-
Notifications
You must be signed in to change notification settings - Fork 32
Open
Labels
Description
Hello,
I have tried testing the docker image, but it doesn't work for me as expected.
Here is the result when I go to http://auth.example.com/:
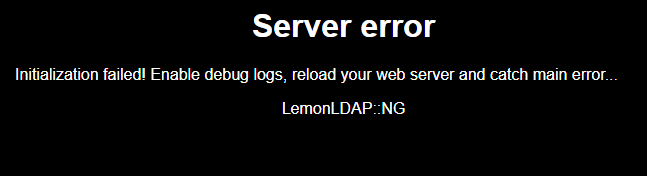
Here is how I built the image:
FROM coudot/lemonldap-ng:2.0.12docker build --pull -t local/lemoldap . docker run -d \
--name "lemonldap-app" \
-p 80:80 \
-e "SSODOMAIN=example.com" \
-e LOGLEVEL=debug \
"local/lemoldap"These are the logs right after the container starts:
[Wed Jul 28 06:57:16 2021] [LLNG:30] [debug] Logger Lemonldap::NG::Common::Logger::Std loaded
[Wed Jul 28 06:57:16 2021] [LLNG:30] [debug] User logger Lemonldap::NG::Common::Logger::Std loaded
[Wed Jul 28 06:57:16 2021] [LLNG:30] [debug] Check configuration for Lemonldap::NG::Handler::Server::Main
[Wed Jul 28 06:57:16 2021] [LLNG:30] [debug] Lemonldap::NG::Common::Conf::Backends::File loaded.
Get configuration 1.
[Wed Jul 28 06:57:16 2021] [LLNG:30] [debug] Get configuration 1
[Wed Jul 28 06:57:16 2021] [LLNG:30] [error] No configuration available
FastCGI: manager (pid 30): initialized
FastCGI: manager (pid 30): server (pid 40) started
FastCGI: server (pid 40): initialized
FastCGI: manager (pid 30): server (pid 41) started
FastCGI: server (pid 41): initialized
FastCGI: manager (pid 30): server (pid 42) started
FastCGI: server (pid 42): initialized
FastCGI: manager (pid 30): server (pid 43) started
FastCGI: server (pid 43): initialized
FastCGI: manager (pid 30): server (pid 44) started
FastCGI: server (pid 44): initialized
FastCGI: manager (pid 30): server (pid 45) started
FastCGI: server (pid 45): initialized
FastCGI: manager (pid 30): server (pid 46) started
FastCGI: server (pid 46): initialized
Starting periodic command scheduler: cron.
Starting anac(h)ronistic cron: anacron.
Here are the logs after opening the url:
[Wed Jul 28 06:58:17 2021] [LLNG:40] [debug] Logger Lemonldap::NG::Common::Logger::Std loaded
[Wed Jul 28 06:58:17 2021] [LLNG:40] [debug] User logger Lemonldap::NG::Common::Logger::Std loaded
[Wed Jul 28 06:58:17 2021] [LLNG:40] [debug] Check configuration for Lemonldap::NG::Handler::PSGI::Main
172.17.0.1 - - [28/Jul/2021:06:58:17 +0000] "GET / HTTP/1.1" 500 407 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.107 Safari/537.36 Edg/92.0.902.55"
[Wed Jul 28 06:58:17 2021] [LLNG:40] [debug] Lemonldap::NG::Common::Conf::Backends::File loaded.
Configuration unchanged, get configuration from cache.
[Wed Jul 28 06:58:17 2021] [LLNG:40] [debug] Get configuration 1
[Wed Jul 28 06:58:17 2021] [LLNG:40] [error] No configuration available
[Wed Jul 28 06:58:17 2021] [LLNG:40] [error] Initialization failed: Unable to protect this server ()
[Wed Jul 28 06:58:17 2021] [LLNG:40] [error] Initialization failed! Enable debug logs, reload your web server and catch main error...
[Wed Jul 28 06:58:17 2021] [LLNG:40] [debug] Returned userId: anonymous
[Wed Jul 28 06:58:17 2021] [LLNG:40] [warn] [anonymous] Initialization failed! Enable debug logs, reload your web server and catch main error...
