|
1 | 1 | # Google |
2 | 2 |
|
3 | | -## Sample Configuration |
| 3 | +## Introduction |
4 | 4 |
|
5 | | - |
| 5 | +Integrating Google as your Single Sign-On (SSO) provider enables users to authenticate with their Google accounts, ensuring secure and streamlined access to Devtron. This document walks you through setting up Google SSO in Devtron, ensuring users can log in smoothly. |
6 | 6 |
|
7 | | ---- |
| 7 | +## Prerequisites |
8 | 8 |
|
9 | | -## Values You Would Require at SSO Provider |
| 9 | +To configure Google SSO in Devtron, you will need: |
10 | 10 |
|
11 | | -Devtron provides a sample configuration out of the box. There are some values that you need to either get from your SSO provider or give to your SSO provider. |
| 11 | +* Super Admin permissions |
| 12 | + * Only a [Super-Admin](https://docs.devtron.ai/global-configurations/authorization/user-access) can configure SSO. If you are setting up SSO for the first time, use [Admin Credentials](https://docs.devtron.ai/install/install-devtron#devtron-admin-credentials) instead. |
| 13 | +* A Google Cloud account to create and manage OAuth credentials. If you don’t have one, you must create it at the [Google Cloud Console](https://console.cloud.google.com/). |
12 | 14 |
|
13 | | -### Values to Fetch |
| 15 | +## Get the Redirect URI from Devtron |
14 | 16 |
|
15 | | -* clientID |
| 17 | +Before configuring Google as an SSO provider, |
