diff --git a/.github/linters/.markdown-lint.yaml b/.github/linters/.markdown-lint.yaml
new file mode 100644
index 0000000000..2988b78110
--- /dev/null
+++ b/.github/linters/.markdown-lint.yaml
@@ -0,0 +1,15 @@
+---
+extends: "markdownlint/style/prettier"
+
+MD010:
+ code_blocks: false
+
+MD013: false
+
+MD024:
+ siblings_only: true
+ allow_different_nesting: true
+
+MD033:
+ allowed_elements:
+ - img
diff --git a/.github/workflows/linter.yml b/.github/workflows/linter.yml
index f2db214f82..c49f9c09c5 100644
--- a/.github/workflows/linter.yml
+++ b/.github/workflows/linter.yml
@@ -44,10 +44,6 @@ jobs:
run: |
echo "::add-matcher::.github/workflows/matchers/yamllint.json"
- - name: Remove part of the doc
- run: |
- rm -rf docs/src/
-
- name: Lint everything else
uses: super-linter/super-linter/slim@v6.1.1
if: always()
diff --git a/README.md b/README.md
index b76cffdd2a..67c3757c8b 100644
--- a/README.md
+++ b/README.md
@@ -10,7 +10,7 @@
> Join the Empire Hacking Slack
>
> [](https://slack.empirehacking.nyc/)
-> > - Discussions and Support
+> > _\- Discussions and Support_
**Slither** is a Solidity & Vyper static analysis framework written in Python3. It runs a suite of vulnerability detectors, prints visual information about contract details, and provides an API to easily write custom analyses. Slither enables developers to find vulnerabilities, enhance their code comprehension, and quickly prototype custom analyses.
@@ -66,7 +66,7 @@ slither tests/uninitialized.sol
## How to install
-> **Note**
+> **Note**
> Slither requires Python 3.8+.
If you're **not** going to use one of the [supported compilation frameworks](https://github.com/crytic/crytic-compile), you need [solc](https://github.com/ethereum/solidity/), the Solidity compiler; we recommend using [solc-select](https://github.com/crytic/solc-select) to conveniently switch between solc versions.
diff --git a/docs/src/SUMMARY.md b/docs/src/SUMMARY.md
index 44e7023976..5809dbe720 100644
--- a/docs/src/SUMMARY.md
+++ b/docs/src/SUMMARY.md
@@ -1,3 +1,5 @@
+# Summary
+
- [Introduction](./README.md)
- [Usage](./Usage.md)
- [API](./api/README.md)
diff --git a/docs/src/Usage.md b/docs/src/Usage.md
index 8b08099f16..4c4dc58eed 100644
--- a/docs/src/Usage.md
+++ b/docs/src/Usage.md
@@ -1,4 +1,4 @@
-## Usage
+# Usage
- [How to run Slither](#how-to-run-slither)
- [Foundry/Hardhat](#foundryhardhat)
@@ -11,7 +11,7 @@
- [Path Filtering](#path-filtering)
- [Triage mode](#triage-mode)
- [Configuration file](#configuration-file)
-- [IDE integrations](#ide-integration)
+- [IDE integrations](#ide-integrations)
## How to run Slither
@@ -21,7 +21,7 @@ All the [`crytic-compile`](https://github.com/crytic/crytic-compile/wiki/Configu
To run Slither on a Foundry/hardhat directory:
-```
+```sh
slither .
```
@@ -29,7 +29,7 @@ slither .
To run Slither from a Solidity file:
-```
+```sh
slither file.sol
```
@@ -37,25 +37,31 @@ slither file.sol
To run Slither from a contract hosted on Etherscan, run
-```
+```sh
slither 0x7F37f78cBD74481E593F9C737776F7113d76B315
```
+### AST File
+
+This section is work in progress
+
We recommend installing [solc-select](https://github.com/crytic/solc-select/) so Slither can switch to the expected solc version automatically.
+## Options
+
### Detector selection
Slither runs all its detectors by default.
To run only selected detectors, use `--detect detector1,detector2`. For example:
-```
+```sh
slither file.sol --detect arbitrary-send,pragma
```
To exclude detectors, use `--exclude detector1,detector2`. For example:
-```
+```sh
slither file.sol --exclude naming-convention,unused-state,suicidal
```
@@ -69,7 +75,7 @@ By default, no printers are run.
To run selected printers, use `--print printer1,printer2`. For example:
-```
+```sh
slither file.sol --print inheritance-graph
```
@@ -81,20 +87,18 @@ slither file.sol --print inheritance-graph
Examples:
-```
+```sh
slither . --filter-paths "openzepellin"
```
Filter all the results only related to openzepellin.
-```
+```sh
slither . --filter-paths "Migrations.sol|ConvertLib.sol"
```
Filter all the results only related to the file `SafeMath.sol` or `ConvertLib.sol`.
-### Triage mode
-
Slither offers two ways to remove results:
- By adding `//slither-disable-next-line DETECTOR_NAME` before the issue
@@ -108,7 +112,7 @@ Slither offers two ways to remove results:
Examples:
-```
+```sh
slither . --triage-mode
[...]
0: C.destination (test.sol#3) is never initialized. It is used in:
@@ -130,7 +134,7 @@ Options passed via the CLI have priority over options set in the configuration f
The following flags are supported:
-```
+```sh
{
"detectors_to_run": "all",
"printers_to_run": None,
@@ -168,3 +172,7 @@ The following flags are supported:
```
For flags related to the compilation, see the [`crytic-compile` configuration](https://github.com/crytic/crytic-compile/blob/master/crytic_compile/cryticparser/defaults.py)
+
+## IDE integrations
+
+This section is work in progress
diff --git a/docs/src/api/Data-dependency.md b/docs/src/api/Data-dependency.md
index 6eb0a35c87..03add0edcb 100644
--- a/docs/src/api/Data-dependency.md
+++ b/docs/src/api/Data-dependency.md
@@ -37,7 +37,7 @@ If we consider the contract entirely (with all the functions), we have:
As a result, in our previous example, `is_dependent(b, a, funcA)` will return `False`, while `is_dependent(b, a, myContract)` will return `True`:
-```
+```python
from slither import Slither
from slither.analyses import is_dependent
diff --git a/docs/src/api/JSON-output.md b/docs/src/api/JSON-output.md
index bee991ba47..e7f45e793b 100644
--- a/docs/src/api/JSON-output.md
+++ b/docs/src/api/JSON-output.md
@@ -1,3 +1,5 @@
+# JSON Output
+
- [Top-level Command Output](https://github.com/crytic/slither/wiki/JSON-output#top-level-command-output): Standard top-level (for detectors, printers and tools)
- [Detectors output](https://github.com/crytic/slither/wiki/JSON-output#detector-results)
- [Upgradeability output](https://github.com/crytic/slither/wiki/JSON-output#slither-check-upgradeability)
@@ -36,7 +38,7 @@ The underlying `results` item above will appear in the following format:
A detector result found in the `detectors` array above will be of the following format:
-```
+```json
{
"check": "...",
"impact": "...",
@@ -92,7 +94,7 @@ Each element found in `elements` above is of the form:
Each `source_mapping` object is used to map an element to some portion of source. It is of the form:
-```
+```json
"source_mapping": {
"start": 45
"length": 58,
@@ -165,7 +167,7 @@ The `slither-check-upgradeability` tool also produces JSON output (with the use
- `error` (string | null): If `success` is `false`, this will be a string with relevant error information. Otherwise, it will be `null`.
- `results` (upgradeability-check-results, see below): If `success` is `true`, this will contain an `upgradeability-check` object populated with the different upgradeability checks. If `success` is `false`, `upgradeability-check` object will be empty.
-## Command Results
+## Upgradeability Check Results
The underlying `upgradeability-check` item above will appear in the following format:
diff --git a/docs/src/api/README.md b/docs/src/api/README.md
index 62e67fc49c..5990cb5f54 100644
--- a/docs/src/api/README.md
+++ b/docs/src/api/README.md
@@ -1,3 +1,5 @@
+# Slither API
+
Slither is fully customizable:
- [Static Analysis](./static_analysis.md): learn about the basics of static analysis
diff --git a/docs/src/api/SlithIR-SSA.md b/docs/src/api/SlithIR-SSA.md
index 50f3f4b4ed..50915f9d48 100644
--- a/docs/src/api/SlithIR-SSA.md
+++ b/docs/src/api/SlithIR-SSA.md
@@ -1,4 +1,4 @@
-## SSA
+# SSA
Slither possess a Static Single Assignment (SSA) form representation of SlithIR. SSA is a commonly used representation in compilation and static analysis in general. It requires that each variable is assigned at least one time. SSA is a key component for building an efficient data-dependency analysis.
diff --git a/docs/src/api/SlithIR.md b/docs/src/api/SlithIR.md
index e345ff082f..de21f49291 100644
--- a/docs/src/api/SlithIR.md
+++ b/docs/src/api/SlithIR.md
@@ -20,7 +20,7 @@ Additionally, Slither can include non-trivial variable tracking by default by tr
`$ slither file.sol --print slithir` will output the IR for every function.
-```
+```sh
$ slither examples/printers/slihtir.sol --printers slithir
Contract UnsafeMath
Function add(uint256,uint256)
@@ -49,9 +49,9 @@ Contract MyContract
REF_3 := TMP_1
```
-# SlithIR Specification
+## SlithIR Specification
-## Variables
+### Variables
- `StateVariable`
- `LocalVariable`
@@ -66,18 +66,18 @@ In the following we use:
- `LVALUE` can be: `StateVariable`, `LocalVariable`, `TemporaryVariable`, `ReferenceVariable` or `TupleVariable`
- `RVALUE` can be: `StateVariable`, `LocalVariable`, `Constant`, `SolidityVariable`, `TemporaryVariable` or `ReferenceVariable`
-## Operators
+### Operators
- All the operators inherit from `Operation` and have a `read` attribute returning the list of variables read (see [slither/slithir/operations/operation.py](https://github.com/crytic/slither/blob/master/slither/slithir/operations/operation.py)).
- All the operators writing to a `LVALUE` inherit from `OperationWithLValue` and have the `lvalue` attribute (see [slither/slithir/operations/lvalue.py](https://github.com/crytic/slither/blob/master/slither/slithir/operations/lvalue.py)).
-### Assignment
+#### Assignment
- `LVALUE := RVALUE`
- `LVALUE := Tuple`
- `LVALUE := Function` (for dynamic function)
-### Binary Operation
+#### Binary Operation
- `LVALUE = RVALUE ** RVALUE`
- `LVALUE = RVALUE * RVALUE`
@@ -99,18 +99,18 @@ In the following we use:
- `LVALUE = RVALUE && RVALUE`
- `LVALUE = RVALUE -- RVALUE`
-### Unary Operation
+#### Unary Operation
- `LVALUE = ! RVALUE`
- `LVALUE = ~ RVALUE`
-### Index
+#### Index
- `REFERENCE -> LVALUE [ RVALUE ]`
Note: The reference points to the memory location
-### Member
+#### Member
- `REFERENCE -> LVALUE . RVALUE`
- `REFERENCE -> CONTRACT . RVALUE`
@@ -118,7 +118,7 @@ Note: The reference points to the memory location
Note: The reference points to the memory location
-### New Operators
+#### New Operators
- `LVALUE = NEW_ARRAY ARRAY_TYPE DEPTH(:int)`
@@ -132,32 +132,32 @@ Note: The reference points to the memory location
`ELEMENTARY_TYPE` is defined in [slither/core/solidity_types/elementary_type.py](https://github.com/crytic/slither/blob/master/slither/core/solidity_types/elementary_type.py)
-### Push Operator
+#### Push Operator
- `PUSH LVALUE RVALUE`
- `PUSH LVALUE Function` (for dynamic function)
-### Delete Operator
+#### Delete Operator
- `DELETE LVALUE`
-### Conversion
+#### Conversion
- `CONVERT LVALUE RVALUE TYPE`
TYPE is a [solidity_types](https://github.com/crytic/slither/tree/master/slither/core/solidity_types)
-### Unpack
+#### Unpack
- `LVALUE = UNPACK TUPLEVARIABLE INDEX(:int)`
-### Array Initialization
+#### Array Initialization
- `LVALUE = INIT_VALUES`
`INIT_VALUES` is a list of `RVALUE`, or a list of lists in case of a multidimensional array.
-### Calls Operators
+#### Calls Operators
In the following, `ARG` is a variable as defined in [SlithIR#variables](https://github.com/crytic/slither/wiki/SlithIR#variables)
@@ -186,7 +186,7 @@ Optional arguments:
- `GAS` and `VALUE` for `HIGH_LEVEL_CALL` / `LOW_LEVEL_CALL`.
-### Return
+#### Return
- `RETURN RVALUE`
- `RETURN TUPLE`
@@ -194,7 +194,7 @@ Optional arguments:
`Return None` represents an empty return statement.
-### Condition
+#### Condition
- `CONDITION RVALUE`
diff --git a/docs/src/api/static_analysis.md b/docs/src/api/static_analysis.md
index 6c8f86b668..5d19892b59 100644
--- a/docs/src/api/static_analysis.md
+++ b/docs/src/api/static_analysis.md
@@ -1,4 +1,4 @@
-## Static analysis
+# Static analysis
The capabilities and design of the Slither static analysis framework have been described in blog posts ([1](https://blog.trailofbits.com/2018/10/19/slither-a-solidity-static-analysis-framework/), [2](https://blog.trailofbits.com/2019/05/27/slither-the-leading-static-analyzer-for-smart-contracts/)) and an [academic paper](https://github.com/trailofbits/publications/blob/master/papers/wetseb19.pdf).
@@ -10,7 +10,7 @@ In this article, we will not provide an exhaustive review of static analysis tec
- [Code analysis](#analysis)
- [Intermediate representation](#intermediate-representation)
-### Code representation
+## Code representation
Unlike dynamic analysis, which reasons about a single execution path, static analysis reasons about all paths at once. To do so, it relies on a different code representation. The two most common ones are the abstract syntax tree (AST) and the control flow graph (CFG).
diff --git a/docs/src/detectors/Adding-a-new-detector.md b/docs/src/detectors/Adding-a-new-detector.md
index abc35fc047..3ebee2f320 100644
--- a/docs/src/detectors/Adding-a-new-detector.md
+++ b/docs/src/detectors/Adding-a-new-detector.md
@@ -1,3 +1,5 @@
+# Adding New Detectors
+
Slither's plugin architecture lets you integrate new detectors that run from the command-line.
## Detector Skeleton
diff --git a/docs/src/detectors/Detector-Documentation.md b/docs/src/detectors/Detector-Documentation.md
index 41990962f8..aa23d81c77 100644
--- a/docs/src/detectors/Detector-Documentation.md
+++ b/docs/src/detectors/Detector-Documentation.md
@@ -14,7 +14,7 @@ List of public detectors
`solc` versions `0.4.7`-`0.5.9` contain a [compiler bug](https://blog.ethereum.org/2019/06/25/solidity-storage-array-bugs) leading to incorrect ABI encoder usage.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract A {
@@ -45,7 +45,7 @@ Use a compiler >= `0.5.10`.
Detect when `msg.sender` is not used as `from` in transferFrom.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
function a(address from, address to, uint256 amount) public {
@@ -71,7 +71,7 @@ Use `msg.sender` as `from` in transferFrom.
Detect arrays passed to a function that expects reference to a storage array
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Memory {
@@ -111,7 +111,7 @@ Ensure the correct usage of `memory` and `storage` in the function parameters. M
Detect collision due to dynamic type usages in `abi.encodePacked`
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Sign {
@@ -130,7 +130,7 @@ Do not use more than one dynamic type in `abi.encodePacked()`
(see the [Solidity documentation](https://solidity.readthedocs.io/en/v0.5.10/abi-spec.html?highlight=abi.encodePacked#non-standard-packed-modeDynamic)).
Use `abi.encode()`, preferably.
-## Incorrect shift in assembly.
+## Incorrect shift in assembly
### Configuration
@@ -142,7 +142,7 @@ Use `abi.encode()`, preferably.
Detect if the values in a shift operation are reversed
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract C {
@@ -172,7 +172,7 @@ Swap the order of parameters.
Detect multiple constructor definitions in the same contract (using new and old schemes).
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract A {
@@ -209,7 +209,7 @@ Only declare one constructor, preferably using the new scheme `constructor(...)`
If a codebase has two contracts the similar names, the compilation artifacts
will not contain one of the contracts with the duplicate name.
-### Exploit Scenario:
+### Exploit Scenario
Bob's `truffle` codebase has two contracts named `ERC20`.
When `truffle compile` runs, only one of the two contracts will generate artifacts in `build/contracts`.
@@ -231,7 +231,7 @@ Rename the contract.