[Wed Jul 28 06:58:17 2021] [LLNG:40] [debug] [warn] [anonymous] Initialization failed! Enable debug logs, reload your web server and catch main error...
[Wed Jul 28 06:58:17 2021] [LLNG:40] [error] Error 500: Initialization failed! Enable debug logs, reload your web server and catch main error...
/etc/lemonldap-ng/lemonldap-ng.ini:
;==============================================================================
; LemonLDAP::NG local configuration parameters
;
; This file is dedicated to configuration parameters override
; You can set here configuration parameters that will be used only by
; local LemonLDAP::NG elements
;
; Section "all" is always read first before "portal", "handler"
; and "manager"
;
; Section "configuration" is used to load global configuration and set cache
; (replace old storage.conf file)
;
; Other section are only read by the specific LemonLDAP::NG component
;==============================================================================
[all]
; CUSTOM FUNCTION
; If you want to create customFunctions in rules, declare them here:
;require = Package
; Prevent Portal to crash if Perl module is not found
;requireDontDie = 1
;customFunctions = function1 function2
;customFunctions = Package::func1 Package::func2
; CROSS-DOMAIN
; If you have some handlers that are not registered on the main domain,
; uncomment this
;cda = 1
; SAFE JAIL
; Uncomment this to disable Safe jail.
; Warning: this can allow malicious code in custom functions or rules
;useSafeJail = 0
; LOGGING
;
; 1 - Defined logging level
; Set here one of error, warn, notice, info or debug
logLevel=debug
logger = Lemonldap::NG::Common::Logger::Std
; Note that this has no effect for Apache2 logging: Apache LogLevel is used
; instead
;
; 2 - Change logger
;
; By default, logging is set to:
; - Lemonldap::NG::Common::Logger::Apache2 for ApacheMP2 handlers
; - Lemonldap::NG::Common::Logger::Syslog for FastCGI (Nginx)
; - Lemonldap::NG::Common::Logger::Std for PSGI applications (manager,
; portal,...) when they are not
; launched by FastCGI server
; Other loggers availables:
; - Lemonldap::NG::Common::Logger::Log4perl to use Log4perl
;
; "Std" is redirected to the web server logs for Apache. For Nginx, only if
; request failed
;
; You can overload this in this section (for all) or in another section if
; you want to change logger for a specified app.
;
; LLNG uses 2 loggers: 1 for technical logs (logger), 1 for user actions
; (userLogger). "userLogger" uses the same class as "logger" if not set.
;logger = Lemonldap::NG::Common::Logger::Syslog
;userLogger = Lemonldap::NG::Common::Logger::Log4perl
;
; 2.1 - Using Syslog
;
; For Syslog logging, you can also overwrite facilities. Default values:
;logger = Lemonldap::NG::Common::Logger::Syslog
;syslogFacility = daemon
;syslogOptions = cons,pid,ndelay
;userSyslogFacility = auth
;userSyslogOptions = cons,pid,ndelay
;
; 2.2 - Using Log4perl
;
; If you want to use Log4perl, you can set these parameters. Here are default
; values:
;logger = Lemonldap::NG::Common::Logger::Log4perl
;log4perlConfFile = /etc/log4perl.conf
;log4perlLogger = LLNG
;log4perlUserLogger = LLNG.user
;
; Here, Log4perl configuration is read from /etc/log4perl.conf. The "LLNG"
; value points to the logger class. Example:
; log4perl.logger.LLNG = WARN, File1
; log4perl.logger.LLNG.user = INFO, File2
; ...
; CONFIGURATION CHECK
;
; LLNG verify configuration at server start. If you use "reload" mechanism,
; local cache will be updated. Configuration is checked locally every
; 10 minutes by each LLNG component. You can change this value using
; `checkTime` (time in seconds).
; To increase performances, you should comment this parameter and rely on cache.
checkTime = 1
[configuration]
; confTimeout: maximum time to get configuration (default 10)
;confTimeout = 5
; GLOBAL CONFIGURATION ACCESS TYPE
; (File, REST, SOAP, CDBI/RDBI, LDAP, YAMLFile)
; Set here the parameters needed to access to LemonLDAP::NG configuration.