| 18 | +* Ensure that the [Host URL](../../host-url.md) is correctly configured in Devtron. This is crucial because the Redirect URI is generated based on the Host URL. |
| 19 | +* You need to retrieve the Redirect URI from Devtron, which will be required in Google Cloud while setting up OAuth credentials. |
16 | 20 |
|
17 | | -* clientSecret |
| 21 | + * Log in to Devtron. |
| 22 | + * Navigate to **Global Configurations** → **SSO Login Services**. |
| 23 | + * Select **Google** as the authentication provider. |
| 24 | + * Enter the Host URL in the `URL` field. (This is essential to generate the correct Redirect URI.) |
| 25 | + * Copy the Redirect URI displayed in this section. You will need to enter this in Google Cloud. |
18 | 26 |
|
19 | | - 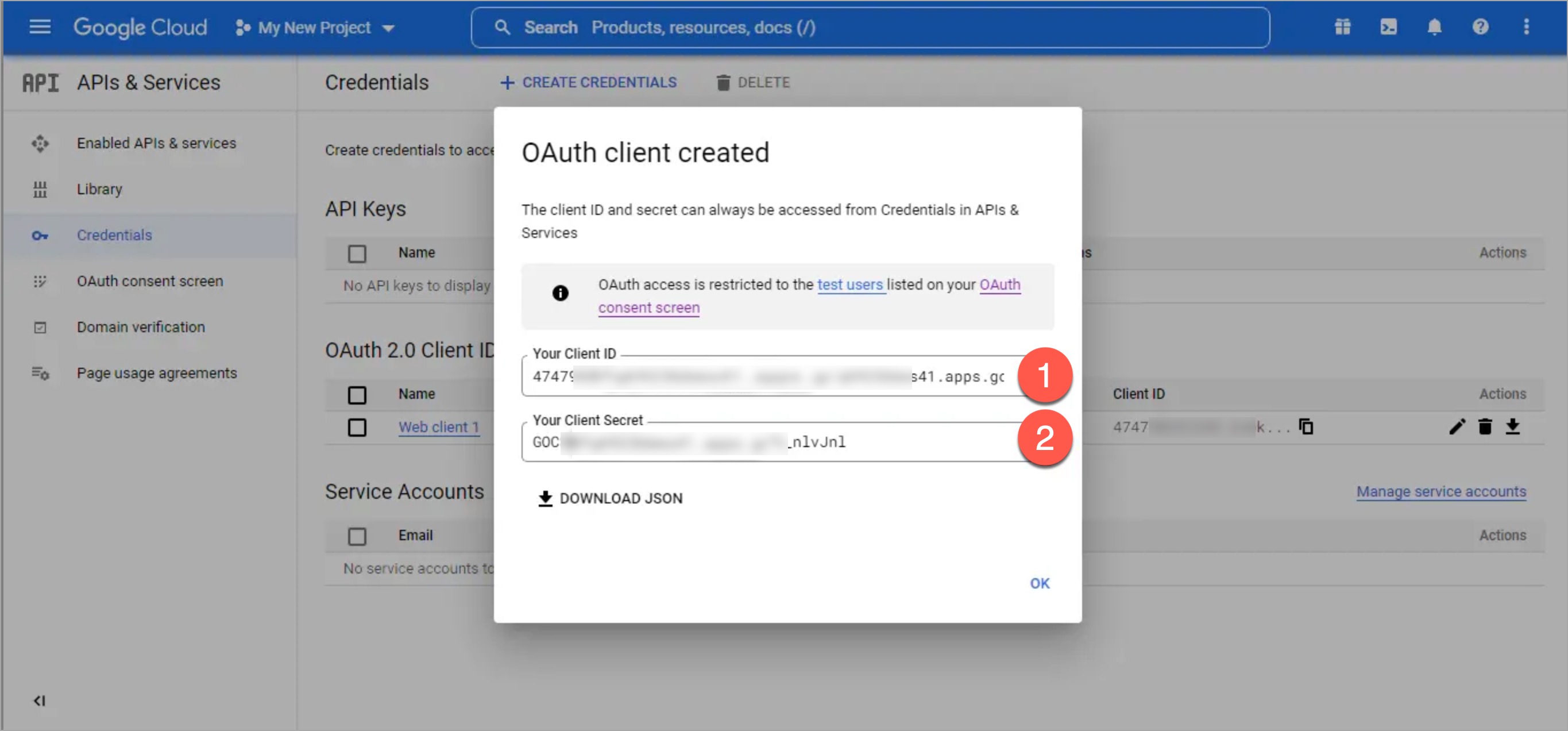 |
| 27 | + |
20 | 28 |
|
| 29 | +## Configure OAuth in Google Cloud Console |
21 | 30 |
|
22 | | -### Values to Provide |
| 31 | +The next step is to configure OAuth credentials in Google Cloud Console. This involves creating a Google OAuth Client ID and Client Secret, which will be used in Devtron for authentication. |
23 | 32 |
|
24 | | -* redirectURI (provided in SSO Login Services by Devtron) |
| 33 | +### To set up OAuth, follow these steps: |
25 | 34 |
|
26 | | - 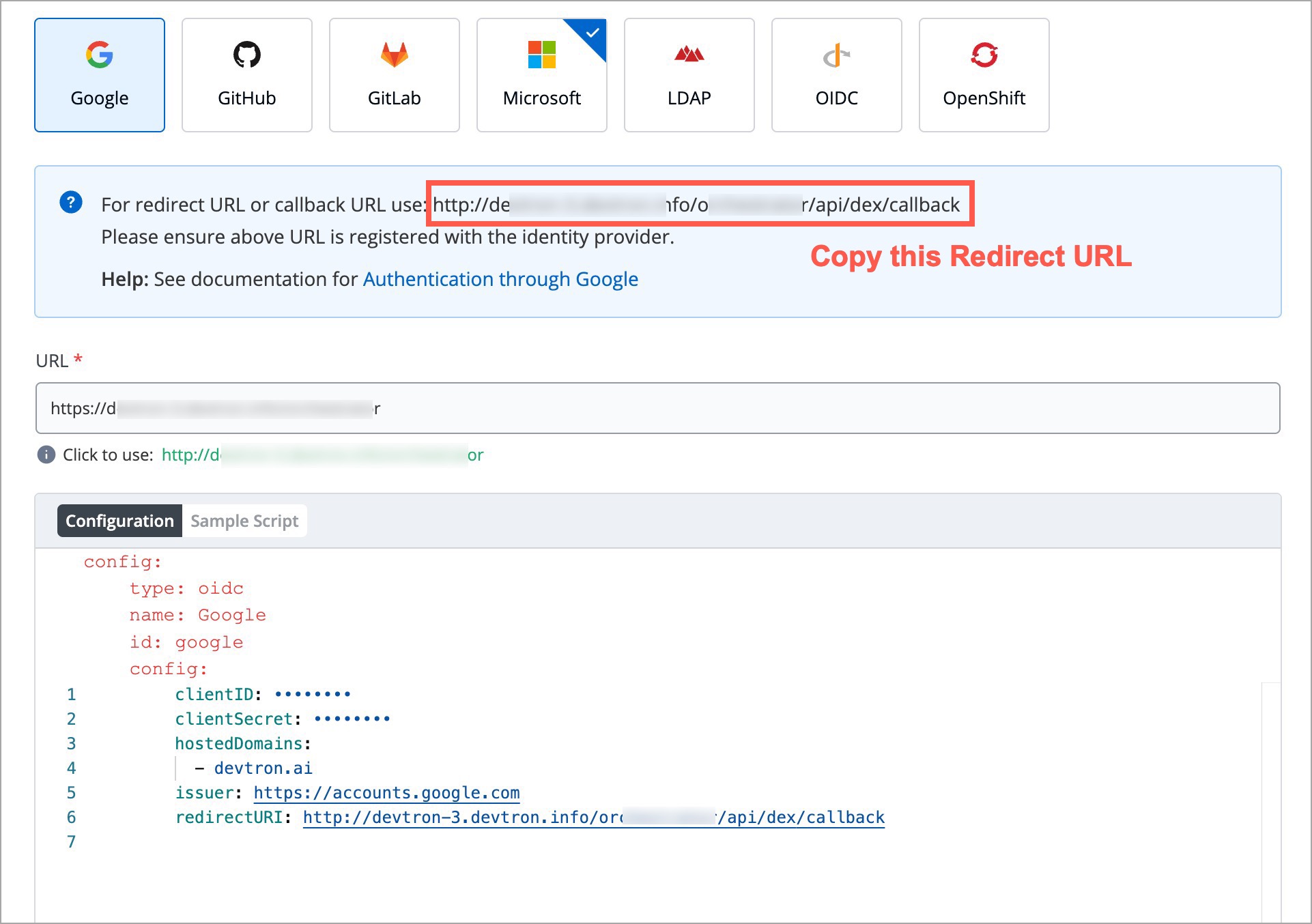 |
| 35 | +* Access [Google Cloud Console](https://console.cloud.google.com/) and create a new project or select an existing one. |
| 36 | +* Navigate to **APIs & Services** → **OAuth Consent Screen** and configure the required details as shown on the screen. |