Detect unprotected variable that are marked protected
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Buggy{
@@ -267,7 +267,7 @@ Add access controls to the vulnerable function
Prior to Solidity 0.5, a public mapping with nested structures returned [incorrect values](https://github.com/ethereum/solidity/issues/5520).
-### Exploit Scenario:
+### Exploit Scenario
Bob interacts with a contract that has a public mapping with nested structures. The values returned by the mapping are incorrect, breaking Bob's usage
@@ -287,7 +287,7 @@ Do not use public mapping with nested structures.
An attacker can manipulate the logic of the contract by using a right-to-left-override character (`U+202E)`.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Token
@@ -331,7 +331,7 @@ Special control characters must not be allowed.
Detection of state variables shadowed.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract BaseContract{
@@ -375,7 +375,7 @@ Remove the state variable shadowing.
Unprotected call to a function executing `selfdestruct`/`suicide`.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Suicidal{
@@ -403,7 +403,7 @@ Protect access to all sensitive functions.
Uninitialized state variables.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Uninitialized{
@@ -433,7 +433,7 @@ Initialize all the variables. If a variable is meant to be initialized to zero,
An uninitialized storage variable will act as a reference to the first state variable, and can override a critical variable.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Uninitialized{
@@ -468,7 +468,7 @@ Initialize all storage variables.
Detects logic contract that can be destructed.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Buggy is Initializable{
@@ -503,7 +503,7 @@ Add a constructor to ensure `initialize` cannot be called on the logic contract.
Detect when `msg.sender` is not used as `from` in transferFrom and permit is used.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
function bad(address from, uint256 value, uint256 deadline, uint8 v, bytes32 r, bytes32 s, address to) public {
@@ -530,7 +530,7 @@ Ensure that the underlying ERC20 token correctly implements a permit function.
Unprotected call to a function sending Ether to an arbitrary address.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract ArbitrarySendEth{
@@ -563,7 +563,7 @@ Ensure that an arbitrary user cannot withdraw unauthorized funds.
Detects the direct assignment of an array's length.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract A {
@@ -605,7 +605,7 @@ Otherwise, thoroughly review the contract to ensure a user-controlled variable c
`Delegatecall` or `callcode` to an address controlled by the user.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Delegatecall{
@@ -633,7 +633,7 @@ Avoid using `delegatecall`. Use only trusted destinations.
Detect the use of `delegatecall` inside a loop in a payable function.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract DelegatecallInLoop{
@@ -671,7 +671,7 @@ Carefully check that the function called by `delegatecall` is not payable/doesn'
Detect use of bitwise `xor ^` instead of exponential `**`
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Bug{
@@ -698,7 +698,7 @@ Use the correct operator `**` for exponentiation.
Detect if `return` in an assembly block halts unexpectedly the execution.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract C {
@@ -734,7 +734,7 @@ Use the `leave` statement.
Detect the use of `msg.value` inside a loop.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract MsgValueInLoop{
@@ -767,7 +767,7 @@ Provide an explicit array of amounts alongside the receivers array, and check th
Detection of the [reentrancy bug](https://github.com/trailofbits/not-so-smart-contracts/tree/master/reentrancy).
Do not report reentrancies that don't involve Ether (see `reentrancy-no-eth`)
-### Exploit Scenario:
+### Exploit Scenario
```solidity
function withdrawBalance(){
@@ -798,7 +798,7 @@ Apply the [`check-effects-interactions pattern`](http://solidity.readthedocs.io/
Detect if a `return` is used where a `leave` should be used.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract C {
@@ -830,7 +830,7 @@ Use the `leave` statement.
`solc` versions `0.4.7`-`0.5.9` contain [a compiler bug](https://blog.ethereum.org/2019/06/25/solidity-storage-array-bugs)
leading to incorrect values in signed integer arrays.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract A {
@@ -843,7 +843,7 @@ contract A {
}
```
-`bad0()` uses a (storage-allocated) signed integer array state variable to store the ether balances of three accounts.
+`bad0()` uses a (storage-allocated) signed integer array state variable to store the ether balances of three accounts.
`-1` is supposed to indicate uninitialized values but the Solidity bug makes these as `1`, which could be exploited by the accounts.
### Recommendation
@@ -862,7 +862,7 @@ Use a compiler version >= `0.5.10`.
The return value of an external transfer/transferFrom call is not checked
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Token {
@@ -896,7 +896,7 @@ Use `SafeERC20`, or ensure that the transfer/transferFrom return value is checke
Weak PRNG due to a modulo on `block.timestamp`, `now` or `blockhash`. These can be influenced by miners to some extent so they should be avoided.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Game {
@@ -928,7 +928,7 @@ Do not use `block.timestamp`, `now` or `blockhash` as a source of randomness
Use [codex](https://openai.com/blog/openai-codex/) to find vulnerabilities
-### Exploit Scenario:
+### Exploit Scenario
N/A
@@ -948,7 +948,7 @@ Review codex's message.
An ERC20 token has a function whose signature collides with EIP-2612's DOMAIN_SEPARATOR(), causing unanticipated behavior for contracts using `permit` functionality.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Contract{
@@ -974,7 +974,7 @@ Remove or rename the function that collides with DOMAIN_SEPARATOR().
Detect out-of-range `enum` conversion (`solc` < `0.4.5`).
-### Exploit Scenario:
+### Exploit Scenario
```solidity
pragma solidity 0.4.2;
@@ -1006,7 +1006,7 @@ Use a recent compiler version. If `solc` <`0.4.5` is required, check the `enum`
Incorrect return values for `ERC20` functions. A contract compiled with Solidity > 0.4.22 interacting with these functions will fail to execute them, as the return value is missing.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Token{
@@ -1033,7 +1033,7 @@ Set the appropriate return values and types for the defined `ERC20` functions.
Incorrect return values for `ERC721` functions. A contract compiled with solidity > 0.4.22 interacting with these functions will fail to execute them, as the return value is missing.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Token{
@@ -1060,7 +1060,7 @@ Set the appropriate return values and vtypes for the defined `ERC721` functions.
Use of strict equalities that can be easily manipulated by an attacker.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Crowdsale{
@@ -1088,7 +1088,7 @@ Don't use strict equality to determine if an account has enough Ether or tokens.
Contract with a `payable` function, but without a withdrawal capacity.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
pragma solidity 0.4.24;
@@ -1116,7 +1116,7 @@ Remove the payable attribute or add a withdraw function.
A deletion in a structure containing a mapping will not delete the mapping (see the [Solidity documentation](https://solidity.readthedocs.io/en/latest/types.html##delete)). The remaining data may be used to compromise the contract.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
struct BalancesStruct{
@@ -1149,7 +1149,7 @@ Use a lock mechanism instead of a deletion to disable structure containing a map
Detect when a Pyth deprecated function is used
-### Exploit Scenario:
+### Exploit Scenario
```solidity
import "@pythnetwork/pyth-sdk-solidity/IPyth.sol";
@@ -1174,7 +1174,7 @@ The function `A` uses the deprecated `getPrice` Pyth function.
### Recommendation
-Do not use deprecated Pyth functions. Visit https://api-reference.pyth.network/.
+Do not use deprecated Pyth functions. Visit [https://api-reference.pyth.network/](https://api-reference.pyth.network/).
## Pyth unchecked confidence level
@@ -1188,7 +1188,7 @@ Do not use deprecated Pyth functions. Visit https://api-reference.pyth.network/.
Detect when the confidence level of a Pyth price is not checked
-### Exploit Scenario:
+### Exploit Scenario
```solidity
import "@pythnetwork/pyth-sdk-solidity/IPyth.sol";
@@ -1212,7 +1212,7 @@ The function `A` uses the price without checking its confidence level.
### Recommendation
-Check the confidence level of a Pyth price. Visit https://docs.pyth.network/price-feeds/best-practices#confidence-intervals for more information.
+Check the confidence level of a Pyth price. Visit [pyth confidence intervals](https://docs.pyth.network/price-feeds/best-practices#confidence-intervals) for more information.
## Pyth unchecked publishTime
@@ -1226,7 +1226,7 @@ Check the confidence level of a Pyth price. Visit https://docs.pyth.network/pric
Detect when the publishTime of a Pyth price is not checked
-### Exploit Scenario:
+### Exploit Scenario
```solidity
import "@pythnetwork/pyth-sdk-solidity/IPyth.sol";
@@ -1264,7 +1264,7 @@ Check the publishTime of a Pyth price.
Detection of state variables shadowed from abstract contracts.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract BaseContract{
@@ -1294,7 +1294,7 @@ Remove the state variable shadowing.
A variable compared to itself is probably an error as it will always return `true` for `==`, `>=`, `<=` and always `false` for `<`, `>` and `!=`.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
function check(uint a) external returns(bool){
@@ -1320,7 +1320,7 @@ Remove comparison or compare to different value.
Detects expressions that are tautologies or contradictions.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract A {
@@ -1359,19 +1359,20 @@ Fix the incorrect comparison by changing the value type or the comparison.
Detects variables that are written but never read and written again.
-### Exploit Scenario:
+### Exploit Scenario
- ```solidity
- contract Buggy{
- function my_func() external initializer{
- // ...
- a = b;
- a = c;
- // ..
- }
+```solidity
+contract Buggy{
+ function my_func() external initializer{
+ // ...
+ a = b;
+ a = c;
+ // ..
}
- ```
- `a` is first asigned to `b`, and then to `c`. As a result the first write does nothing.
+}
+```
+
+`a` is first asigned to `b`, and then to `c`. As a result the first write does nothing.
### Recommendation
@@ -1389,7 +1390,7 @@ Fix or remove the writes.
Detects the misuse of a Boolean constant.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract A {
@@ -1426,9 +1427,9 @@ Verify and simplify the condition.
### Description
-Chronicle oracle is used and the price returned is not checked to be valid. For more information https://docs.chroniclelabs.org/Resources/FAQ/Oracles#how-do-i-check-if-an-oracle-becomes-inactive-gets-deprecated.
+Chronicle oracle is used and the price returned is not checked to be valid. For more information visit [https://docs.chroniclelabs.org/Resources/FAQ/Oracles#how-do-i-check-if-an-oracle-becomes-inactive-gets-deprecated](https://docs.chroniclelabs.org/Resources/FAQ/Oracles#how-do-i-check-if-an-oracle-becomes-inactive-gets-deprecated).
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract C {
@@ -1466,7 +1467,7 @@ Starting from Solidity 0.5, a call to a `constant`/`pure`/`view` function uses t
As a result, a call to an [incorrectly labeled function may trap a contract compiled with Solidity 0.5](https://solidity.readthedocs.io/en/develop/050-breaking-changes.html#interoperability-with-older-contracts).
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Constant{
@@ -1502,7 +1503,7 @@ Starting from Solidity 0.5, a call to a `constant`/`pure`/`view` function uses t
As a result, a call to an [incorrectly labeled function may trap a contract compiled with Solidity 0.5](https://solidity.readthedocs.io/en/develop/050-breaking-changes.html#interoperability-with-older-contracts).
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Constant{
@@ -1533,7 +1534,7 @@ Ensure that attributes of contracts compiled prior to Solidity 0.5.0 are correct
Solidity's integer division truncates. Thus, performing division before multiplication can lead to precision loss.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract A {
@@ -1543,8 +1544,8 @@ contract A {
}
```
-If `n` is greater than `oldSupply`, `coins` will be zero. For example, with `oldSupply = 5; n = 10, interest = 2`, coins will be zero.
-If `(oldSupply * interest / n)` was used, `coins` would have been `1`.
+If `n` is greater than `oldSupply`, `coins` will be zero. For example, with `oldSupply = 5; n = 10, interest = 2`, coins will be zero.
+If `(oldSupply * interest / n)` was used, `coins` would have been `1`.
In general, it's usually a good idea to re-arrange arithmetic to perform multiplication before division, unless the limit of a smaller type makes this dangerous.
### Recommendation
@@ -1563,7 +1564,7 @@ Consider ordering multiplication before division.
Detect calls to `_requestRandomness` within an unprotected function.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract C is GelatoVRFConsumerBase {
@@ -1599,7 +1600,7 @@ Function that request randomness should be allowed only to authorized users.
Out-of-order retryable transactions
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract L1 {
@@ -1652,7 +1653,7 @@ Bob calls `doStuffOnL2` but the first retryable ticket calling `claim_rewards` f
Do not rely on the order or successful execution of retryable tickets.
-## Reentrancy vulnerabilities
+## Reentrancy vulnerabilities no ETH
### Configuration
@@ -1665,7 +1666,7 @@ Do not rely on the order or successful execution of retryable tickets.
Detection of the [reentrancy bug](https://github.com/trailofbits/not-so-smart-contracts/tree/master/reentrancy).
Do not report reentrancies that involve Ether (see `reentrancy-eth`).
-### Exploit Scenario:
+### Exploit Scenario
```solidity
function bug(){
@@ -1693,7 +1694,7 @@ Apply the [`check-effects-interactions` pattern](http://solidity.readthedocs.io/
Detects if the same base constructor is called with arguments from two different locations in the same inheritance hierarchy.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
pragma solidity ^0.4.0;
@@ -1744,7 +1745,7 @@ Remove the duplicate constructor call.
`tx.origin`-based protection can be abused by a malicious contract if a legitimate user interacts with the malicious contract.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract TxOrigin {
@@ -1773,7 +1774,7 @@ Do not use `tx.origin` for authorization.
The return value of a low-level call is not checked.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract MyConc{
@@ -1802,7 +1803,7 @@ Ensure that the return value of a low-level call is checked or logged.
The return value of a `send` is not checked.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract MyConc{
@@ -1831,7 +1832,7 @@ Ensure that the return value of `send` is checked or logged.
Uninitialized local variables.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Uninitialized is Owner{
@@ -1860,7 +1861,7 @@ Initialize all the variables. If a variable is meant to be initialized to zero,
The return value of an external call is not stored in a local or state variable.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract MyConc{
@@ -1889,7 +1890,7 @@ Ensure that all the return values of the function calls are used.
Detect when Chainlink Feed Registry is used. At the moment is only available on Ethereum Mainnet.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
import "chainlink/contracts/src/v0.8/interfaces/FeedRegistryInteface.sol"
@@ -1927,7 +1928,7 @@ Do not use Chainlink Feed Registry outside of Ethereum Mainnet.
If a modifier does not execute `_` or revert, the execution of the function will return the default value, which can be misleading for the caller.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
modidfier myModif(){
@@ -1958,7 +1959,7 @@ All the paths in a modifier must execute `_` or revert.
Detect when deprecated Optimism predeploy or function is used.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
interface GasPriceOracle {
@@ -1992,7 +1993,7 @@ Do not use the deprecated components.
Detection of shadowing built-in symbols using local variables, state variables, functions, modifiers, or events.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
pragma solidity ^0.4.24;
@@ -2028,7 +2029,7 @@ Rename the local variables, state variables, functions, modifiers, and events th
Detection of shadowing using local variables.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
pragma solidity ^0.4.24;
@@ -2067,7 +2068,7 @@ Rename the local variables that shadow another component.
solc versions `0.4.5`-`0.4.26` and `0.5.0`-`0.5.8` contain a compiler bug leading to unexpected behavior when calling uninitialized function pointers in constructors.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract bad0 {
@@ -2099,7 +2100,7 @@ Initialize function pointers before calling. Avoid function pointers if possible
Detects the possible usage of a variable before the declaration is stepped over (either because it is later declared, or declared in another scope).
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract C {
@@ -2141,7 +2142,7 @@ Move all variable declarations prior to any usage of the variable, and ensure th
Detect the call to a constructor that is not implemented
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract A{}
@@ -2168,7 +2169,7 @@ Remove the constructor call.
Calls inside a loop might lead to a denial-of-service attack.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract CallsInLoop{
@@ -2206,7 +2207,7 @@ Favor [pull over push](https://github.com/ethereum/wiki/wiki/Safety#favor-pull-o
Detect missing events for critical access control parameters
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract C {
@@ -2240,7 +2241,7 @@ Emit an event for critical parameter changes.
Detect missing events for critical arithmetic parameters.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract C {
@@ -2278,7 +2279,7 @@ Emit an event for critical parameter changes.
Unary expressions such as `x=+1` probably typos.
-### Exploit Scenario:
+### Exploit Scenario
```Solidity
contract Bug{
@@ -2309,7 +2310,7 @@ Remove the unary expression.
Detect missing zero address validation.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract C {
@@ -2331,7 +2332,7 @@ Bob calls `updateOwner` without specifying the `newOwner`, so Bob loses ownershi
Check that the address is not zero.
-## Reentrancy vulnerabilities
+## Reentrancy vulnerabilities benign
### Configuration
@@ -2344,7 +2345,7 @@ Check that the address is not zero.