; You have to set "type" to one of the followings :
;
; * File/YAMLFile: you have to set 'dirName' parameter. Example:
;
; type = File ; or type = YAMLFile
; dirName = /var/lib/lemonldap-ng/conf
; ; Optimize JSON for readability instead of performance
; prettyPrint = 1
;
; * CDBI/RDBI : you have to set 'dbiChain' (required) and 'dbiUser' and 'dbiPassword'
; if needed. Example:
;
; type = CDBI
; ;type = RDBI
; dbiChain = DBI:MariaDB:database=lemonldap-ng;host=1.2.3.4
; dbiUser = lemonldap
; dbiPassword = password
;
; * REST: REST configuration access is a sort of proxy: the portal is
; configured to use the real session storage type (DBI or File for
; example).
; You have to set 'baseUrl' parameter. Example:
;
; type = REST
; baseUrl = https://auth.example.com/config
; proxyOptions = { timeout => 5 }
; User = lemonldap
; Password = mypassword
;
; * SOAP: SOAP configuration access is a sort of proxy: the portal is
; configured to use the real session storage type (DBI or File for
; example).
; You have to set 'proxy' parameter. Example:
;
; type = SOAP
; proxy = https://auth.example.com/config
; proxyOptions = { timeout => 5 }
; User = lemonldap
; Password = mypassword
;
; * LDAP: you have to set ldapServer, ldapConfBase, ldapBindDN and ldapBindPassword.
;
; type = LDAP
; ldapServer = ldap://localhost
; ldapConfBase = ou=conf,ou=applications,dc=example,dc=com
; ldapBindDN = cn=manager,dc=example,dc=com
; ldapBindPassword = secret
; ldapObjectClass = applicationProcess
; ldapAttributeId = cn
; ldapAttributeContent = description
type=File
dirName = /var/lib/lemonldap-ng/conf
; Optimize for readability instead of performance
prettyPrint = 1
; LOCAL CACHE CONFIGURATION
;
; To increase performances, use a local cache for the configuration. You have
; to choose a Cache::Cache module and set its parameters. Example:
;
; localStorage = Cache::FileCache
; localStorageOptions={ \
; 'namespace' => 'lemonldap-ng-config',\
; 'default_expires_in' => 600, \
; 'directory_umask' => '007', \
; 'cache_root' => '/var/cache/lemonldap-ng', \
; 'cache_depth' => 3, \
; }
localStorage=Cache::FileCache
localStorageOptions={ \
'namespace' => 'lemonldap-ng-config',\
'default_expires_in' => 600, \
'directory_umask' => '007', \
'cache_root' => '/var/cache/lemonldap-ng', \
'cache_depth' => 3, \
}
[portal]
; PORTAL CUSTOMIZATION
; I - Required parameters
; staticPrefix: relative (or URL) location of static HTML components
staticPrefix = /static
; location of HTML templates directory
templateDir = /usr/share/lemonldap-ng/portal/templates
; languages: available languages for portal interface
languages = en, fr, vi, it, ar, de, fi, tr, pl, zh_TW, es
; II - Optional parameters (overwrite configuration)
; Name of the skin
;portalSkin = pastel
; Modules displayed
;portalDisplayLogout = 1
;portalDisplayResetPassword = 1
;portalDisplayChangePassword = 1
;portalDisplayAppslist = 1
;portalDisplayLoginHistory = 1
; Require the old password when changing password
;portalRequireOldPassword = 1
; Attribute displayed as connected user
;portalUserAttr = mail
; Old menu HTML code
; Enable it if you use old templates
;useOldMenuItems=1
; Override error codes
;error_0 = You are well authenticated!