| 37 | +* In **APIs & Services** → **Credentials**, create a new OAuth Client ID: |
| 38 | + * Select 'Web application' as the application type. |
| 39 | + * Paste the Redirect URI (copied from Devtron) under Authorized Redirect URIs. |
| 40 | +* Click **Create** to generate the Client ID and Client Secret. |
27 | 41 |
|
28 | | -  |
| 42 | +{% hint style="warning" %} |
| 43 | +Google SSO Requires a Valid Domain with HTTPS |
29 | 44 |
|
30 | | ---- |
| 45 | +Google does not support IP addresses as valid redirect URIs. You must use a valid domain name ([FQDN](https://en.wikipedia.org/wiki/Fully_qualified_domain_name)) accessible over HTTPS. |
31 | 46 |
|
32 | | -## Reference |
| 47 | +Examples of valid URIs: |
33 | 48 |
|
34 | | -* [View Google Documentation](https://developers.google.com/identity/gsi/web/guides/get-google-api-clientid) |
| 49 | +✅ https://devtron.example.com/api/dex/callback |
| 50 | + |
| 51 | +✅ https://auth.yourcompany.com/callback |
| 52 | + |
| 53 | +Examples of invalid URIs: |
| 54 | + |
| 55 | +❌ http://localhost:8080/callback |
| 56 | + |
| 57 | +❌ http://192.168.1.10/callback |
| 58 | +{% endhint %} |
| 59 | + |
| 60 | + |
| 61 | + |
| 62 | +You can see a new client ID is created in the **APIs & Services** → **Credentials**, under **OAuth 2.0 Client IDs** section. To obtain Client ID and Client Secret, click on the name (devtron-sso in our case) of the **OAuth 2.0 Client IDs** |
| 63 | + |
