Description
Is this related to a new or existing framework?
React
Is this related to a new or existing API?
Authentication
Is this related to another service?
No response
Describe the feature you'd like to request
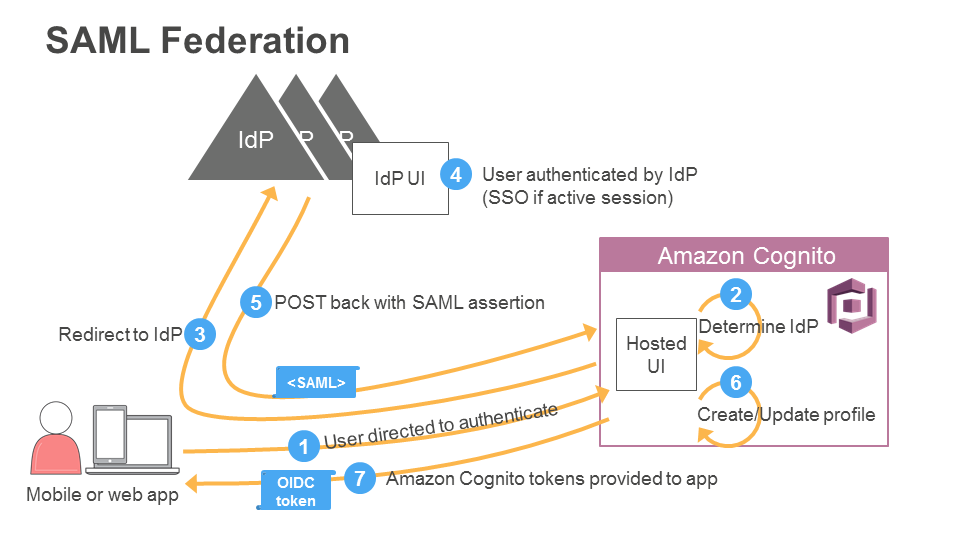
Cognito User Pools federated identities supports using identifiers (typically a domain name) to correctly figure out what IdP a user should be authenticating with based on their email address. This is described in the Cognito documentation here.
You can also choose identifiers for your SAML providers. An identifier uniquely resolves to an identity provider (IdP) associated with your user pool. Typically, each identifier corresponds to an organization domain that the SAML IdP represents. For a multi-tenant app that multiple organizations share, you can use identifiers to redirect users to the correct IdP. Because the same organization can own multiple domains, you can provide multiple identifiers. To sign in your users with an identifier, direct their sessions to the Authorize endpoint for your app client with an idp_identifier parameter.
Following the link, you can see that the /oauth2/authorize endpoint supports an optional idp_identifier query parameter for providing this information.
I would like to be able to use the Auth.federatedSignIn function to be able to utilize this functionality.
Currently Amplify applications utilizing multiple identify providers need to jump through some awkward hoops to get their authentication code working correctly, but Cognito already supports the required functionality.
Describe the solution you'd like
Currently the Auth package provides a federatedSignIn function that has a required provider. I would like to see this function's input type enhanced to something like the following.
export declare type FederatedSignInOptions = {
provider?: CognitoHostedUIIdentityProvider;
idpIdentifier?: string;
customState?: string;
};Maybe something a little smarter to require either provider or idpIdentifier; my TypeScript isn't that good.
This would allow one to do something like,
Auth.federatedSignIn({ idpIdentifier: "example.com" });and have the user be directed to their correct IdP to authenticate.
Describe alternatives you've considered
I've tried to see if it would be possible to abuse the current behavior to make this work, but you can see here that there's currently no way to provide additional query parameters to make this request work.
Additional context
The documentation here has a handy graphical overview of the workflow.
Is this something that you'd be interested in working on?
- 👋 I may be able to implement this feature request
-
⚠️ This feature might incur a breaking change