; Custom template parameters
; For example to use <TMPL_VAR NAME="myparam">
;tpl_myparam = test
; COMBINATION FORMS
; If you want to fix forms to display, you can use this;
;combinationForms = standardform, yubikeyform
;syslog = auth
; SOAP FUNCTIONS
; Remove comment to activate SOAP Functions getCookies(user,pwd) and
; error(language, code)
;Soap = 1
; Note that getAttibutes() will be activated but on a different URI
; (http://auth.example.com/sessions)
; You can also restrict attributes and macros exported by getAttributes
;exportedAttr = uid mail
; PASSWORD POLICY
; Remove comment to use LDAP Password Policy
;ldapPpolicyControl = 1
; Remove comment to store password in session (use with caution)
;storePassword = 1
; Remove comment to use LDAP modify password extension
; (beware of compatibility with LDAP Password Policy)
;ldapSetPassword = 1
; RESET PASSWORD BY MAIL
; SMTP server (default to localhost), set to '' to use default mail service
;SMTPServer = localhost
; SMTP auth user
;SMTPAuthUser = toto
; SMTP auth password
;SMTPAuthPass = secret
; Mail From address
;mailFrom = [email protected]
; Reply To
;mailReplyTo = [email protected]
; Mail confirmation URL
;mailUrl = http://reset.example.com
; Mail subject for confirmation message
;mailConfirmSubject = [LemonLDAP::NG] Password reset confirmation
; Mail body for confiramtion (can use $url for confirmation URL, and other session
; infos, like $cn). Keep comment to use HTML templates
;mailConfirmBody = Hello $cn,\n\nClick here to receive your new password: $url
; Mail subject for new password message
;mailSubject = [LemonLDAP::NG] Your new password
; Mail body for new password (can use $password for generated password, and other session
; infos, like $cn). Keep comment to use HTML templates
;mailBody = Hello $cn,\n\nYour new password is $password
; LDAP filter to use
;mailLDAPFilter = '(&(mail=$mail)(objectClass=inetOrgPerson))'
; Random regexp for password generation
;randomPasswordRegexp = [A-Z]{3}[a-z]{5}.\d{2}
; LDAP GROUPS
; Set the base DN of your groups branch
;ldapGroupBase = ou=groups,dc=example,dc=com
; Objectclass used by groups
;ldapGroupObjectClass = groupOfUniqueNames
; Attribute used by groups to store member
;ldapGroupAttributeName = uniqueMember
; Attribute used by user to link to groups
;ldapGroupAttributeNameUser = dn
; Attribute used to identify a group. The group will be displayed as
; cn|mail|status, where cn, mail and status will be replaced by their
; values.
;ldapGroupAttributeNameSearch = cn mail
; NOTIFICATIONS SERVICE
; Use it to be able to notify messages during authentication
;notification = 1
; Note that the SOAP function newNotification will be activated on
; http://auth.example.com/notification
; If you want to hide this, just protect "/index.fcgi/notification" in
; your Apache configuration file
; XSS protection bypass
; By default, the portal refuses redirections that come from sites not
; registered in the configuration (manager) except for those coming
; from trusted domains. By default, trustedDomains contains the domain
; declared in the manager. You can set trustedDomains to empty value so
; that, undeclared sites will be rejected. You can also set here a list
; of trusted domains or hosts separated by spaces. This is usefull if
; your website use LemonLDAP::NG without handler with SOAP functions.
;trustedDomains = my.trusted.host example2.com
; Check XSS
; Set to 0 to disable error on XSS attack detection
;checkXSS = 0
; pdata cookie domain
; pdata cookie could not be sent with cross domains AJAX request
; Null is default value
;pdataDomain = example.com
; CUSTOM PLUGINS
; If you want to add custom plugins, set list here (comma separated)
; Read Lemonldap::NG::Portal::Main::Plugin(3pm) man page.
;customPlugins = ::My::Package1, ::My::Package2
; To avoid bad/expired OTT if "authssl" and "auth" are served by different Load Balancers
; you can override OTT configuration to store Upgrade or Issuer OTT into global storage
;forceGlobalStorageUpgradeOTT = 1
;forceGlobalStorageIssuerOTT = 1
[handler]
; Handler cache configuration
; You can overwrite here local session cache settings in manager:
; localSessionStorage=Cache::FileCache
; localSessionStorageOptions={ \
; 'namespace' => 'lemonldap-ng-sessions', \
; 'default_expires_in' => 600, \
; 'directory_umask' => '007', \
; 'cache_root' => '/var/cache/lemonldap-ng', \
; 'cache_depth' => 3, \
; }
; Set https to 1 if your handler protect a https website (used only for
; redirections to the portal)
;https = 0
; Set port if your your hanlder protect a website on a non standard port
; - 80 for http, 443 for https (used only for redirections to the portal)
;port = 8080
; Set status to 1 if you want to have the report of activity (used for
; example to inform MRTG)
status = 0
; Set useRedirectOnForbidden to 1 if you want to use REDIRECT and not FORBIDDEN
; when a user is not allowed by Handler
;useRedirectOnForbidden = 1
; Hide LemonLDAP::NG Handler in Apache Server Signature
;hideSignature = 1
; Set ServiceToken timeout
;handlerServiceTokenTTL = 30
; Set Impersonation/ContextSwitching prefix
; impersonationPrefix = real_
useRedirectOnError = 1
; Zimbra Handler parameters
;zimbraPreAuthKey = XXXX
;zimbraAccountKey = uid
;zimbraBy =id
;zimbraUrl = /service/preauth
;zimbraSsoUrl = ^/zimbrasso$
[manager]
; Manager protection: by default, the manager is protected by a demo account.