| 64 | + |
| 65 | + |
| 66 | +Copy the Client ID and Client Secret, as they will be required in Devtron’s SSO configuration. |
| 67 | + |
| 68 | + |
| 69 | + |
| 70 | +For a detailed step-by-step guide, refer to Google’s official documentation: [Get Google API Client ID](https://developers.google.com/identity/gsi/web/guides/get-google-api-clientid). |
| 71 | + |
| 72 | +## Configure Google SSO in Devtron |
| 73 | + |
| 74 | +The next step is to configure Devtron to use these credentials for authentication. For this, navigate back to **Global Configurations → SSO Login Services**, here you can already find a configuration template. |
35 | 75 |
|
36 | | -* [View Dex IdP Documentation](https://dexidp.io/docs/connectors/google/) |
| 76 | +## Configuration |
37 | 77 |
|
| 78 | + |
38 | 79 |
|
| 80 | +In the configuration,  |
39 | 81 |
|
| 82 | +* Enter the OAuth Credentials: |
| 83 | + * Paste the Client ID obtained from Google Cloud in the `clientID` field. |
| 84 | + * Paste the Client Secret obtained from Google Cloud in the `clientSecret` field. |
| 85 | +* Configure Hosted Domains (Optional): |
| 86 | + * If you want to restrict authentication to specific domains (e.g., only users from company.com can log in), add these under `hostedDomains` in Devtron. |
| 87 | + * If you want to allow all users with any valid Google account, remove the entire `hostedDomains` section from the configuration. |
| 88 | +* Enter the Redirect URI: |