Detection of the [reentrancy bug](https://github.com/trailofbits/not-so-smart-contracts/tree/master/reentrancy).
Only report reentrancy that acts as a double call (see `reentrancy-eth`, `reentrancy-no-eth`).
-### Exploit Scenario:
+### Exploit Scenario
```solidity
function callme(){
@@ -2361,7 +2362,7 @@ Only report reentrancy that acts as a double call (see `reentrancy-eth`, `reentr
Apply the [`check-effects-interactions` pattern](http://solidity.readthedocs.io/en/v0.4.21/security-considerations.html#re-entrancy).
-## Reentrancy vulnerabilities
+## Reentrancy vulnerabilities events
### Configuration
@@ -2373,7 +2374,7 @@ Apply the [`check-effects-interactions` pattern](http://solidity.readthedocs.io/
Detects [reentrancies](https://github.com/trailofbits/not-so-smart-contracts/tree/master/reentrancy) that allow manipulation of the order or value of events.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract ReentrantContract {
@@ -2423,7 +2424,7 @@ Apply the [`check-effects-interactions` pattern](https://docs.soliditylang.org/e
A low level callee may consume all callers gas unexpectedly.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
//Modified from https://github.com/nomad-xyz/ExcessivelySafeCall
@@ -2474,7 +2475,7 @@ Avoid unlimited implicit decoding of returndata.
Dangerous usage of `block.timestamp`. `block.timestamp` can be manipulated by miners.
-### Exploit Scenario:
+### Exploit Scenario
"Bob's contract relies on `block.timestamp` for its randomness. Eve is a miner and manipulates `block.timestamp` to exploit Bob's contract.
@@ -2510,7 +2511,7 @@ Do not use `evm` assembly.
Incorrect use of `assert()`. See Solidity best [practices](https://solidity.readthedocs.io/en/latest/control-structures.html#id4).
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract A {
@@ -2541,7 +2542,7 @@ Use `require` for invariants modifying the state.
Detects the comparison to boolean constants.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract A {
@@ -2589,7 +2590,7 @@ Reduce cyclomatic complexity by splitting the function into several smaller subr
Detect the usage of deprecated standards.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract ContractWithDeprecatedReferences {
@@ -2635,7 +2636,7 @@ Replace all uses of deprecated symbols.
Detects whether events defined by the `ERC20` specification that should have some parameters as `indexed` are missing the `indexed` keyword.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract ERC20Bad {
@@ -2666,7 +2667,7 @@ Add the `indexed` keyword to event parameters that should include it, according
Detects the immediate initialization of state variables through function calls that are not pure/constant, or that use non-constant state variable.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract StateVarInitFromFunction {
@@ -2712,16 +2713,17 @@ Remove any initialization of state variables via non-constant state variables or
In Solidity, it is possible to use libraries for certain types, by the `using-for` statement (`using for `). However, the Solidity compiler doesn't check whether a given library has at least one function matching a given type. If it doesn't, such a statement has no effect and may be confusing.
-### Exploit Scenario:
+### Exploit Scenario
- ```solidity
- library L {
- function f(bool) public pure {}
- }
+```solidity
+library L {
+ function f(bool) public pure {}
+}
+
+using L for uint;
+```
- using L for uint;
- ```
- Such a code will compile despite the fact that `L` has no function with `uint` as its first argument.
+Such a code will compile despite the fact that `L` has no function with `uint` as its first argument.
### Recommendation
@@ -2755,7 +2757,7 @@ Avoid low-level calls. Check the call success. If the call is meant for a contra
Detect missing inheritance.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
interface ISomething {
@@ -2824,7 +2826,7 @@ Use one Solidity version.
Detect the usage of redundant statements that have no effect.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract RedundantStatementsContract {
@@ -2882,7 +2884,7 @@ Consider using the latest version of Solidity for testing.
Detect functions that are not implemented on derived-most contracts.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
interface BaseInterface {
@@ -2937,7 +2939,7 @@ Remove unused state variables.
Costly operations inside a loop might waste gas, so optimizations are justified.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract CostlyOperationsInLoop{
@@ -2979,7 +2981,7 @@ Use a local variable to hold the loop computation result.
Functions that are not used.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Contract{
@@ -2993,7 +2995,7 @@ contract Contract{
Remove unused functions.
-## Reentrancy vulnerabilities
+## Reentrancy vulnerabilities unlimited gas
### Configuration
@@ -3006,7 +3008,7 @@ Remove unused functions.
Detection of the [reentrancy bug](https://github.com/trailofbits/not-so-smart-contracts/tree/master/reentrancy).
Only report reentrancy that is based on `transfer` or `send`.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
function callme(){
@@ -3033,7 +3035,7 @@ Apply the [`check-effects-interactions` pattern](http://solidity.readthedocs.io/
Literals with many digits are difficult to read and review. Use scientific notation or suffixes to make the code more readable.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract MyContract{
@@ -3063,7 +3065,7 @@ Use:
Detects `for` loops that use `length` member of some storage array in their loop condition and don't modify it.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract C
@@ -3162,7 +3164,7 @@ Add the `immutable` attribute to state variables that never change or are set on
The contract reads its own variable using `this`, adding overhead of an unnecessary STATICCALL.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract C {
diff --git a/docs/src/printers/Printer-documentation.md b/docs/src/printers/Printer-documentation.md
index 389c9659b7..0695b55742 100644
--- a/docs/src/printers/Printer-documentation.md
+++ b/docs/src/printers/Printer-documentation.md
@@ -1,3 +1,5 @@
+# Printing contracts
+
Slither allows printing contracts information through its printers.
| Num | Printer | Description |
@@ -32,7 +34,7 @@ Slither allows printing contracts information through its printers.
Several printers require xdot installed for visualization:
-```
+```sh
sudo apt install xdot
```
@@ -44,23 +46,23 @@ Export the call-graph of the contracts to a dot file
### Example
-```
-$ slither examples/printers/call_graph.sol --print call-graph
+```sh
+slither examples/printers/call_graph.sol --print call-graph
```
-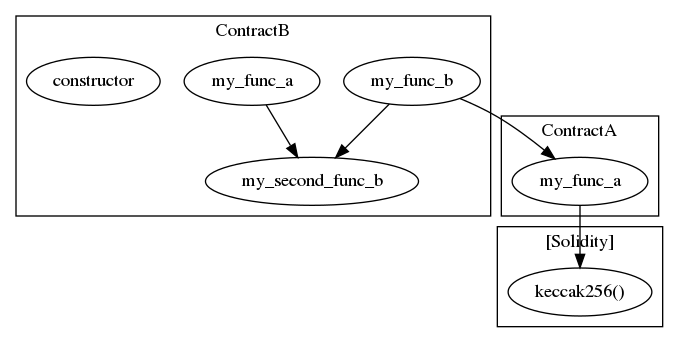 +
The output format is [dot](https://www.graphviz.org/).
To vizualize the graph:
-```
-$ xdot examples/printers/call_graph.sol.dot
+```sh
+xdot examples/printers/call_graph.sol.dot
```
To convert the file to svg:
-```
-$ dot examples/printers/call_graph.sol.dot -Tpng -o examples/printers/call_graph.sol.png
+```sh
+dot examples/printers/call_graph.sol.dot -Tpng -o examples/printers/call_graph.sol.png
```
## CFG
@@ -74,14 +76,14 @@ Export the control flow graph of each function
The output format is [dot](https://www.graphviz.org/).
To vizualize the graph:
-```
-$ xdot function.sol.dot
+```sh
+xdot function.sol.dot
```
To convert the file to svg:
-```
-$ dot function.dot -Tsvg -o function.sol.png
+```sh
+dot function.dot -Tsvg -o function.sol.png
```
## Contract Summary
@@ -92,11 +94,11 @@ Output a quick summary of the contract.
### Example
-```
-$ slither examples/printers/quick_summary.sol --print contract-summary
+```sh
+slither examples/printers/quick_summary.sol --print contract-summary
```
-
+
The output format is [dot](https://www.graphviz.org/).
To vizualize the graph:
-```
-$ xdot examples/printers/call_graph.sol.dot
+```sh
+xdot examples/printers/call_graph.sol.dot
```
To convert the file to svg:
-```
-$ dot examples/printers/call_graph.sol.dot -Tpng -o examples/printers/call_graph.sol.png
+```sh
+dot examples/printers/call_graph.sol.dot -Tpng -o examples/printers/call_graph.sol.png
```
## CFG
@@ -74,14 +76,14 @@ Export the control flow graph of each function
The output format is [dot](https://www.graphviz.org/).
To vizualize the graph:
-```
-$ xdot function.sol.dot
+```sh
+xdot function.sol.dot
```
To convert the file to svg:
-```
-$ dot function.dot -Tsvg -o function.sol.png
+```sh
+dot function.dot -Tsvg -o function.sol.png
```
## Contract Summary
@@ -92,11 +94,11 @@ Output a quick summary of the contract.
### Example
-```
-$ slither examples/printers/quick_summary.sol --print contract-summary
+```sh
+slither examples/printers/quick_summary.sol --print contract-summary
```
-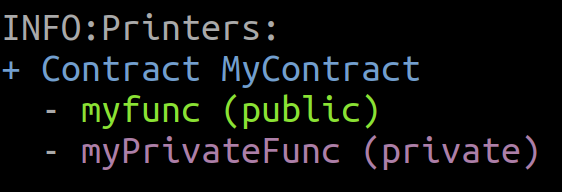 +
## Data Dependencies
@@ -105,11 +107,11 @@ Print the data dependencies of the variables
### Example
-```
-$ slither examples/printers/data_dependencies.sol --print data-dependency
+```sh
+slither examples/printers/data_dependencies.sol --print data-dependency
```
-```
+```text
Contract MyContract
+----------+----------------------+
| Variable | Dependencies |
@@ -148,7 +150,7 @@ Print the calling sequence of constructors based on C3 linearization.
### Example
-```
+```sh
...
$ slither examples/printers/constructors.sol --print constructor-calls
[..]
@@ -202,7 +204,7 @@ Print the EVM representation of the functions
### Example
-```
+```sh
$ slither examples/printers/evm.sol --print evm
INFO:Printers:Contract Test
@@ -266,7 +268,7 @@ Print the keccack256 signature of the functions
### Examples
-```
+```sh
$ slither examples/printers/authorization.sol --print function-id
INFO:Printers:
MyContract:
@@ -290,11 +292,11 @@ Output a summary of the contract showing for each function:
### Example
-```
-$ slither tests/backdoor.sol --print function-summary
+```sh
+slither tests/backdoor.sol --print function-summary
```
-```
+```text
[...]
Contract C
@@ -321,11 +323,11 @@ Print a human-readable summary of the contracts
### Example
-```
-$ slither examples/printers/human_printer.sol --print human-summary
+```sh
+slither examples/printers/human_printer.sol --print human-summary
```
-
+
## Data Dependencies
@@ -105,11 +107,11 @@ Print the data dependencies of the variables
### Example
-```
-$ slither examples/printers/data_dependencies.sol --print data-dependency
+```sh
+slither examples/printers/data_dependencies.sol --print data-dependency
```
-```
+```text
Contract MyContract
+----------+----------------------+
| Variable | Dependencies |
@@ -148,7 +150,7 @@ Print the calling sequence of constructors based on C3 linearization.
### Example
-```
+```sh
...
$ slither examples/printers/constructors.sol --print constructor-calls
[..]
@@ -202,7 +204,7 @@ Print the EVM representation of the functions
### Example
-```
+```sh
$ slither examples/printers/evm.sol --print evm
INFO:Printers:Contract Test
@@ -266,7 +268,7 @@ Print the keccack256 signature of the functions
### Examples
-```
+```sh
$ slither examples/printers/authorization.sol --print function-id
INFO:Printers:
MyContract:
@@ -290,11 +292,11 @@ Output a summary of the contract showing for each function:
### Example
-```
-$ slither tests/backdoor.sol --print function-summary
+```sh
+slither tests/backdoor.sol --print function-summary
```
-```
+```text
[...]
Contract C
@@ -321,11 +323,11 @@ Print a human-readable summary of the contracts
### Example
-```
-$ slither examples/printers/human_printer.sol --print human-summary
+```sh
+slither examples/printers/human_printer.sol --print human-summary
```
-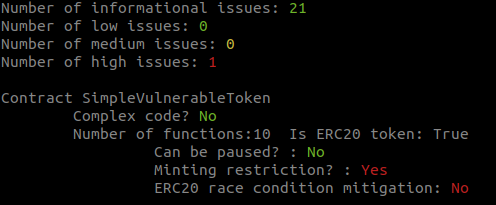 +
## Inheritance
@@ -334,11 +336,11 @@ Print the inheritance relations between contracts
### Example
-```
-$ slither examples/printers/inheritances.sol --print inheritance
+```sh
+slither examples/printers/inheritances.sol --print inheritance
```
-
+
## Inheritance
@@ -334,11 +336,11 @@ Print the inheritance relations between contracts
### Example
-```
-$ slither examples/printers/inheritances.sol --print inheritance
+```sh
+slither examples/printers/inheritances.sol --print inheritance
```
-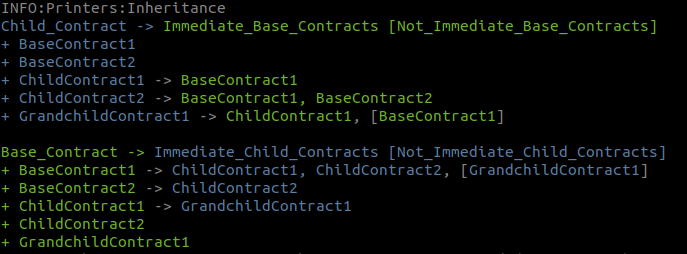 +
## Inheritance Graph
@@ -348,7 +350,7 @@ Output a graph showing the inheritance interaction between the contracts.
### Example
-```
+```sh
$ slither examples/printers/inheritances.sol --print inheritance-graph
[...]
INFO:PrinterInheritance:Inheritance Graph: examples/DAO.sol.dot
@@ -357,17 +359,17 @@ INFO:PrinterInheritance:Inheritance Graph: examples/DAO.sol.dot
The output format is [dot](https://www.graphviz.org/).
To vizualize the graph:
-```
-$ xdot examples/printers/inheritances.sol.dot
+```sh
+xdot examples/printers/inheritances.sol.dot
```
To convert the file to svg:
-```
-$ dot examples/printers/inheritances.sol.dot -Tsvg -o examples/printers/inheritances.sol.png
+```sh
+dot examples/printers/inheritances.sol.dot -Tsvg -o examples/printers/inheritances.sol.png
```
-
+
## Inheritance Graph
@@ -348,7 +350,7 @@ Output a graph showing the inheritance interaction between the contracts.
### Example
-```
+```sh
$ slither examples/printers/inheritances.sol --print inheritance-graph
[...]
INFO:PrinterInheritance:Inheritance Graph: examples/DAO.sol.dot
@@ -357,17 +359,17 @@ INFO:PrinterInheritance:Inheritance Graph: examples/DAO.sol.dot
The output format is [dot](https://www.graphviz.org/).
To vizualize the graph:
-```
-$ xdot examples/printers/inheritances.sol.dot
+```sh
+xdot examples/printers/inheritances.sol.dot
```
To convert the file to svg:
-```
-$ dot examples/printers/inheritances.sol.dot -Tsvg -o examples/printers/inheritances.sol.png
+```sh
+dot examples/printers/inheritances.sol.dot -Tsvg -o examples/printers/inheritances.sol.png
```
-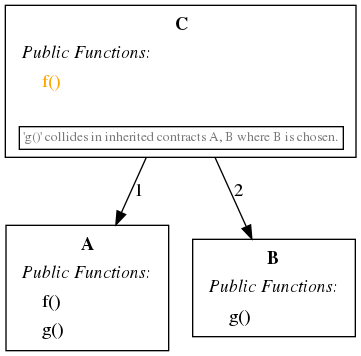 +
Indicators:
@@ -385,7 +387,7 @@ Print the modifiers called by each function.
### Example
-```
+```sh
$ slither examples/printers/modifier.sol --print modifiers
INFO:Printers:
Contract C
@@ -405,7 +407,7 @@ Print the require and assert calls of each function.
### Example
-```
+```sh
$ slither examples/printers/require.sol --print require
INFO:Printers:
Contract Lib
@@ -432,7 +434,7 @@ Print the slithIR representation of the functions
### Example
-```
+```sh
$ slither examples/printers/slihtir.sol --print slithir
Contract UnsafeMath
Function add(uint256,uint256)
@@ -475,7 +477,7 @@ Print the storage order of the state variables
### Example
-```
+```sh
$ slither tests/check-upgradability/contractV2_bug.sol --print variable-order
INFO:Printers:
ContractV2:
@@ -496,7 +498,7 @@ Print the variables written and the check on `msg.sender` of each function.