; You can protect it :
; * by Apache itself,
; * by the parameter 'protection' which can take one of the following
; values :
; * authenticate : all authenticated users can access
; * manager : manager is protected like other virtual hosts: you
; have to set rules in the corresponding virtual host
; * <rule> : you can set here directly the rule to apply
; * none : no protection
protection = manager
; staticPrefix: relative (or URL) location of static HTML components
staticPrefix = /static
;
; instanceName: Display current LLNG instance into Manager
;instanceName = Demo
; location of HTML templates directory
templateDir = /usr/share/lemonldap-ng/manager/htdocs/templates
; languages: available languages for manager interface
languages = en, fr, it, vi, ar, tr, pl, zh_TW, es
; Manager modules enabled
; Set here the list of modules you want to see in manager interface
; The first will be used as default module displayed
;enabledModules = conf, sessions, notifications, 2ndFA, viewer
enabledModules = conf, sessions, notifications, 2ndFA
; To avoid restricted users to edit configuration, defaulModule MUST be different than 'conf'
; 'conf' is set by default
;defaultModule = viewer
; Viewer module allows us to edit configuration in read-only mode
; Options can be set with specific rules like this :
;viewerAllowBrowser = $uid eq 'dwho'
;viewerAllowDiff = $uid ne 'dwho'
;
; Viewer options - Default values
;viewerHiddenKeys = samlIDPMetaDataNodes samlSPMetaDataNodes managerPassword ManagerDn globalStorageOptions persistentStorageOptions
;viewerAllowBrowser = 0
;viewerAllowDiff = 0
;[node-handler]
;
;This section is for node-lemonldap-ng-handler
;nodeVhosts = test3.example.com, test4.example.com
/var/lib/lemonldap-ng/conf/lmConf-1.json
{
"applicationList" : {
"1sample" : {
"catname" : "Sample applications",
"test1" : {
"options" : {
"description" : "A simple application displaying authenticated user",
"display" : "auto",
"logo" : "demo.png",
"name" : "Application Test 1",
"uri" : "http://test1.example.com/"
},
"type" : "application"
},
"test2" : {
"options" : {
"description" : "The same simple application displaying authenticated user",
"display" : "auto",
"logo" : "thumbnail.png",
"name" : "Application Test 2",
"uri" : "http://test2.example.com/"
},
"type" : "application"
},
"type" : "category"
},
"2administration" : {
"catname" : "Administration",
"manager" : {
"options" : {
"description" : "Configure LemonLDAP::NG WebSSO",
"display" : "auto",
"logo" : "configure.png",
"name" : "WebSSO Manager",
"uri" : "http://manager.example.com/manager.html"
},
"type" : "application"
},
"notifications" : {
"options" : {
"description" : "Explore WebSSO notifications",
"display" : "auto",
"logo" : "database.png",
"name" : "Notifications explorer",
"uri" : "http://manager.example.com/notifications.html"
},
"type" : "application"
},
"sessions" : {
"options" : {
"description" : "Explore WebSSO sessions",
"display" : "auto",
"logo" : "database.png",
"name" : "Sessions explorer",
"uri" : "http://manager.example.com/sessions.html"
},
"type" : "application"
},
"type" : "category"
},
"3documentation" : {