| 89 | + * Copy the Redirect URI displayed in Devtron and paste the value in the `redirectURI` field. |
| 90 | +* Click **Update** to save the configuration, once saved, Google SSO is successfully configured |
| 91 | + |
| 92 | +{% hint style="warning" %} |
| 93 | +Although Google SSO is now set up, users will not be able to sign in unless they are explicitly added to Devtron with the necessary permissions. |
| 94 | +{% endhint %} |
| 95 | + |
| 96 | +## Important: Enable User Access After SSO Setup |
| 97 | + |
| 98 | +To ensure users can log in: |
| 99 | + |
| 100 | +* Go to **Global Configurations** → **Authorization** → **User Permissions**. |
| 101 | +* Click **Add User**. |
| 102 | + |
| 103 | + |
| 104 | + |
| 105 | +* Enter their email (matching their Google account). |
| 106 | +* Assign the required role. |
| 107 | +* Click **Save** to complete the setup. |
| 108 | + |
| 109 | +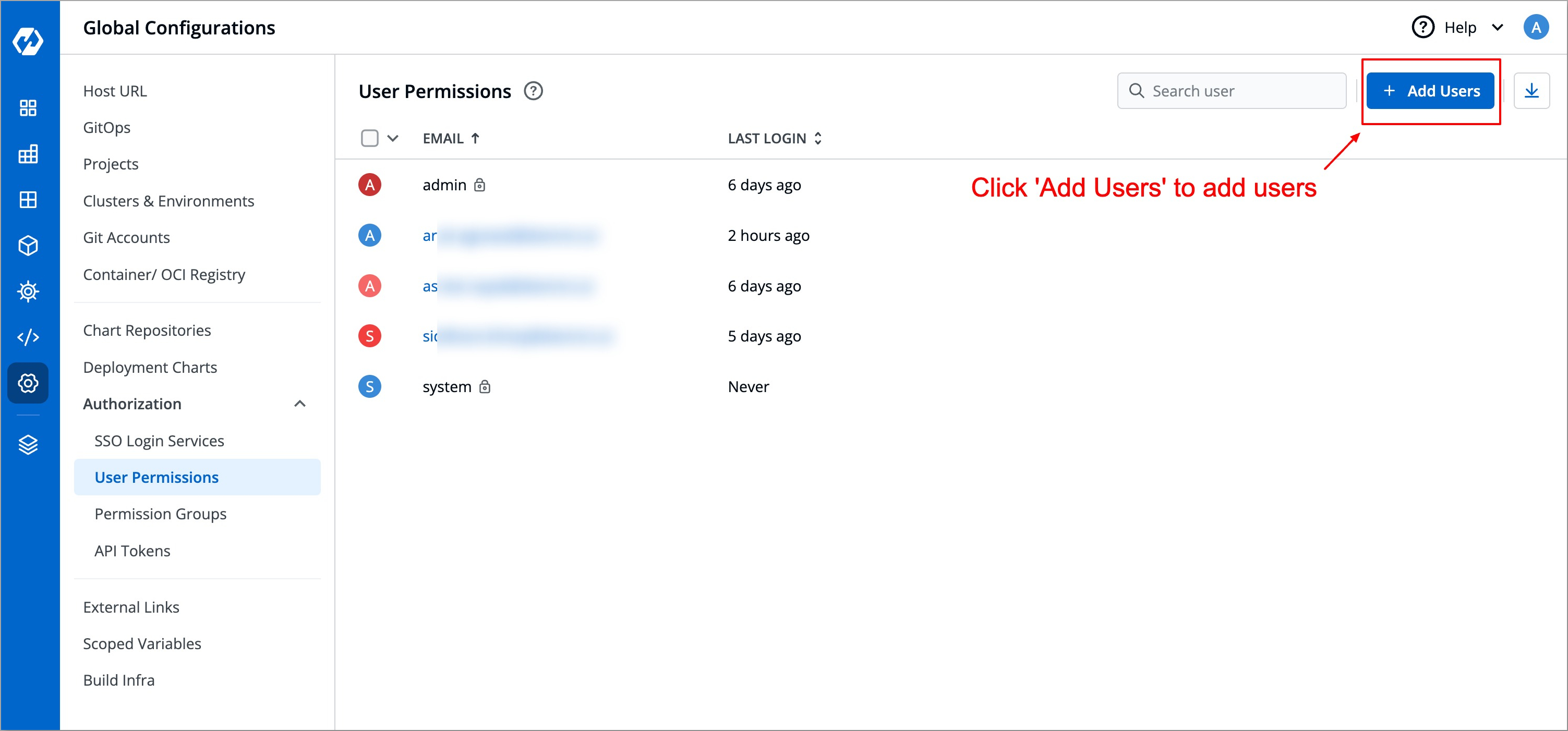 |
| 110 | + |
| 111 | +Once saved, Devtron will use Google OAuth for authentication, allowing users to log in using their Google accounts. |
| 112 | + |
| 113 | +For detailed steps on managing user permissions, refer to the [User Permissions Documentation](../user-access.md). |
| 114 | + |
| 115 | +## Reference |
| 116 | + |
| 117 | +* [View Google Documentation](https://developers.google.com/identity/gsi/web/guides/get-google-api-clientid) |
| 118 | +* [View Dex IdP Documentation](https://dexidp.io/docs/connectors/google/) |
0 commit comments