### Example
-```
+```sh
...
$ slither examples/printers/authorization.sol --print vars-and-auth
[..]
diff --git a/docs/src/tools/Adding-a-new-utility.md b/docs/src/tools/Adding-a-new-utility.md
index 54d1449d36..f62107b494 100644
--- a/docs/src/tools/Adding-a-new-utility.md
+++ b/docs/src/tools/Adding-a-new-utility.md
@@ -1,3 +1,5 @@
+# Adding New Utility
+
Slither can be used as a library to create new utilities.
Official utils are present in [tools](https://github.com/crytic/slither/tree/master/slither/tools)
diff --git a/docs/src/tools/Code-Similarity-Detector.md b/docs/src/tools/Code-Similarity-Detector.md
index 7446118cf0..cd921d0d2a 100644
--- a/docs/src/tools/Code-Similarity-Detector.md
+++ b/docs/src/tools/Code-Similarity-Detector.md
@@ -1,3 +1,5 @@
+# slither-simil
+
`slither-simil` uses state-of-the-art machine learning to detect similar (vulnerable) Solidity functions. We have provided a pretrained model from [etherscan_verified_contracts](https://github.com/thec00n/etherscan_verified_contracts) with 60,000 contracts and more than 850,000 functions to get you started quickly. We included the capability to easily train new models if you have access to larger or different datasets.
`slither-simil` uses [FastText](https://github.com/facebookresearch/fastText), a vector embedding technique, to generate compact numerical representations of every function. We used FastText because it:
@@ -11,10 +13,10 @@
Install the required packages before using `slither-simil`:
-```
-$ pip3 install pybind11 --user
-$ pip3 install https://github.com/facebookresearch/fastText/archive/0.2.0.zip --user
-$ pip3 install sklearn matplotlib --user # for plot mode
+```sh
+pip3 install pybind11 --user
+pip3 install https://github.com/facebookresearch/fastText/archive/0.2.0.zip --user
+pip3 install sklearn matplotlib --user # for plot mode
```
Make sure that you are using `pip3.6` or later. If you are running from inside a [virtualenv](https://virtualenv.pypa.io/en/latest/), remove the `--user` parameter.
@@ -49,7 +51,7 @@ Use the cache to avoid long processing times to compile and vectorize the input
Here's an example that finds functions similar to `sendCoin` in `MetaCoin` (compiled with `solc-0.4.25`). Searching for similar functions among more than 800,000 functions takes only 20 seconds.
-```
+```sh
$ slither-simil test etherscan_verified_contracts.bin --filename MetaCoin.sol --fname MetaCoin.sendCoin --input cache.npz --ntop 25 --solc solc-0.4.25
INFO:Slither-simil:Reviewed 825062 functions, listing the 25 most similar ones:
INFO:Slither-simil:filename contract function score
@@ -84,7 +86,7 @@ INFO:Slither-simil:0x5f9f2ae7150d0beef3bb50ac8d8f4b43e6a6cc57_NABC.sol
Train mode trains new models used to vectorize functions. You will need a large amount of contracts/functions if you plan to train a new model.
-```
+```sh
$ slither-simil train model.bin --input contracts
INFO:Slither-simil:Saving extracted data into last_data_train.txt
INFO:Slither-simil:Starting training
@@ -106,7 +108,7 @@ Plot mode plots sets of functions to visually detect clusters of similar ones.
Here's an example to plot all the functions named `add` from contracts named `SafeMath` sampling from 500 random contracts:
-```
+```sh
$ slither-simil plot etherscan_verified_contracts.bin --fname SafeMath.add --input cache.npz --nsamples 500
INFO:Slither-simil:Loading data..
INFO:Slither-simil:Procesing data..
@@ -124,7 +126,7 @@ It can can be also used to plot sets of functions using only a name from any con
This mode has two features. You can inspect the internal information about a pre-trained model. Info mode is typically used for debugging.
-```
+```sh
$ slither-simil info etherscan_verified_contracts.bin
INFO:Slither-simil:etherscan_verified_contracts.bin uses the following words:
INFO:Slither-simil:
@@ -142,7 +144,7 @@ INFO:Slither-simil:(local_solc_variable(default)):=(temporary_variable)
... or examine the internal representation of function:
-```
+```sh
$ slither-simil info etherscan_verified_contracts.bin --filename MetaCoin.sol --fname MetaCoin.sendCoin --solc solc-0.4.25
INFO:Slither-simil:Function sendCoin in contract MetaCoin is encoded as:
INFO:Slither-simil:index(uint256) binary(<) condition(temporary_variable) return index(uint256) binary(-) index(uint256) binary(+) event return
diff --git a/docs/src/tools/Contract-Flattening.md b/docs/src/tools/Contract-Flattening.md
index 80447a5b56..1f7a084448 100644
--- a/docs/src/tools/Contract-Flattening.md
+++ b/docs/src/tools/Contract-Flattening.md
@@ -1,3 +1,5 @@
+# slither-flat
+
`slither-flat` produces a flattened version of the codebase.
## Features
diff --git a/docs/src/tools/ERC-Conformance.md b/docs/src/tools/ERC-Conformance.md
index 9dbdadbc6e..ea2ebad45e 100644
--- a/docs/src/tools/ERC-Conformance.md
+++ b/docs/src/tools/ERC-Conformance.md
@@ -1,3 +1,5 @@
+# slither-check-erc
+
`slither-check-erc` checks for ERC's conformance.
## Features
@@ -26,15 +28,15 @@
- [ERC2612](https://eips.ethereum.org/EIPS/eip-2612): Permit Extension for EIP-20 Signed Approvals
- [ERC4626](https://eips.ethereum.org/EIPS/eip-4626): Tokenized Vaults
-## Usage:
+## Usage
-```
+```sh
slither-check-erc contract.sol ContractName
```
For example, on
-```Solidity
+```solidity
contract ERC20{
event Transfer(address indexed,address,uint256);
@@ -49,7 +51,7 @@ contract ERC20{
The tool will report:
-```
+```text
# Check ERC20
## Check functions
diff --git a/docs/src/tools/Path-Finding-Utility.md b/docs/src/tools/Path-Finding-Utility.md
index b7618a8b29..4a4f3f0077 100644
--- a/docs/src/tools/Path-Finding-Utility.md
+++ b/docs/src/tools/Path-Finding-Utility.md
@@ -1,8 +1,10 @@
+# slither-find-paths
+
`slither-find-paths` finds all the paths that reach a given target.
## Usage
-```
+```sh
slither-find-paths file.sol [contract.function targets]
```
@@ -12,7 +14,7 @@ slither-find-paths file.sol [contract.function targets]
Tested on [tests/possible_paths/paths.sol](https://github.com/trailofbits/slither/blob/master/tests/possible_paths/paths.sol)
-```
+```sh
$ slither-find-paths paths.sol A.destination
Target functions:
- A.destination()
diff --git a/docs/src/tools/Property-generation.md b/docs/src/tools/Property-generation.md
index 5ceabef0dd..4785961540 100644
--- a/docs/src/tools/Property-generation.md
+++ b/docs/src/tools/Property-generation.md
@@ -1,3 +1,5 @@
+# slither-prop
+
`slither-prop` generates code properties (e.g., invariants) that can be tested with unit tests or [Echidna](https://github.com/crytic/echidna/), entirely automatically. Once you have these properties in hand, use [Crytic](https://crytic.io/) to continuously test them with every commit.
Note: `slither-prop` only supports Truffle for now. We'll be adding support for other frameworks soon!
@@ -13,7 +15,7 @@ There are four steps:
### Step 1. Generate the tests
-```
+```sh
slither-prop . --contract ContractName
```
@@ -26,7 +28,7 @@ slither-prop . --contract ContractName
For example on [examples/slither-prop](https://github.com/crytic/slither/tree/9623a2781faa4e7759f06d2e8c4adcd45078af69/examples/slither-prop).
-```
+```sh
Write contracts/crytic/interfaces.sol
Write contracts/crytic/PropertiesERC20BuggyTransferable.sol
Write contracts/crytic/TestERC20BuggyTransferable.sol
@@ -74,7 +76,7 @@ On [examples/slither-prop/contracts](https://github.com/crytic/slither/tree/9623
The first unit test file, named `InitializationX.js` will check that the constructor has been correctly initialized:
-```
+```sh
$ truffle test test/crytic/InitializationTestERC20BuggyTransferable.js
[..]
Contract: TestERC20BuggyTransferable
@@ -89,7 +91,7 @@ $ truffle test test/crytic/InitializationTestERC20BuggyTransferable.js
If all the unit tests passed, run the property tests:
-```
+```sh
$ truffle test test/crytic/InitializationTestERC20BuggyTransferable.js
Contract: TestERC20BuggyTransferable
✓ The address 0x0 should not receive tokens.
@@ -113,8 +115,8 @@ As you can see, the unit tests detect some of the bugs.
### Step 4. Run the property tests with Echidna
-```
-$ echidna-test . --contract TestERC20BuggyTransferable --config echidna_config.yaml
+```sh
+echidna-test . --contract TestERC20BuggyTransferable --config echidna_config.yaml
```
## Scenarios
@@ -123,7 +125,7 @@ $ echidna-test . --contract TestERC20BuggyTransferable --config echidna_config.y
Here are the available scenarios:
-```
+```sh
#################### ERC20 ####################
Transferable - Test the correct tokens transfer
Pausable - Test the pausable functionality
@@ -135,7 +137,7 @@ Burnable - Test the burn of tokens. Require the "burn(address) returns()" functi
## All properties
-```
+```sh
+-----+-------------------------------------------------------------------------+------------------------+
| Num | Description | Scenario |
+-----+-------------------------------------------------------------------------+------------------------+
diff --git a/docs/src/tools/README.md b/docs/src/tools/README.md
index f17053e89c..12c7f8828c 100644
--- a/docs/src/tools/README.md
+++ b/docs/src/tools/README.md
@@ -1,3 +1,5 @@
+# Slither Inbuilt Tools
+
Slither comes with inbuilt tools
| Name | Command-Line | What it Does |
diff --git a/docs/src/tools/Slither-format.md b/docs/src/tools/Slither-format.md
index 5f155160ce..6012f3b225 100644
--- a/docs/src/tools/Slither-format.md
+++ b/docs/src/tools/Slither-format.md
@@ -1,3 +1,5 @@
+# slither-format
+
`slither-format` generates automatically patches. The patches are compatible with `git`.
Carefully review each patch before applying it.
diff --git a/docs/src/tools/Upgradeability-Checks.md b/docs/src/tools/Upgradeability-Checks.md
index d2cf7a7a15..bf3f0e3b03 100644
--- a/docs/src/tools/Upgradeability-Checks.md
+++ b/docs/src/tools/Upgradeability-Checks.md
@@ -7,26 +7,26 @@
| Num | Check | What it Detects | Impact | Proxy | Contract V2 |
| --- | ----------------------- | --------------------------------------------------------------------------------------- | ------------- | ----- | ----------- |
| 1 | `became-constant` | [Variables that should not be constant](#variables-that-should-not-be-constant) | High | | X |
-| 2 | `function-id-collision` | [Functions IDs collision](#functions-ids-collisions) | High | X |
-| 3 | `function-shadowing` | [Functions shadowing](#functions-shadowing) | High | X |
-| 4 | `missing-calls` | [Missing calls to init functions](#initialize-functions-are-not-called) | High | |
-| 5 | `missing-init-modifier` | [initializer() is not called](#initializer-is-not-called) | High | |
-| 6 | `multiple-calls` | [Init functions called multiple times](#initialize-functions-are-called-multiple-times) | High | |
+| 2 | `function-id-collision` | [Functions IDs collision](#functions-ids-collisions) | High | X | |
+| 3 | `function-shadowing` | [Functions shadowing](#functions-shadowing) | High | X | |
+| 4 | `missing-calls` | [Missing calls to init functions](#initialize-functions-are-not-called) | High | | |
+| 5 | `missing-init-modifier` | [initializer() is not called](#initializer-is-not-called) | High | | |
+| 6 | `multiple-calls` | [Init functions called multiple times](#initialize-functions-are-called-multiple-times) | High | | |
| 7 | `order-vars-contracts` | [Incorrect vars order with the v2](#incorrect-variables-with-the-v2) | High | | X |
-| 8 | `order-vars-proxy` | [Incorrect vars order with the proxy](#incorrect-variables-with-the-proxy) | High | X |
-| 9 | `variables-initialized` | [State variables with an initial value](#state-variable-initialized) | High | |
+| 8 | `order-vars-proxy` | [Incorrect vars order with the proxy](#incorrect-variables-with-the-proxy) | High | X | |
+| 9 | `variables-initialized` | [State variables with an initial value](#state-variable-initialized) | High | | |
| 10 | `were-constant` | [Variables that should be constant](#variables-that-should-be-constant) | High | | X |
-| 11 | `extra-vars-proxy` | [Extra vars in the proxy](#extra-variables-in-the-proxy) | Medium | X |
+| 11 | `extra-vars-proxy` | [Extra vars in the proxy](#extra-variables-in-the-proxy) | Medium | X | |
| 12 | `missing-variables` | [Variable missing in the v2](#missing-variables) | Medium | | X |
| 13 | `extra-vars-v2` | [Extra vars in the v2](#extra-variables-in-the-v2) | Informational | | X |
-| 14 | `init-inherited` | [Initializable is not inherited](#initializable-is-not-inherited) | Informational | |
-| 15 | `init-missing` | [Initializable is missing](#initializable-is-missing) | Informational | |
-| 16 | `initialize-target` | [Initialize function that must be called](#initialize-function) | Informational | |
-| 17 | `initializer-missing` | [initializer() is missing](#initializer-is-missing) | Informational | |
+| 14 | `init-inherited` | [Initializable is not inherited](#initializable-is-not-inherited) | Informational | | |
+| 15 | `init-missing` | [Initializable is missing](#initializable-is-missing) | Informational | | |
+| 16 | `initialize-target` | [Initialize function that must be called](#initialize-function) | Informational | | |
+| 17 | `initializer-missing` | [initializer() is missing](#initializer-is-missing) | Informational | | |
## Usage
-```
+```sh
slither-check-upgradeability project ContractName
```
@@ -54,9 +54,9 @@ If you want to check also the proxy, use:
If you use zos, you will have the proxy and the contract in different directories.
-Likely, you will use one of the proxy from https://github.com/zeppelinos/zos. Clone the `zos`, and install the dependencies:
+Likely, you will use one of the proxy from [zos](https://github.com/zeppelinos/zos). Clone the `zos`, and install the dependencies:
-```
+```sh
git clone https://github.com/zeppelinos/zos
cd zos/packages/lib
npm install
@@ -67,7 +67,7 @@ Note: `contracts/mocks/WithConstructorImplementation.sol` must be removed as it
Then from your project directory:
-```
+```sh
slither-check-upgradeability . ContractName --proxy-filename /path/to/zos/packages/lib/ --proxy-name UpgradeabilityProxy
```
@@ -86,7 +86,7 @@ According to your setup, you might choose another proxy name than `Upgradeabilit
Detect state variables that should not be `constant̀`.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Contract{
@@ -120,7 +120,7 @@ Do not make an existing state variable `constant`.
Detect function ID collision between the contract and the proxy.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Contract{
@@ -154,7 +154,7 @@ Rename the function. Avoid public functions in the proxy.
Detect function shadowing between the contract and the proxy.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Contract{
@@ -187,7 +187,7 @@ Rename the function. Avoid public functions in the proxy.
Detect missing calls to initialize functions.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Base{
@@ -220,7 +220,7 @@ Ensure all the initialize functions are reached by the most derived initialize f
Detect if `Initializable.initializer()` is called.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Contract{
@@ -248,7 +248,7 @@ Use `Initializable.initializer()`.
Detect multiple calls to a initialize function.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Base{
@@ -288,7 +288,7 @@ Call only one time every initialize function.
Detect variables that are different between the original contract and the updated one.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Contract{
@@ -317,7 +317,7 @@ Respect the variable order of the original contract in the updated contract.
Detect variables that are different between the contract and the proxy.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Contract{
@@ -346,7 +346,7 @@ Avoid variables in the proxy. If a variable is in the proxy, ensure it has the s
Detect state variables that are initialized.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Contract{
@@ -371,7 +371,7 @@ Using initialize functions to write initial values in state variables.
Detect state variables that should be `constant̀`.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Contract{
@@ -405,7 +405,7 @@ Do not remove `constant` from a state variables during an update.
Detect variables that are in the proxy and not in the contract.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Contract{
@@ -435,7 +435,7 @@ Avoid variables in the proxy. If a variable is in the proxy, ensure it has the s
Detect variables that were present in the original contracts but are not in the updated one.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract V1{
@@ -469,7 +469,7 @@ Show new variables in the updated contract.