"catname" : "Documentation",
"localdoc" : {
"options" : {
"description" : "Documentation supplied with LemonLDAP::NG",
"display" : "on",
"logo" : "help.png",
"name" : "Local documentation",
"uri" : "http://manager.example.com/doc/"
},
"type" : "application"
},
"officialwebsite" : {
"options" : {
"description" : "Official LemonLDAP::NG Website",
"display" : "on",
"logo" : "network.png",
"name" : "Official Website",
"uri" : "http://lemonldap-ng.org/"
},
"type" : "application"
},
"type" : "category"
}
},
"authentication" : "Demo",
"cfgAuthor" : "The LemonLDAP::NG team",
"cfgNum" : 1,
"cfgVersion" : "2.0.12",
"cookieName" : "lemonldap",
"demoExportedVars" : {
"cn" : "cn",
"mail" : "mail",
"uid" : "uid"
},
"domain" : "example.com",
"exportedHeaders" : {
"test1.example.com" : {
"Auth-Groups" : "$groups",
"Auth-User" : "$uid"
},
"test2.example.com" : {
"Auth-Groups" : "$groups",
"Auth-User" : "$uid"
}
},
"exportedVars" : {},
"globalStorage" : "Apache::Session::File",
"globalStorageOptions" : {
"Directory" : "/var/lib/lemonldap-ng/sessions",
"LockDirectory" : "/var/lib/lemonldap-ng/sessions/lock",
"generateModule" : "Lemonldap::NG::Common::Apache::Session::Generate::SHA256"
},
"groups" : {},
"localSessionStorage" : "Cache::FileCache",
"localSessionStorageOptions" : {
"cache_depth" : 3,
"cache_root" : "/var/cache/lemonldap-ng",
"default_expires_in" : 600,
"directory_umask" : "007",
"namespace" : "lemonldap-ng-sessions"
},
"locationRules" : {
"auth.example.com" : {
"(?#checkUser)^/checkuser" : "inGroup(\"timelords\")",
"(?#errors)^/lmerror/" : "accept",
"default" : "accept"
},
"manager.example.com" : {
"(?#Configuration)^/(.*?\\.(fcgi|psgi)/)?(manager\\.html|confs|prx/|$)" : "inGroup(\"timelords\")",
"(?#Notifications)/(.*?\\.(fcgi|psgi)/)?notifications" : "inGroup(\"timelords\") or $uid eq \"rtyler\"",
"(?#Sessions)/(.*?\\.(fcgi|psgi)/)?sessions" : "inGroup(\"timelords\") or $uid eq \"rtyler\"",
"default" : "inGroup(\"timelords\") or $uid eq \"rtyler\""
},
"test1.example.com" : {
"^/logout" : "logout_sso",
"default" : "accept"
},
"test2.example.com" : {
"^/logout" : "logout_sso",
"default" : "accept"
}
},
"loginHistoryEnabled" : 1,
"macros" : {
"UA" : "$ENV{HTTP_USER_AGENT}",
"_whatToTrace" : "$_auth eq 'SAML' ? lc($_user.'@'.$_idpConfKey) : $_auth eq 'OpenIDConnect' ? lc($_user.'@'.$_oidc_OP) : lc($_user)"
},
"mailUrl" : "http://auth.example.com/resetpwd",
"notification" : 1,
"notificationStorage" : "File",
"notificationStorageOptions" : {
"dirName" : "/var/lib/lemonldap-ng/notifications"
},
"passwordDB" : "Demo",
"persistentStorage" : "Apache::Session::File",
"persistentStorageOptions" : {
"Directory" : "/var/lib/lemonldap-ng/psessions",
"LockDirectory" : "/var/lib/lemonldap-ng/psessions/lock"
},
"portal" : "http://auth.example.com/",
"portalSkin" : "bootstrap",
"portalSkinBackground" : "1280px-Cedar_Breaks_National_Monument_partially.jpg",
"registerDB" : "Demo",
"registerUrl" : "http://auth.example.com/register",
"reloadUrls" : {
"localhost" : "http://reload.example.com/reload"
},
"securedCookie" : 0,
"sessionDataToRemember" : {},
"timeout" : 72000,
"userDB" : "Same",
"whatToTrace" : "_whatToTrace"
}