs/images/part-2/media/image8.png differ
diff --git a/docs/images/part-2/media/image9.png b/docs/images/part-2/media/image9.png
new file mode 100644
index 0000000..4c9ef01
Binary files /dev/null and b/docs/images/part-2/media/image9.png differ
diff --git a/docs/images/part-2/override-gui.png b/docs/images/part-2/override-gui.png
new file mode 100644
index 0000000..7066211
Binary files /dev/null and b/docs/images/part-2/override-gui.png differ
diff --git a/docs/index.html b/docs/index.html
index f6e704f..ec0d16e 100644
--- a/docs/index.html
+++ b/docs/index.html
@@ -7,7 +7,7 @@
name="viewport"
content="width=device-width, initial-scale=1, minimum-scale=1.0, shrink-to-fit=no"
/>
- Deploy your first application to IBM Cloud in 3 clicks | IBM TechXchange 2023
+ Seamless Deployment: From Provisioning to Runtime with IBM Cloud's Landing Zone Deployable Architecture | IBM TechXchange 2023
@@ -48,14 +48,14 @@
@@ -83,5 +87,7 @@
+
+