This finding does not have an immediate security impact and is informative.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Contract{
diff --git a/docs/src/tutorials/exercise1.md b/docs/src/tutorials/exercise1.md
index 887ba7b89b..11c8d26d42 100644
--- a/docs/src/tutorials/exercise1.md
+++ b/docs/src/tutorials/exercise1.md
@@ -14,7 +14,7 @@ Use `solc-select install 0.5.0 && solc-select use 0.5.0` to switch to solc 0.5.0
## Proposed Algorithm
-```
+```text
Get the Coin contract
For each contract in the project:
If Coin is in the list of inherited contracts:
diff --git a/docs/src/tutorials/exercise2.md b/docs/src/tutorials/exercise2.md
index b6c1a88427..2ef0a8a678 100644
--- a/docs/src/tutorials/exercise2.md
+++ b/docs/src/tutorials/exercise2.md
@@ -6,7 +6,7 @@ Our goal is to create a script that ensures all public and external functions ca
## Proposed Algorithm
-```
+```text
Create a whitelist of signatures
Explore all the functions
If the function is in the whitelist of signatures:
diff --git a/tests/e2e/printers/test_data/test_printer_cheatcode/README.md b/tests/e2e/printers/test_data/test_printer_cheatcode/README.md
index f1a26a296c..5141da7317 100644
--- a/tests/e2e/printers/test_data/test_printer_cheatcode/README.md
+++ b/tests/e2e/printers/test_data/test_printer_cheatcode/README.md
@@ -4,4 +4,5 @@ Init using :
```shell
forge install foundry-rs/forge-std
-```
\ No newline at end of file
+```
+
+
Indicators:
@@ -385,7 +387,7 @@ Print the modifiers called by each function.
### Example
-```
+```sh
$ slither examples/printers/modifier.sol --print modifiers
INFO:Printers:
Contract C
@@ -405,7 +407,7 @@ Print the require and assert calls of each function.
### Example
-```
+```sh
$ slither examples/printers/require.sol --print require
INFO:Printers:
Contract Lib
@@ -432,7 +434,7 @@ Print the slithIR representation of the functions
### Example
-```
+```sh
$ slither examples/printers/slihtir.sol --print slithir
Contract UnsafeMath
Function add(uint256,uint256)
@@ -475,7 +477,7 @@ Print the storage order of the state variables
### Example
-```
+```sh
$ slither tests/check-upgradability/contractV2_bug.sol --print variable-order
INFO:Printers:
ContractV2:
@@ -496,7 +498,7 @@ Print the variables written and the check on `msg.sender` of each function.
### Example
-```
+```sh
...
$ slither examples/printers/authorization.sol --print vars-and-auth
[..]
diff --git a/docs/src/tools/Adding-a-new-utility.md b/docs/src/tools/Adding-a-new-utility.md
index 54d1449d36..f62107b494 100644
--- a/docs/src/tools/Adding-a-new-utility.md
+++ b/docs/src/tools/Adding-a-new-utility.md
@@ -1,3 +1,5 @@
+# Adding New Utility
+
Slither can be used as a library to create new utilities.
Official utils are present in [tools](https://github.com/crytic/slither/tree/master/slither/tools)
diff --git a/docs/src/tools/Code-Similarity-Detector.md b/docs/src/tools/Code-Similarity-Detector.md
index 7446118cf0..cd921d0d2a 100644
--- a/docs/src/tools/Code-Similarity-Detector.md
+++ b/docs/src/tools/Code-Similarity-Detector.md
@@ -1,3 +1,5 @@
+# slither-simil
+
`slither-simil` uses state-of-the-art machine learning to detect similar (vulnerable) Solidity functions. We have provided a pretrained model from [etherscan_verified_contracts](https://github.com/thec00n/etherscan_verified_contracts) with 60,000 contracts and more than 850,000 functions to get you started quickly. We included the capability to easily train new models if you have access to larger or different datasets.
`slither-simil` uses [FastText](https://github.com/facebookresearch/fastText), a vector embedding technique, to generate compact numerical representations of every function. We used FastText because it:
@@ -11,10 +13,10 @@
Install the required packages before using `slither-simil`:
-```
-$ pip3 install pybind11 --user
-$ pip3 install https://github.com/facebookresearch/fastText/archive/0.2.0.zip --user
-$ pip3 install sklearn matplotlib --user # for plot mode
+```sh
+pip3 install pybind11 --user
+pip3 install https://github.com/facebookresearch/fastText/archive/0.2.0.zip --user
+pip3 install sklearn matplotlib --user # for plot mode
```
Make sure that you are using `pip3.6` or later. If you are running from inside a [virtualenv](https://virtualenv.pypa.io/en/latest/), remove the `--user` parameter.
@@ -49,7 +51,7 @@ Use the cache to avoid long processing times to compile and vectorize the input
Here's an example that finds functions similar to `sendCoin` in `MetaCoin` (compiled with `solc-0.4.25`). Searching for similar functions among more than 800,000 functions takes only 20 seconds.
-```
+```sh
$ slither-simil test etherscan_verified_contracts.bin --filename MetaCoin.sol --fname MetaCoin.sendCoin --input cache.npz --ntop 25 --solc solc-0.4.25
INFO:Slither-simil:Reviewed 825062 functions, listing the 25 most similar ones:
INFO:Slither-simil:filename contract function score
@@ -84,7 +86,7 @@ INFO:Slither-simil:0x5f9f2ae7150d0beef3bb50ac8d8f4b43e6a6cc57_NABC.sol
Train mode trains new models used to vectorize functions. You will need a large amount of contracts/functions if you plan to train a new model.
-```
+```sh
$ slither-simil train model.bin --input contracts
INFO:Slither-simil:Saving extracted data into last_data_train.txt
INFO:Slither-simil:Starting training
@@ -106,7 +108,7 @@ Plot mode plots sets of functions to visually detect clusters of similar ones.
Here's an example to plot all the functions named `add` from contracts named `SafeMath` sampling from 500 random contracts:
-```
+```sh
$ slither-simil plot etherscan_verified_contracts.bin --fname SafeMath.add --input cache.npz --nsamples 500
INFO:Slither-simil:Loading data..
INFO:Slither-simil:Procesing data..
@@ -124,7 +126,7 @@ It can can be also used to plot sets of functions using only a name from any con
This mode has two features. You can inspect the internal information about a pre-trained model. Info mode is typically used for debugging.
-```
+```sh
$ slither-simil info etherscan_verified_contracts.bin
INFO:Slither-simil:etherscan_verified_contracts.bin uses the following words:
INFO:Slither-simil:
@@ -142,7 +144,7 @@ INFO:Slither-simil:(local_solc_variable(default)):=(temporary_variable)
... or examine the internal representation of function:
-```
+```sh
$ slither-simil info etherscan_verified_contracts.bin --filename MetaCoin.sol --fname MetaCoin.sendCoin --solc solc-0.4.25
INFO:Slither-simil:Function sendCoin in contract MetaCoin is encoded as:
INFO:Slither-simil:index(uint256) binary(<) condition(temporary_variable) return index(uint256) binary(-) index(uint256) binary(+) event return
diff --git a/docs/src/tools/Contract-Flattening.md b/docs/src/tools/Contract-Flattening.md
index 80447a5b56..1f7a084448 100644
--- a/docs/src/tools/Contract-Flattening.md
+++ b/docs/src/tools/Contract-Flattening.md
@@ -1,3 +1,5 @@
+# slither-flat
+
`slither-flat` produces a flattened version of the codebase.
## Features
diff --git a/docs/src/tools/ERC-Conformance.md b/docs/src/tools/ERC-Conformance.md
index 9dbdadbc6e..ea2ebad45e 100644
--- a/docs/src/tools/ERC-Conformance.md
+++ b/docs/src/tools/ERC-Conformance.md
@@ -1,3 +1,5 @@
+# slither-check-erc
+
`slither-check-erc` checks for ERC's conformance.
## Features
@@ -26,15 +28,15 @@
- [ERC2612](https://eips.ethereum.org/EIPS/eip-2612): Permit Extension for EIP-20 Signed Approvals
- [ERC4626](https://eips.ethereum.org/EIPS/eip-4626): Tokenized Vaults
-## Usage:
+## Usage
-```
+```sh
slither-check-erc contract.sol ContractName
```
For example, on
-```Solidity
+```solidity
contract ERC20{
event Transfer(address indexed,address,uint256);
@@ -49,7 +51,7 @@ contract ERC20{
The tool will report:
-```
+```text
# Check ERC20
## Check functions
diff --git a/docs/src/tools/Path-Finding-Utility.md b/docs/src/tools/Path-Finding-Utility.md
index b7618a8b29..4a4f3f0077 100644
--- a/docs/src/tools/Path-Finding-Utility.md
+++ b/docs/src/tools/Path-Finding-Utility.md
@@ -1,8 +1,10 @@
+# slither-find-paths
+
`slither-find-paths` finds all the paths that reach a given target.
## Usage
-```
+```sh
slither-find-paths file.sol [contract.function targets]
```
@@ -12,7 +14,7 @@ slither-find-paths file.sol [contract.function targets]
Tested on [tests/possible_paths/paths.sol](https://github.com/trailofbits/slither/blob/master/tests/possible_paths/paths.sol)
-```
+```sh
$ slither-find-paths paths.sol A.destination
Target functions:
- A.destination()
diff --git a/docs/src/tools/Property-generation.md b/docs/src/tools/Property-generation.md
index 5ceabef0dd..4785961540 100644
--- a/docs/src/tools/Property-generation.md
+++ b/docs/src/tools/Property-generation.md
@@ -1,3 +1,5 @@
+# slither-prop
+
`slither-prop` generates code properties (e.g., invariants) that can be tested with unit tests or [Echidna](https://github.com/crytic/echidna/), entirely automatically. Once you have these properties in hand, use [Crytic](https://crytic.io/) to continuously test them with every commit.
Note: `slither-prop` only supports Truffle for now. We'll be adding support for other frameworks soon!
@@ -13,7 +15,7 @@ There are four steps:
### Step 1. Generate the tests
-```
+```sh
slither-prop . --contract ContractName
```
@@ -26,7 +28,7 @@ slither-prop . --contract ContractName
For example on [examples/slither-prop](https://github.com/crytic/slither/tree/9623a2781faa4e7759f06d2e8c4adcd45078af69/examples/slither-prop).
-```
+```sh
Write contracts/crytic/interfaces.sol
Write contracts/crytic/PropertiesERC20BuggyTransferable.sol
Write contracts/crytic/TestERC20BuggyTransferable.sol
@@ -74,7 +76,7 @@ On [examples/slither-prop/contracts](https://github.com/crytic/slither/tree/9623
The first unit test file, named `InitializationX.js` will check that the constructor has been correctly initialized:
-```
+```sh
$ truffle test test/crytic/InitializationTestERC20BuggyTransferable.js
[..]
Contract: TestERC20BuggyTransferable
@@ -89,7 +91,7 @@ $ truffle test test/crytic/InitializationTestERC20BuggyTransferable.js
If all the unit tests passed, run the property tests:
-```
+```sh
$ truffle test test/crytic/InitializationTestERC20BuggyTransferable.js
Contract: TestERC20BuggyTransferable
✓ The address 0x0 should not receive tokens.
@@ -113,8 +115,8 @@ As you can see, the unit tests detect some of the bugs.
### Step 4. Run the property tests with Echidna
-```
-$ echidna-test . --contract TestERC20BuggyTransferable --config echidna_config.yaml
+```sh
+echidna-test . --contract TestERC20BuggyTransferable --config echidna_config.yaml
```
## Scenarios
@@ -123,7 +125,7 @@ $ echidna-test . --contract TestERC20BuggyTransferable --config echidna_config.y
Here are the available scenarios:
-```
+```sh
#################### ERC20 ####################
Transferable - Test the correct tokens transfer
Pausable - Test the pausable functionality
@@ -135,7 +137,7 @@ Burnable - Test the burn of tokens. Require the "burn(address) returns()" functi
## All properties
-```
+```sh
+-----+-------------------------------------------------------------------------+------------------------+
| Num | Description | Scenario |
+-----+-------------------------------------------------------------------------+------------------------+
diff --git a/docs/src/tools/README.md b/docs/src/tools/README.md
index f17053e89c..12c7f8828c 100644
--- a/docs/src/tools/README.md
+++ b/docs/src/tools/README.md
@@ -1,3 +1,5 @@
+# Slither Inbuilt Tools
+
Slither comes with inbuilt tools
| Name | Command-Line | What it Does |
diff --git a/docs/src/tools/Slither-format.md b/docs/src/tools/Slither-format.md
index 5f155160ce..6012f3b225 100644
--- a/docs/src/tools/Slither-format.md
+++ b/docs/src/tools/Slither-format.md
@@ -1,3 +1,5 @@
+# slither-format
+
`slither-format` generates automatically patches. The patches are compatible with `git`.
Carefully review each patch before applying it.
diff --git a/docs/src/tools/Upgradeability-Checks.md b/docs/src/tools/Upgradeability-Checks.md
index d2cf7a7a15..bf3f0e3b03 100644
--- a/docs/src/tools/Upgradeability-Checks.md
+++ b/docs/src/tools/Upgradeability-Checks.md
@@ -7,26 +7,26 @@
| Num | Check | What it Detects | Impact | Proxy | Contract V2 |
| --- | ----------------------- | --------------------------------------------------------------------------------------- | ------------- | ----- | ----------- |
| 1 | `became-constant` | [Variables that should not be constant](#variables-that-should-not-be-constant) | High | | X |
-| 2 | `function-id-collision` | [Functions IDs collision](#functions-ids-collisions) | High | X |
-| 3 | `function-shadowing` | [Functions shadowing](#functions-shadowing) | High | X |
-| 4 | `missing-calls` | [Missing calls to init functions](#initialize-functions-are-not-called) | High | |
-| 5 | `missing-init-modifier` | [initializer() is not called](#initializer-is-not-called) | High | |
-| 6 | `multiple-calls` | [Init functions called multiple times](#initialize-functions-are-called-multiple-times) | High | |
+| 2 | `function-id-collision` | [Functions IDs collision](#functions-ids-collisions) | High | X | |
+| 3 | `function-shadowing` | [Functions shadowing](#functions-shadowing) | High | X | |
+| 4 | `missing-calls` | [Missing calls to init functions](#initialize-functions-are-not-called) | High | | |
+| 5 | `missing-init-modifier` | [initializer() is not called](#initializer-is-not-called) | High | | |
+| 6 | `multiple-calls` | [Init functions called multiple times](#initialize-functions-are-called-multiple-times) | High | | |
| 7 | `order-vars-contracts` | [Incorrect vars order with the v2](#incorrect-variables-with-the-v2) | High | | X |
-| 8 | `order-vars-proxy` | [Incorrect vars order with the proxy](#incorrect-variables-with-the-proxy) | High | X |
-| 9 | `variables-initialized` | [State variables with an initial value](#state-variable-initialized) | High | |
+| 8 | `order-vars-proxy` | [Incorrect vars order with the proxy](#incorrect-variables-with-the-proxy) | High | X | |
+| 9 | `variables-initialized` | [State variables with an initial value](#state-variable-initialized) | High | | |
| 10 | `were-constant` | [Variables that should be constant](#variables-that-should-be-constant) | High | | X |
-| 11 | `extra-vars-proxy` | [Extra vars in the proxy](#extra-variables-in-the-proxy) | Medium | X |
+| 11 | `extra-vars-proxy` | [Extra vars in the proxy](#extra-variables-in-the-proxy) | Medium | X | |
| 12 | `missing-variables` | [Variable missing in the v2](#missing-variables) | Medium | | X |
| 13 | `extra-vars-v2` | [Extra vars in the v2](#extra-variables-in-the-v2) | Informational | | X |
-| 14 | `init-inherited` | [Initializable is not inherited](#initializable-is-not-inherited) | Informational | |
-| 15 | `init-missing` | [Initializable is missing](#initializable-is-missing) | Informational | |
-| 16 | `initialize-target` | [Initialize function that must be called](#initialize-function) | Informational | |
-| 17 | `initializer-missing` | [initializer() is missing](#initializer-is-missing) | Informational | |
+| 14 | `init-inherited` | [Initializable is not inherited](#initializable-is-not-inherited) | Informational | | |
+| 15 | `init-missing` | [Initializable is missing](#initializable-is-missing) | Informational | | |
+| 16 | `initialize-target` | [Initialize function that must be called](#initialize-function) | Informational | | |
+| 17 | `initializer-missing` | [initializer() is missing](#initializer-is-missing) | Informational | | |
## Usage
-```
+```sh
slither-check-upgradeability project ContractName
```
@@ -54,9 +54,9 @@ If you want to check also the proxy, use:
If you use zos, you will have the proxy and the contract in different directories.
-Likely, you will use one of the proxy from https://github.com/zeppelinos/zos. Clone the `zos`, and install the dependencies:
+Likely, you will use one of the proxy from [zos](https://github.com/zeppelinos/zos). Clone the `zos`, and install the dependencies:
-```
+```sh
git clone https://github.com/zeppelinos/zos
cd zos/packages/lib
npm install
@@ -67,7 +67,7 @@ Note: `contracts/mocks/WithConstructorImplementation.sol` must be removed as it
Then from your project directory:
-```
+```sh
slither-check-upgradeability . ContractName --proxy-filename /path/to/zos/packages/lib/ --proxy-name UpgradeabilityProxy
```
@@ -86,7 +86,7 @@ According to your setup, you might choose another proxy name than `Upgradeabilit
Detect state variables that should not be `constant̀`.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Contract{
@@ -120,7 +120,7 @@ Do not make an existing state variable `constant`.
Detect function ID collision between the contract and the proxy.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Contract{
@@ -154,7 +154,7 @@ Rename the function. Avoid public functions in the proxy.
Detect function shadowing between the contract and the proxy.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Contract{
@@ -187,7 +187,7 @@ Rename the function. Avoid public functions in the proxy.
Detect missing calls to initialize functions.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Base{
@@ -220,7 +220,7 @@ Ensure all the initialize functions are reached by the most derived initialize f
Detect if `Initializable.initializer()` is called.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Contract{
@@ -248,7 +248,7 @@ Use `Initializable.initializer()`.
Detect multiple calls to a initialize function.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Base{
@@ -288,7 +288,7 @@ Call only one time every initialize function.
Detect variables that are different between the original contract and the updated one.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Contract{
@@ -317,7 +317,7 @@ Respect the variable order of the original contract in the updated contract.
Detect variables that are different between the contract and the proxy.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Contract{
@@ -346,7 +346,7 @@ Avoid variables in the proxy. If a variable is in the proxy, ensure it has the s
Detect state variables that are initialized.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Contract{
@@ -371,7 +371,7 @@ Using initialize functions to write initial values in state variables.
Detect state variables that should be `constant̀`.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Contract{
@@ -405,7 +405,7 @@ Do not remove `constant` from a state variables during an update.
Detect variables that are in the proxy and not in the contract.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Contract{
@@ -435,7 +435,7 @@ Avoid variables in the proxy. If a variable is in the proxy, ensure it has the s
Detect variables that were present in the original contracts but are not in the updated one.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract V1{
@@ -469,7 +469,7 @@ Show new variables in the updated contract.
This finding does not have an immediate security impact and is informative.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Contract{
diff --git a/docs/src/tutorials/exercise1.md b/docs/src/tutorials/exercise1.md
index 887ba7b89b..11c8d26d42 100644
--- a/docs/src/tutorials/exercise1.md
+++ b/docs/src/tutorials/exercise1.md
@@ -14,7 +14,7 @@ Use `solc-select install 0.5.0 && solc-select use 0.5.0` to switch to solc 0.5.0
## Proposed Algorithm
-```
+```text
Get the Coin contract
For each contract in the project:
If Coin is in the list of inherited contracts:
diff --git a/docs/src/tutorials/exercise2.md b/docs/src/tutorials/exercise2.md
index b6c1a88427..2ef0a8a678 100644
--- a/docs/src/tutorials/exercise2.md
+++ b/docs/src/tutorials/exercise2.md
@@ -6,7 +6,7 @@ Our goal is to create a script that ensures all public and external functions ca
## Proposed Algorithm
-```
+```text
Create a whitelist of signatures
Explore all the functions
If the function is in the whitelist of signatures:
diff --git a/tests/e2e/printers/test_data/test_printer_cheatcode/README.md b/tests/e2e/printers/test_data/test_printer_cheatcode/README.md
index f1a26a296c..5141da7317 100644
--- a/tests/e2e/printers/test_data/test_printer_cheatcode/README.md
+++ b/tests/e2e/printers/test_data/test_printer_cheatcode/README.md
@@ -4,4 +4,5 @@ Init using :
```shell
forge install foundry-rs/forge-std
-```
\ No newline at end of file
+```
+
 +
The output format is [dot](https://www.graphviz.org/).
To vizualize the graph:
-```
-$ xdot examples/printers/call_graph.sol.dot
+```sh
+xdot examples/printers/call_graph.sol.dot
```
To convert the file to svg:
-```
-$ dot examples/printers/call_graph.sol.dot -Tpng -o examples/printers/call_graph.sol.png
+```sh
+dot examples/printers/call_graph.sol.dot -Tpng -o examples/printers/call_graph.sol.png
```
## CFG
@@ -74,14 +76,14 @@ Export the control flow graph of each function
The output format is [dot](https://www.graphviz.org/).
To vizualize the graph:
-```
-$ xdot function.sol.dot
+```sh
+xdot function.sol.dot
```
To convert the file to svg:
-```
-$ dot function.dot -Tsvg -o function.sol.png
+```sh
+dot function.dot -Tsvg -o function.sol.png
```
## Contract Summary
@@ -92,11 +94,11 @@ Output a quick summary of the contract.
### Example
-```
-$ slither examples/printers/quick_summary.sol --print contract-summary
+```sh
+slither examples/printers/quick_summary.sol --print contract-summary
```
-
+
The output format is [dot](https://www.graphviz.org/).
To vizualize the graph:
-```
-$ xdot examples/printers/call_graph.sol.dot
+```sh
+xdot examples/printers/call_graph.sol.dot
```
To convert the file to svg:
-```
-$ dot examples/printers/call_graph.sol.dot -Tpng -o examples/printers/call_graph.sol.png
+```sh
+dot examples/printers/call_graph.sol.dot -Tpng -o examples/printers/call_graph.sol.png
```
## CFG
@@ -74,14 +76,14 @@ Export the control flow graph of each function
The output format is [dot](https://www.graphviz.org/).
To vizualize the graph:
-```
-$ xdot function.sol.dot
+```sh
+xdot function.sol.dot
```
To convert the file to svg:
-```
-$ dot function.dot -Tsvg -o function.sol.png
+```sh
+dot function.dot -Tsvg -o function.sol.png
```
## Contract Summary
@@ -92,11 +94,11 @@ Output a quick summary of the contract.
### Example
-```
-$ slither examples/printers/quick_summary.sol --print contract-summary
+```sh
+slither examples/printers/quick_summary.sol --print contract-summary
```
- +
## Data Dependencies
@@ -105,11 +107,11 @@ Print the data dependencies of the variables
### Example
-```
-$ slither examples/printers/data_dependencies.sol --print data-dependency
+```sh
+slither examples/printers/data_dependencies.sol --print data-dependency
```
-```
+```text
Contract MyContract
+----------+----------------------+
| Variable | Dependencies |
@@ -148,7 +150,7 @@ Print the calling sequence of constructors based on C3 linearization.
### Example
-```
+```sh
...
$ slither examples/printers/constructors.sol --print constructor-calls
[..]
@@ -202,7 +204,7 @@ Print the EVM representation of the functions
### Example
-```
+```sh
$ slither examples/printers/evm.sol --print evm
INFO:Printers:Contract Test
@@ -266,7 +268,7 @@ Print the keccack256 signature of the functions
### Examples
-```
+```sh
$ slither examples/printers/authorization.sol --print function-id
INFO:Printers:
MyContract:
@@ -290,11 +292,11 @@ Output a summary of the contract showing for each function:
### Example
-```
-$ slither tests/backdoor.sol --print function-summary
+```sh
+slither tests/backdoor.sol --print function-summary
```
-```
+```text
[...]
Contract C
@@ -321,11 +323,11 @@ Print a human-readable summary of the contracts
### Example
-```
-$ slither examples/printers/human_printer.sol --print human-summary
+```sh
+slither examples/printers/human_printer.sol --print human-summary
```
-
+
## Data Dependencies
@@ -105,11 +107,11 @@ Print the data dependencies of the variables
### Example
-```
-$ slither examples/printers/data_dependencies.sol --print data-dependency
+```sh
+slither examples/printers/data_dependencies.sol --print data-dependency
```
-```
+```text
Contract MyContract
+----------+----------------------+
| Variable | Dependencies |
@@ -148,7 +150,7 @@ Print the calling sequence of constructors based on C3 linearization.
### Example
-```
+```sh
...
$ slither examples/printers/constructors.sol --print constructor-calls
[..]
@@ -202,7 +204,7 @@ Print the EVM representation of the functions
### Example
-```
+```sh
$ slither examples/printers/evm.sol --print evm
INFO:Printers:Contract Test
@@ -266,7 +268,7 @@ Print the keccack256 signature of the functions
### Examples
-```
+```sh
$ slither examples/printers/authorization.sol --print function-id
INFO:Printers:
MyContract:
@@ -290,11 +292,11 @@ Output a summary of the contract showing for each function:
### Example
-```
-$ slither tests/backdoor.sol --print function-summary
+```sh
+slither tests/backdoor.sol --print function-summary
```
-```
+```text
[...]
Contract C
@@ -321,11 +323,11 @@ Print a human-readable summary of the contracts
### Example
-```
-$ slither examples/printers/human_printer.sol --print human-summary
+```sh
+slither examples/printers/human_printer.sol --print human-summary
```
- +
## Inheritance
@@ -334,11 +336,11 @@ Print the inheritance relations between contracts
### Example
-```
-$ slither examples/printers/inheritances.sol --print inheritance
+```sh
+slither examples/printers/inheritances.sol --print inheritance
```
-
+
## Inheritance
@@ -334,11 +336,11 @@ Print the inheritance relations between contracts
### Example
-```
-$ slither examples/printers/inheritances.sol --print inheritance
+```sh
+slither examples/printers/inheritances.sol --print inheritance
```
- +
## Inheritance Graph
@@ -348,7 +350,7 @@ Output a graph showing the inheritance interaction between the contracts.
### Example
-```
+```sh
$ slither examples/printers/inheritances.sol --print inheritance-graph
[...]
INFO:PrinterInheritance:Inheritance Graph: examples/DAO.sol.dot
@@ -357,17 +359,17 @@ INFO:PrinterInheritance:Inheritance Graph: examples/DAO.sol.dot
The output format is [dot](https://www.graphviz.org/).
To vizualize the graph:
-```
-$ xdot examples/printers/inheritances.sol.dot
+```sh
+xdot examples/printers/inheritances.sol.dot
```
To convert the file to svg:
-```
-$ dot examples/printers/inheritances.sol.dot -Tsvg -o examples/printers/inheritances.sol.png
+```sh
+dot examples/printers/inheritances.sol.dot -Tsvg -o examples/printers/inheritances.sol.png
```
-
+
## Inheritance Graph
@@ -348,7 +350,7 @@ Output a graph showing the inheritance interaction between the contracts.
### Example
-```
+```sh
$ slither examples/printers/inheritances.sol --print inheritance-graph
[...]
INFO:PrinterInheritance:Inheritance Graph: examples/DAO.sol.dot
@@ -357,17 +359,17 @@ INFO:PrinterInheritance:Inheritance Graph: examples/DAO.sol.dot
The output format is [dot](https://www.graphviz.org/).
To vizualize the graph:
-```
-$ xdot examples/printers/inheritances.sol.dot
+```sh
+xdot examples/printers/inheritances.sol.dot
```
To convert the file to svg:
-```
-$ dot examples/printers/inheritances.sol.dot -Tsvg -o examples/printers/inheritances.sol.png
+```sh
+dot examples/printers/inheritances.sol.dot -Tsvg -o examples/printers/inheritances.sol.png
```
- +
Indicators:
@@ -385,7 +387,7 @@ Print the modifiers called by each function.
### Example
-```
+```sh
$ slither examples/printers/modifier.sol --print modifiers
INFO:Printers:
Contract C
@@ -405,7 +407,7 @@ Print the require and assert calls of each function.
### Example
-```
+```sh
$ slither examples/printers/require.sol --print require
INFO:Printers:
Contract Lib
@@ -432,7 +434,7 @@ Print the slithIR representation of the functions
### Example
-```
+```sh
$ slither examples/printers/slihtir.sol --print slithir
Contract UnsafeMath
Function add(uint256,uint256)
@@ -475,7 +477,7 @@ Print the storage order of the state variables
### Example
-```
+```sh
$ slither tests/check-upgradability/contractV2_bug.sol --print variable-order
INFO:Printers:
ContractV2:
@@ -496,7 +498,7 @@ Print the variables written and the check on `msg.sender` of each function.
### Example
-```
+```sh
...
$ slither examples/printers/authorization.sol --print vars-and-auth
[..]
diff --git a/docs/src/tools/Adding-a-new-utility.md b/docs/src/tools/Adding-a-new-utility.md
index 54d1449d36..f62107b494 100644
--- a/docs/src/tools/Adding-a-new-utility.md
+++ b/docs/src/tools/Adding-a-new-utility.md
@@ -1,3 +1,5 @@
+# Adding New Utility
+
Slither can be used as a library to create new utilities.
Official utils are present in [tools](https://github.com/crytic/slither/tree/master/slither/tools)
diff --git a/docs/src/tools/Code-Similarity-Detector.md b/docs/src/tools/Code-Similarity-Detector.md
index 7446118cf0..cd921d0d2a 100644
--- a/docs/src/tools/Code-Similarity-Detector.md
+++ b/docs/src/tools/Code-Similarity-Detector.md
@@ -1,3 +1,5 @@
+# slither-simil
+
`slither-simil` uses state-of-the-art machine learning to detect similar (vulnerable) Solidity functions. We have provided a pretrained model from [etherscan_verified_contracts](https://github.com/thec00n/etherscan_verified_contracts) with 60,000 contracts and more than 850,000 functions to get you started quickly. We included the capability to easily train new models if you have access to larger or different datasets.
`slither-simil` uses [FastText](https://github.com/facebookresearch/fastText), a vector embedding technique, to generate compact numerical representations of every function. We used FastText because it:
@@ -11,10 +13,10 @@
Install the required packages before using `slither-simil`:
-```
-$ pip3 install pybind11 --user
-$ pip3 install https://github.com/facebookresearch/fastText/archive/0.2.0.zip --user
-$ pip3 install sklearn matplotlib --user # for plot mode
+```sh
+pip3 install pybind11 --user
+pip3 install https://github.com/facebookresearch/fastText/archive/0.2.0.zip --user
+pip3 install sklearn matplotlib --user # for plot mode
```
Make sure that you are using `pip3.6` or later. If you are running from inside a [virtualenv](https://virtualenv.pypa.io/en/latest/), remove the `--user` parameter.
@@ -49,7 +51,7 @@ Use the cache to avoid long processing times to compile and vectorize the input
Here's an example that finds functions similar to `sendCoin` in `MetaCoin` (compiled with `solc-0.4.25`). Searching for similar functions among more than 800,000 functions takes only 20 seconds.
-```
+```sh
$ slither-simil test etherscan_verified_contracts.bin --filename MetaCoin.sol --fname MetaCoin.sendCoin --input cache.npz --ntop 25 --solc solc-0.4.25
INFO:Slither-simil:Reviewed 825062 functions, listing the 25 most similar ones:
INFO:Slither-simil:filename contract function score
@@ -84,7 +86,7 @@ INFO:Slither-simil:0x5f9f2ae7150d0beef3bb50ac8d8f4b43e6a6cc57_NABC.sol
Train mode trains new models used to vectorize functions. You will need a large amount of contracts/functions if you plan to train a new model.
-```
+```sh
$ slither-simil train model.bin --input contracts
INFO:Slither-simil:Saving extracted data into last_data_train.txt
INFO:Slither-simil:Starting training
@@ -106,7 +108,7 @@ Plot mode plots sets of functions to visually detect clusters of similar ones.
Here's an example to plot all the functions named `add` from contracts named `SafeMath` sampling from 500 random contracts:
-```
+```sh
$ slither-simil plot etherscan_verified_contracts.bin --fname SafeMath.add --input cache.npz --nsamples 500
INFO:Slither-simil:Loading data..
INFO:Slither-simil:Procesing data..
@@ -124,7 +126,7 @@ It can can be also used to plot sets of functions using only a name from any con
This mode has two features. You can inspect the internal information about a pre-trained model. Info mode is typically used for debugging.
-```
+```sh
$ slither-simil info etherscan_verified_contracts.bin
INFO:Slither-simil:etherscan_verified_contracts.bin uses the following words:
INFO:Slither-simil:
@@ -142,7 +144,7 @@ INFO:Slither-simil:(local_solc_variable(default)):=(temporary_variable)
... or examine the internal representation of function:
-```
+```sh
$ slither-simil info etherscan_verified_contracts.bin --filename MetaCoin.sol --fname MetaCoin.sendCoin --solc solc-0.4.25
INFO:Slither-simil:Function sendCoin in contract MetaCoin is encoded as:
INFO:Slither-simil:index(uint256) binary(<) condition(temporary_variable) return index(uint256) binary(-) index(uint256) binary(+) event return
diff --git a/docs/src/tools/Contract-Flattening.md b/docs/src/tools/Contract-Flattening.md
index 80447a5b56..1f7a084448 100644
--- a/docs/src/tools/Contract-Flattening.md
+++ b/docs/src/tools/Contract-Flattening.md
@@ -1,3 +1,5 @@
+# slither-flat
+
`slither-flat` produces a flattened version of the codebase.
## Features
diff --git a/docs/src/tools/ERC-Conformance.md b/docs/src/tools/ERC-Conformance.md
index 9dbdadbc6e..ea2ebad45e 100644
--- a/docs/src/tools/ERC-Conformance.md
+++ b/docs/src/tools/ERC-Conformance.md
@@ -1,3 +1,5 @@
+# slither-check-erc
+
`slither-check-erc` checks for ERC's conformance.
## Features
@@ -26,15 +28,15 @@
- [ERC2612](https://eips.ethereum.org/EIPS/eip-2612): Permit Extension for EIP-20 Signed Approvals
- [ERC4626](https://eips.ethereum.org/EIPS/eip-4626): Tokenized Vaults
-## Usage:
+## Usage
-```
+```sh
slither-check-erc contract.sol ContractName
```
For example, on
-```Solidity
+```solidity
contract ERC20{
event Transfer(address indexed,address,uint256);
@@ -49,7 +51,7 @@ contract ERC20{
The tool will report:
-```
+```text
# Check ERC20
## Check functions
diff --git a/docs/src/tools/Path-Finding-Utility.md b/docs/src/tools/Path-Finding-Utility.md
index b7618a8b29..4a4f3f0077 100644
--- a/docs/src/tools/Path-Finding-Utility.md
+++ b/docs/src/tools/Path-Finding-Utility.md
@@ -1,8 +1,10 @@
+# slither-find-paths
+
`slither-find-paths` finds all the paths that reach a given target.
## Usage
-```
+```sh
slither-find-paths file.sol [contract.function targets]
```
@@ -12,7 +14,7 @@ slither-find-paths file.sol [contract.function targets]
Tested on [tests/possible_paths/paths.sol](https://github.com/trailofbits/slither/blob/master/tests/possible_paths/paths.sol)
-```
+```sh
$ slither-find-paths paths.sol A.destination
Target functions:
- A.destination()
diff --git a/docs/src/tools/Property-generation.md b/docs/src/tools/Property-generation.md
index 5ceabef0dd..4785961540 100644
--- a/docs/src/tools/Property-generation.md
+++ b/docs/src/tools/Property-generation.md
@@ -1,3 +1,5 @@
+# slither-prop
+
`slither-prop` generates code properties (e.g., invariants) that can be tested with unit tests or [Echidna](https://github.com/crytic/echidna/), entirely automatically. Once you have these properties in hand, use [Crytic](https://crytic.io/) to continuously test them with every commit.
Note: `slither-prop` only supports Truffle for now. We'll be adding support for other frameworks soon!
@@ -13,7 +15,7 @@ There are four steps:
### Step 1. Generate the tests
-```
+```sh
slither-prop . --contract ContractName
```
@@ -26,7 +28,7 @@ slither-prop . --contract ContractName
For example on [examples/slither-prop](https://github.com/crytic/slither/tree/9623a2781faa4e7759f06d2e8c4adcd45078af69/examples/slither-prop).
-```
+```sh
Write contracts/crytic/interfaces.sol
Write contracts/crytic/PropertiesERC20BuggyTransferable.sol
Write contracts/crytic/TestERC20BuggyTransferable.sol
@@ -74,7 +76,7 @@ On [examples/slither-prop/contracts](https://github.com/crytic/slither/tree/9623
The first unit test file, named `InitializationX.js` will check that the constructor has been correctly initialized:
-```
+```sh
$ truffle test test/crytic/InitializationTestERC20BuggyTransferable.js
[..]
Contract: TestERC20BuggyTransferable
@@ -89,7 +91,7 @@ $ truffle test test/crytic/InitializationTestERC20BuggyTransferable.js
If all the unit tests passed, run the property tests:
-```
+```sh
$ truffle test test/crytic/InitializationTestERC20BuggyTransferable.js
Contract: TestERC20BuggyTransferable
✓ The address 0x0 should not receive tokens.
@@ -113,8 +115,8 @@ As you can see, the unit tests detect some of the bugs.
### Step 4. Run the property tests with Echidna
-```
-$ echidna-test . --contract TestERC20BuggyTransferable --config echidna_config.yaml
+```sh
+echidna-test . --contract TestERC20BuggyTransferable --config echidna_config.yaml
```
## Scenarios
@@ -123,7 +125,7 @@ $ echidna-test . --contract TestERC20BuggyTransferable --config echidna_config.y
Here are the available scenarios:
-```
+```sh
#################### ERC20 ####################
Transferable - Test the correct tokens transfer
Pausable - Test the pausable functionality
@@ -135,7 +137,7 @@ Burnable - Test the burn of tokens. Require the "burn(address) returns()" functi
## All properties
-```
+```sh
+-----+-------------------------------------------------------------------------+------------------------+
| Num | Description | Scenario |
+-----+-------------------------------------------------------------------------+------------------------+
diff --git a/docs/src/tools/README.md b/docs/src/tools/README.md
index f17053e89c..12c7f8828c 100644
--- a/docs/src/tools/README.md
+++ b/docs/src/tools/README.md
@@ -1,3 +1,5 @@
+# Slither Inbuilt Tools
+
Slither comes with inbuilt tools
| Name | Command-Line | What it Does |
diff --git a/docs/src/tools/Slither-format.md b/docs/src/tools/Slither-format.md
index 5f155160ce..6012f3b225 100644
--- a/docs/src/tools/Slither-format.md
+++ b/docs/src/tools/Slither-format.md
@@ -1,3 +1,5 @@
+# slither-format
+
`slither-format` generates automatically patches. The patches are compatible with `git`.
Carefully review each patch before applying it.
diff --git a/docs/src/tools/Upgradeability-Checks.md b/docs/src/tools/Upgradeability-Checks.md
index d2cf7a7a15..bf3f0e3b03 100644
--- a/docs/src/tools/Upgradeability-Checks.md
+++ b/docs/src/tools/Upgradeability-Checks.md
@@ -7,26 +7,26 @@
| Num | Check | What it Detects | Impact | Proxy | Contract V2 |
| --- | ----------------------- | --------------------------------------------------------------------------------------- | ------------- | ----- | ----------- |
| 1 | `became-constant` | [Variables that should not be constant](#variables-that-should-not-be-constant) | High | | X |
-| 2 | `function-id-collision` | [Functions IDs collision](#functions-ids-collisions) | High | X |
-| 3 | `function-shadowing` | [Functions shadowing](#functions-shadowing) | High | X |
-| 4 | `missing-calls` | [Missing calls to init functions](#initialize-functions-are-not-called) | High | |
-| 5 | `missing-init-modifier` | [initializer() is not called](#initializer-is-not-called) | High | |
-| 6 | `multiple-calls` | [Init functions called multiple times](#initialize-functions-are-called-multiple-times) | High | |
+| 2 | `function-id-collision` | [Functions IDs collision](#functions-ids-collisions) | High | X | |
+| 3 | `function-shadowing` | [Functions shadowing](#functions-shadowing) | High | X | |
+| 4 | `missing-calls` | [Missing calls to init functions](#initialize-functions-are-not-called) | High | | |
+| 5 | `missing-init-modifier` | [initializer() is not called](#initializer-is-not-called) | High | | |
+| 6 | `multiple-calls` | [Init functions called multiple times](#initialize-functions-are-called-multiple-times) | High | | |
| 7 | `order-vars-contracts` | [Incorrect vars order with the v2](#incorrect-variables-with-the-v2) | High | | X |
-| 8 | `order-vars-proxy` | [Incorrect vars order with the proxy](#incorrect-variables-with-the-proxy) | High | X |
-| 9 | `variables-initialized` | [State variables with an initial value](#state-variable-initialized) | High | |
+| 8 | `order-vars-proxy` | [Incorrect vars order with the proxy](#incorrect-variables-with-the-proxy) | High | X | |
+| 9 | `variables-initialized` | [State variables with an initial value](#state-variable-initialized) | High | | |
| 10 | `were-constant` | [Variables that should be constant](#variables-that-should-be-constant) | High | | X |
-| 11 | `extra-vars-proxy` | [Extra vars in the proxy](#extra-variables-in-the-proxy) | Medium | X |
+| 11 | `extra-vars-proxy` | [Extra vars in the proxy](#extra-variables-in-the-proxy) | Medium | X | |
| 12 | `missing-variables` | [Variable missing in the v2](#missing-variables) | Medium | | X |
| 13 | `extra-vars-v2` | [Extra vars in the v2](#extra-variables-in-the-v2) | Informational | | X |
-| 14 | `init-inherited` | [Initializable is not inherited](#initializable-is-not-inherited) | Informational | |
-| 15 | `init-missing` | [Initializable is missing](#initializable-is-missing) | Informational | |
-| 16 | `initialize-target` | [Initialize function that must be called](#initialize-function) | Informational | |
-| 17 | `initializer-missing` | [initializer() is missing](#initializer-is-missing) | Informational | |
+| 14 | `init-inherited` | [Initializable is not inherited](#initializable-is-not-inherited) | Informational | | |
+| 15 | `init-missing` | [Initializable is missing](#initializable-is-missing) | Informational | | |
+| 16 | `initialize-target` | [Initialize function that must be called](#initialize-function) | Informational | | |
+| 17 | `initializer-missing` | [initializer() is missing](#initializer-is-missing) | Informational | | |
## Usage
-```
+```sh
slither-check-upgradeability project ContractName
```
@@ -54,9 +54,9 @@ If you want to check also the proxy, use:
If you use zos, you will have the proxy and the contract in different directories.
-Likely, you will use one of the proxy from https://github.com/zeppelinos/zos. Clone the `zos`, and install the dependencies:
+Likely, you will use one of the proxy from [zos](https://github.com/zeppelinos/zos). Clone the `zos`, and install the dependencies:
-```
+```sh
git clone https://github.com/zeppelinos/zos
cd zos/packages/lib
npm install
@@ -67,7 +67,7 @@ Note: `contracts/mocks/WithConstructorImplementation.sol` must be removed as it
Then from your project directory:
-```
+```sh
slither-check-upgradeability . ContractName --proxy-filename /path/to/zos/packages/lib/ --proxy-name UpgradeabilityProxy
```
@@ -86,7 +86,7 @@ According to your setup, you might choose another proxy name than `Upgradeabilit
Detect state variables that should not be `constant̀`.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Contract{
@@ -120,7 +120,7 @@ Do not make an existing state variable `constant`.
Detect function ID collision between the contract and the proxy.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Contract{
@@ -154,7 +154,7 @@ Rename the function. Avoid public functions in the proxy.
Detect function shadowing between the contract and the proxy.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Contract{
@@ -187,7 +187,7 @@ Rename the function. Avoid public functions in the proxy.
Detect missing calls to initialize functions.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Base{
@@ -220,7 +220,7 @@ Ensure all the initialize functions are reached by the most derived initialize f
Detect if `Initializable.initializer()` is called.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Contract{
@@ -248,7 +248,7 @@ Use `Initializable.initializer()`.
Detect multiple calls to a initialize function.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Base{
@@ -288,7 +288,7 @@ Call only one time every initialize function.
Detect variables that are different between the original contract and the updated one.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Contract{
@@ -317,7 +317,7 @@ Respect the variable order of the original contract in the updated contract.
Detect variables that are different between the contract and the proxy.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Contract{
@@ -346,7 +346,7 @@ Avoid variables in the proxy. If a variable is in the proxy, ensure it has the s
Detect state variables that are initialized.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Contract{
@@ -371,7 +371,7 @@ Using initialize functions to write initial values in state variables.
Detect state variables that should be `constant̀`.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Contract{
@@ -405,7 +405,7 @@ Do not remove `constant` from a state variables during an update.
Detect variables that are in the proxy and not in the contract.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Contract{
@@ -435,7 +435,7 @@ Avoid variables in the proxy. If a variable is in the proxy, ensure it has the s
Detect variables that were present in the original contracts but are not in the updated one.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract V1{
@@ -469,7 +469,7 @@ Show new variables in the updated contract.
This finding does not have an immediate security impact and is informative.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Contract{
diff --git a/docs/src/tutorials/exercise1.md b/docs/src/tutorials/exercise1.md
index 887ba7b89b..11c8d26d42 100644
--- a/docs/src/tutorials/exercise1.md
+++ b/docs/src/tutorials/exercise1.md
@@ -14,7 +14,7 @@ Use `solc-select install 0.5.0 && solc-select use 0.5.0` to switch to solc 0.5.0
## Proposed Algorithm
-```
+```text
Get the Coin contract
For each contract in the project:
If Coin is in the list of inherited contracts:
diff --git a/docs/src/tutorials/exercise2.md b/docs/src/tutorials/exercise2.md
index b6c1a88427..2ef0a8a678 100644
--- a/docs/src/tutorials/exercise2.md
+++ b/docs/src/tutorials/exercise2.md
@@ -6,7 +6,7 @@ Our goal is to create a script that ensures all public and external functions ca
## Proposed Algorithm
-```
+```text
Create a whitelist of signatures
Explore all the functions
If the function is in the whitelist of signatures:
diff --git a/tests/e2e/printers/test_data/test_printer_cheatcode/README.md b/tests/e2e/printers/test_data/test_printer_cheatcode/README.md
index f1a26a296c..5141da7317 100644
--- a/tests/e2e/printers/test_data/test_printer_cheatcode/README.md
+++ b/tests/e2e/printers/test_data/test_printer_cheatcode/README.md
@@ -4,4 +4,5 @@ Init using :
```shell
forge install foundry-rs/forge-std
-```
\ No newline at end of file
+```
+
+
Indicators:
@@ -385,7 +387,7 @@ Print the modifiers called by each function.
### Example
-```
+```sh
$ slither examples/printers/modifier.sol --print modifiers
INFO:Printers:
Contract C
@@ -405,7 +407,7 @@ Print the require and assert calls of each function.
### Example
-```
+```sh
$ slither examples/printers/require.sol --print require
INFO:Printers:
Contract Lib
@@ -432,7 +434,7 @@ Print the slithIR representation of the functions
### Example
-```
+```sh
$ slither examples/printers/slihtir.sol --print slithir
Contract UnsafeMath
Function add(uint256,uint256)
@@ -475,7 +477,7 @@ Print the storage order of the state variables
### Example
-```
+```sh
$ slither tests/check-upgradability/contractV2_bug.sol --print variable-order
INFO:Printers:
ContractV2:
@@ -496,7 +498,7 @@ Print the variables written and the check on `msg.sender` of each function.
### Example
-```
+```sh
...
$ slither examples/printers/authorization.sol --print vars-and-auth
[..]
diff --git a/docs/src/tools/Adding-a-new-utility.md b/docs/src/tools/Adding-a-new-utility.md
index 54d1449d36..f62107b494 100644
--- a/docs/src/tools/Adding-a-new-utility.md
+++ b/docs/src/tools/Adding-a-new-utility.md
@@ -1,3 +1,5 @@
+# Adding New Utility
+
Slither can be used as a library to create new utilities.
Official utils are present in [tools](https://github.com/crytic/slither/tree/master/slither/tools)
diff --git a/docs/src/tools/Code-Similarity-Detector.md b/docs/src/tools/Code-Similarity-Detector.md
index 7446118cf0..cd921d0d2a 100644
--- a/docs/src/tools/Code-Similarity-Detector.md
+++ b/docs/src/tools/Code-Similarity-Detector.md
@@ -1,3 +1,5 @@
+# slither-simil
+
`slither-simil` uses state-of-the-art machine learning to detect similar (vulnerable) Solidity functions. We have provided a pretrained model from [etherscan_verified_contracts](https://github.com/thec00n/etherscan_verified_contracts) with 60,000 contracts and more than 850,000 functions to get you started quickly. We included the capability to easily train new models if you have access to larger or different datasets.
`slither-simil` uses [FastText](https://github.com/facebookresearch/fastText), a vector embedding technique, to generate compact numerical representations of every function. We used FastText because it:
@@ -11,10 +13,10 @@
Install the required packages before using `slither-simil`:
-```
-$ pip3 install pybind11 --user
-$ pip3 install https://github.com/facebookresearch/fastText/archive/0.2.0.zip --user
-$ pip3 install sklearn matplotlib --user # for plot mode
+```sh
+pip3 install pybind11 --user
+pip3 install https://github.com/facebookresearch/fastText/archive/0.2.0.zip --user
+pip3 install sklearn matplotlib --user # for plot mode
```
Make sure that you are using `pip3.6` or later. If you are running from inside a [virtualenv](https://virtualenv.pypa.io/en/latest/), remove the `--user` parameter.
@@ -49,7 +51,7 @@ Use the cache to avoid long processing times to compile and vectorize the input
Here's an example that finds functions similar to `sendCoin` in `MetaCoin` (compiled with `solc-0.4.25`). Searching for similar functions among more than 800,000 functions takes only 20 seconds.
-```
+```sh
$ slither-simil test etherscan_verified_contracts.bin --filename MetaCoin.sol --fname MetaCoin.sendCoin --input cache.npz --ntop 25 --solc solc-0.4.25
INFO:Slither-simil:Reviewed 825062 functions, listing the 25 most similar ones:
INFO:Slither-simil:filename contract function score
@@ -84,7 +86,7 @@ INFO:Slither-simil:0x5f9f2ae7150d0beef3bb50ac8d8f4b43e6a6cc57_NABC.sol
Train mode trains new models used to vectorize functions. You will need a large amount of contracts/functions if you plan to train a new model.
-```
+```sh
$ slither-simil train model.bin --input contracts
INFO:Slither-simil:Saving extracted data into last_data_train.txt
INFO:Slither-simil:Starting training
@@ -106,7 +108,7 @@ Plot mode plots sets of functions to visually detect clusters of similar ones.
Here's an example to plot all the functions named `add` from contracts named `SafeMath` sampling from 500 random contracts:
-```
+```sh
$ slither-simil plot etherscan_verified_contracts.bin --fname SafeMath.add --input cache.npz --nsamples 500
INFO:Slither-simil:Loading data..
INFO:Slither-simil:Procesing data..
@@ -124,7 +126,7 @@ It can can be also used to plot sets of functions using only a name from any con
This mode has two features. You can inspect the internal information about a pre-trained model. Info mode is typically used for debugging.
-```
+```sh
$ slither-simil info etherscan_verified_contracts.bin
INFO:Slither-simil:etherscan_verified_contracts.bin uses the following words:
INFO:Slither-simil:
@@ -142,7 +144,7 @@ INFO:Slither-simil:(local_solc_variable(default)):=(temporary_variable)
... or examine the internal representation of function:
-```
+```sh
$ slither-simil info etherscan_verified_contracts.bin --filename MetaCoin.sol --fname MetaCoin.sendCoin --solc solc-0.4.25
INFO:Slither-simil:Function sendCoin in contract MetaCoin is encoded as:
INFO:Slither-simil:index(uint256) binary(<) condition(temporary_variable) return index(uint256) binary(-) index(uint256) binary(+) event return
diff --git a/docs/src/tools/Contract-Flattening.md b/docs/src/tools/Contract-Flattening.md
index 80447a5b56..1f7a084448 100644
--- a/docs/src/tools/Contract-Flattening.md
+++ b/docs/src/tools/Contract-Flattening.md
@@ -1,3 +1,5 @@
+# slither-flat
+
`slither-flat` produces a flattened version of the codebase.
## Features
diff --git a/docs/src/tools/ERC-Conformance.md b/docs/src/tools/ERC-Conformance.md
index 9dbdadbc6e..ea2ebad45e 100644
--- a/docs/src/tools/ERC-Conformance.md
+++ b/docs/src/tools/ERC-Conformance.md
@@ -1,3 +1,5 @@
+# slither-check-erc
+
`slither-check-erc` checks for ERC's conformance.
## Features
@@ -26,15 +28,15 @@
- [ERC2612](https://eips.ethereum.org/EIPS/eip-2612): Permit Extension for EIP-20 Signed Approvals
- [ERC4626](https://eips.ethereum.org/EIPS/eip-4626): Tokenized Vaults
-## Usage:
+## Usage
-```
+```sh
slither-check-erc contract.sol ContractName
```
For example, on
-```Solidity
+```solidity
contract ERC20{
event Transfer(address indexed,address,uint256);
@@ -49,7 +51,7 @@ contract ERC20{
The tool will report:
-```
+```text
# Check ERC20
## Check functions
diff --git a/docs/src/tools/Path-Finding-Utility.md b/docs/src/tools/Path-Finding-Utility.md
index b7618a8b29..4a4f3f0077 100644
--- a/docs/src/tools/Path-Finding-Utility.md
+++ b/docs/src/tools/Path-Finding-Utility.md
@@ -1,8 +1,10 @@
+# slither-find-paths
+
`slither-find-paths` finds all the paths that reach a given target.
## Usage
-```
+```sh
slither-find-paths file.sol [contract.function targets]
```
@@ -12,7 +14,7 @@ slither-find-paths file.sol [contract.function targets]
Tested on [tests/possible_paths/paths.sol](https://github.com/trailofbits/slither/blob/master/tests/possible_paths/paths.sol)
-```
+```sh
$ slither-find-paths paths.sol A.destination
Target functions:
- A.destination()
diff --git a/docs/src/tools/Property-generation.md b/docs/src/tools/Property-generation.md
index 5ceabef0dd..4785961540 100644
--- a/docs/src/tools/Property-generation.md
+++ b/docs/src/tools/Property-generation.md
@@ -1,3 +1,5 @@
+# slither-prop
+
`slither-prop` generates code properties (e.g., invariants) that can be tested with unit tests or [Echidna](https://github.com/crytic/echidna/), entirely automatically. Once you have these properties in hand, use [Crytic](https://crytic.io/) to continuously test them with every commit.
Note: `slither-prop` only supports Truffle for now. We'll be adding support for other frameworks soon!
@@ -13,7 +15,7 @@ There are four steps:
### Step 1. Generate the tests
-```
+```sh
slither-prop . --contract ContractName
```
@@ -26,7 +28,7 @@ slither-prop . --contract ContractName
For example on [examples/slither-prop](https://github.com/crytic/slither/tree/9623a2781faa4e7759f06d2e8c4adcd45078af69/examples/slither-prop).
-```
+```sh
Write contracts/crytic/interfaces.sol
Write contracts/crytic/PropertiesERC20BuggyTransferable.sol
Write contracts/crytic/TestERC20BuggyTransferable.sol
@@ -74,7 +76,7 @@ On [examples/slither-prop/contracts](https://github.com/crytic/slither/tree/9623
The first unit test file, named `InitializationX.js` will check that the constructor has been correctly initialized:
-```
+```sh
$ truffle test test/crytic/InitializationTestERC20BuggyTransferable.js
[..]
Contract: TestERC20BuggyTransferable
@@ -89,7 +91,7 @@ $ truffle test test/crytic/InitializationTestERC20BuggyTransferable.js
If all the unit tests passed, run the property tests:
-```
+```sh
$ truffle test test/crytic/InitializationTestERC20BuggyTransferable.js
Contract: TestERC20BuggyTransferable
✓ The address 0x0 should not receive tokens.
@@ -113,8 +115,8 @@ As you can see, the unit tests detect some of the bugs.
### Step 4. Run the property tests with Echidna
-```
-$ echidna-test . --contract TestERC20BuggyTransferable --config echidna_config.yaml
+```sh
+echidna-test . --contract TestERC20BuggyTransferable --config echidna_config.yaml
```
## Scenarios
@@ -123,7 +125,7 @@ $ echidna-test . --contract TestERC20BuggyTransferable --config echidna_config.y
Here are the available scenarios:
-```
+```sh
#################### ERC20 ####################
Transferable - Test the correct tokens transfer
Pausable - Test the pausable functionality
@@ -135,7 +137,7 @@ Burnable - Test the burn of tokens. Require the "burn(address) returns()" functi
## All properties
-```
+```sh
+-----+-------------------------------------------------------------------------+------------------------+
| Num | Description | Scenario |
+-----+-------------------------------------------------------------------------+------------------------+
diff --git a/docs/src/tools/README.md b/docs/src/tools/README.md
index f17053e89c..12c7f8828c 100644
--- a/docs/src/tools/README.md
+++ b/docs/src/tools/README.md
@@ -1,3 +1,5 @@
+# Slither Inbuilt Tools
+
Slither comes with inbuilt tools
| Name | Command-Line | What it Does |
diff --git a/docs/src/tools/Slither-format.md b/docs/src/tools/Slither-format.md
index 5f155160ce..6012f3b225 100644
--- a/docs/src/tools/Slither-format.md
+++ b/docs/src/tools/Slither-format.md
@@ -1,3 +1,5 @@
+# slither-format
+
`slither-format` generates automatically patches. The patches are compatible with `git`.
Carefully review each patch before applying it.
diff --git a/docs/src/tools/Upgradeability-Checks.md b/docs/src/tools/Upgradeability-Checks.md
index d2cf7a7a15..bf3f0e3b03 100644
--- a/docs/src/tools/Upgradeability-Checks.md
+++ b/docs/src/tools/Upgradeability-Checks.md
@@ -7,26 +7,26 @@
| Num | Check | What it Detects | Impact | Proxy | Contract V2 |
| --- | ----------------------- | --------------------------------------------------------------------------------------- | ------------- | ----- | ----------- |
| 1 | `became-constant` | [Variables that should not be constant](#variables-that-should-not-be-constant) | High | | X |
-| 2 | `function-id-collision` | [Functions IDs collision](#functions-ids-collisions) | High | X |
-| 3 | `function-shadowing` | [Functions shadowing](#functions-shadowing) | High | X |
-| 4 | `missing-calls` | [Missing calls to init functions](#initialize-functions-are-not-called) | High | |
-| 5 | `missing-init-modifier` | [initializer() is not called](#initializer-is-not-called) | High | |
-| 6 | `multiple-calls` | [Init functions called multiple times](#initialize-functions-are-called-multiple-times) | High | |
+| 2 | `function-id-collision` | [Functions IDs collision](#functions-ids-collisions) | High | X | |
+| 3 | `function-shadowing` | [Functions shadowing](#functions-shadowing) | High | X | |
+| 4 | `missing-calls` | [Missing calls to init functions](#initialize-functions-are-not-called) | High | | |
+| 5 | `missing-init-modifier` | [initializer() is not called](#initializer-is-not-called) | High | | |
+| 6 | `multiple-calls` | [Init functions called multiple times](#initialize-functions-are-called-multiple-times) | High | | |
| 7 | `order-vars-contracts` | [Incorrect vars order with the v2](#incorrect-variables-with-the-v2) | High | | X |
-| 8 | `order-vars-proxy` | [Incorrect vars order with the proxy](#incorrect-variables-with-the-proxy) | High | X |
-| 9 | `variables-initialized` | [State variables with an initial value](#state-variable-initialized) | High | |
+| 8 | `order-vars-proxy` | [Incorrect vars order with the proxy](#incorrect-variables-with-the-proxy) | High | X | |
+| 9 | `variables-initialized` | [State variables with an initial value](#state-variable-initialized) | High | | |
| 10 | `were-constant` | [Variables that should be constant](#variables-that-should-be-constant) | High | | X |
-| 11 | `extra-vars-proxy` | [Extra vars in the proxy](#extra-variables-in-the-proxy) | Medium | X |
+| 11 | `extra-vars-proxy` | [Extra vars in the proxy](#extra-variables-in-the-proxy) | Medium | X | |
| 12 | `missing-variables` | [Variable missing in the v2](#missing-variables) | Medium | | X |
| 13 | `extra-vars-v2` | [Extra vars in the v2](#extra-variables-in-the-v2) | Informational | | X |
-| 14 | `init-inherited` | [Initializable is not inherited](#initializable-is-not-inherited) | Informational | |
-| 15 | `init-missing` | [Initializable is missing](#initializable-is-missing) | Informational | |
-| 16 | `initialize-target` | [Initialize function that must be called](#initialize-function) | Informational | |
-| 17 | `initializer-missing` | [initializer() is missing](#initializer-is-missing) | Informational | |
+| 14 | `init-inherited` | [Initializable is not inherited](#initializable-is-not-inherited) | Informational | | |
+| 15 | `init-missing` | [Initializable is missing](#initializable-is-missing) | Informational | | |
+| 16 | `initialize-target` | [Initialize function that must be called](#initialize-function) | Informational | | |
+| 17 | `initializer-missing` | [initializer() is missing](#initializer-is-missing) | Informational | | |
## Usage
-```
+```sh
slither-check-upgradeability project ContractName
```
@@ -54,9 +54,9 @@ If you want to check also the proxy, use:
If you use zos, you will have the proxy and the contract in different directories.
-Likely, you will use one of the proxy from https://github.com/zeppelinos/zos. Clone the `zos`, and install the dependencies:
+Likely, you will use one of the proxy from [zos](https://github.com/zeppelinos/zos). Clone the `zos`, and install the dependencies:
-```
+```sh
git clone https://github.com/zeppelinos/zos
cd zos/packages/lib
npm install
@@ -67,7 +67,7 @@ Note: `contracts/mocks/WithConstructorImplementation.sol` must be removed as it
Then from your project directory:
-```
+```sh
slither-check-upgradeability . ContractName --proxy-filename /path/to/zos/packages/lib/ --proxy-name UpgradeabilityProxy
```
@@ -86,7 +86,7 @@ According to your setup, you might choose another proxy name than `Upgradeabilit
Detect state variables that should not be `constant̀`.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Contract{
@@ -120,7 +120,7 @@ Do not make an existing state variable `constant`.
Detect function ID collision between the contract and the proxy.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Contract{
@@ -154,7 +154,7 @@ Rename the function. Avoid public functions in the proxy.
Detect function shadowing between the contract and the proxy.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Contract{
@@ -187,7 +187,7 @@ Rename the function. Avoid public functions in the proxy.
Detect missing calls to initialize functions.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Base{
@@ -220,7 +220,7 @@ Ensure all the initialize functions are reached by the most derived initialize f
Detect if `Initializable.initializer()` is called.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Contract{
@@ -248,7 +248,7 @@ Use `Initializable.initializer()`.
Detect multiple calls to a initialize function.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Base{
@@ -288,7 +288,7 @@ Call only one time every initialize function.
Detect variables that are different between the original contract and the updated one.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Contract{
@@ -317,7 +317,7 @@ Respect the variable order of the original contract in the updated contract.
Detect variables that are different between the contract and the proxy.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Contract{
@@ -346,7 +346,7 @@ Avoid variables in the proxy. If a variable is in the proxy, ensure it has the s
Detect state variables that are initialized.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Contract{
@@ -371,7 +371,7 @@ Using initialize functions to write initial values in state variables.
Detect state variables that should be `constant̀`.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Contract{
@@ -405,7 +405,7 @@ Do not remove `constant` from a state variables during an update.
Detect variables that are in the proxy and not in the contract.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Contract{
@@ -435,7 +435,7 @@ Avoid variables in the proxy. If a variable is in the proxy, ensure it has the s
Detect variables that were present in the original contracts but are not in the updated one.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract V1{
@@ -469,7 +469,7 @@ Show new variables in the updated contract.
This finding does not have an immediate security impact and is informative.
-### Exploit Scenario:
+### Exploit Scenario
```solidity
contract Contract{
diff --git a/docs/src/tutorials/exercise1.md b/docs/src/tutorials/exercise1.md
index 887ba7b89b..11c8d26d42 100644
--- a/docs/src/tutorials/exercise1.md
+++ b/docs/src/tutorials/exercise1.md
@@ -14,7 +14,7 @@ Use `solc-select install 0.5.0 && solc-select use 0.5.0` to switch to solc 0.5.0
## Proposed Algorithm
-```
+```text
Get the Coin contract
For each contract in the project:
If Coin is in the list of inherited contracts:
diff --git a/docs/src/tutorials/exercise2.md b/docs/src/tutorials/exercise2.md
index b6c1a88427..2ef0a8a678 100644
--- a/docs/src/tutorials/exercise2.md
+++ b/docs/src/tutorials/exercise2.md
@@ -6,7 +6,7 @@ Our goal is to create a script that ensures all public and external functions ca
## Proposed Algorithm
-```
+```text
Create a whitelist of signatures
Explore all the functions
If the function is in the whitelist of signatures:
diff --git a/tests/e2e/printers/test_data/test_printer_cheatcode/README.md b/tests/e2e/printers/test_data/test_printer_cheatcode/README.md
index f1a26a296c..5141da7317 100644
--- a/tests/e2e/printers/test_data/test_printer_cheatcode/README.md
+++ b/tests/e2e/printers/test_data/test_printer_cheatcode/README.md
@@ -4,4 +4,5 @@ Init using :
```shell
forge install foundry-rs/forge-std
-```
\ No newline at end of file
+```
+