-
Notifications
You must be signed in to change notification settings - Fork 75
Home
Rekono combines other hacking tools and its results to execute complete pentesting processes against a target in an automated way. The findings obtained during the executions will be sent to the user via email or Telegram notifications and also can be imported in Defect-Dojo if an advanced vulnerability management is needed. Moreover, Rekono includes a Telegram bot that can be used to perform executions easily from anywhere and using any device.
- Combine hacking tools to create pentesting
processes - Execute pentesting
processes - Execute pentesting
tools - Review
findingsand receive them viaemailorTelegramnotifications - Use
Defect-Dojointegration to import the findings detected by Rekono - Execute
toolsandprocessesfromTelegram Bot -
Wordlistsmanagement
Do you ever think about the steps that you follow when you start pentesting? Probably you start performing some OSINT tasks to gather public information about the target. Then, maybe you run hosts discovery and ports enumeration tools. When you know what the target exposes, you can execute more specific tools for each service, to get more information and maybe, some vulnerabilities. And finally, if you find the needed information, you will look for a public exploit to get you into the target machine. I know, I know, this is an utopic scenario, and in the most cases the vulnerabilities are found due to the pentester skills and not by scanning tools. But before using your skills, how many time do you spend trying to get as information as possible with hacking tools? Probably, too much.
Why not automate this process and focus on find vulnerabilities using your skills and the information that Rekono sends you?
The
Rekononame comes from the Esperanto language where it means recon.
The main Rekono feature is the execution of external hacking tools, and it can be performed in two different ways: including them in pentesting processes or independently. Pentesting processes are groups of different tools and configurations that will be executed together automatically. For example, in the picture above, you can see one default process that includes all the supported tools in Rekono:

The pentesting processes can be created dynamically, by including only the hacking tools that the auditor needs for his purposes. This is possible because the dependencies between the different tool executions are established based on the inputs and the potential results for each one. For example, given a process that includes Nmap, SSH audit, CMSeeK and Metasploit, the executions will be launched in that order:
- Nmap: this execution will find hosts, ports and services exposed by the target.
- SSH audit: this execution will be executed on SSH services found by Nmap to identify vulnerabilities.
- CMSeek: this execution will be executed on HTTP services found by Nmap to identify CMS technologies and vulnerabilities.
- Metasploit: this execution will process all the CVE found by SSH audit and CMSeeK to look for known public exploits.
In this case, SSH audit and CMSeeK can be executed at the same time because there are no dependencies between them. Rekono uses an element called project to organize the different resources involved in the pentesting exercises: targets, executions, findings and auditors. As the projects group all the pentesting information, they are very useful to create specific metrics and to restrict the access to the resources. In the next picture, you can see the details for the project Demo:

Within one project, it’s possible to create all the targets included in the pentesting scope. They can be domain names, host address, network address or IP ranges:

Moreover, it’s possible to add more context information about the target, like known open ports, known technologies or known vulnerabilities. This information may be needed to execute some tools outside of pentesting processes. For example, Metasploit looks for known public exploits but it needs a CVE to perform the search, if it’s executed within a pentesting process the CVEs can be obtained from the previous executions, but if it’s executed alone, a known vulnerability is needed. In the following image you can see an example of this information:

After the target definition, it’s possible to execute processes or tools against them, by the creation of tasks following the next form:

As you can see, the task intensity can be configured. In the case of the pentesting processes, only the tools that support an equal or lower intensity than the configured one will be executed. Moreover, the tasks can be created with time configuration, so that they can be executed on a specific date, after a specific time or periodically. The last one is a very interesting feature, because it allows the automatic check of different targets, so the users will note if new vulnerabilities appear for those targets:


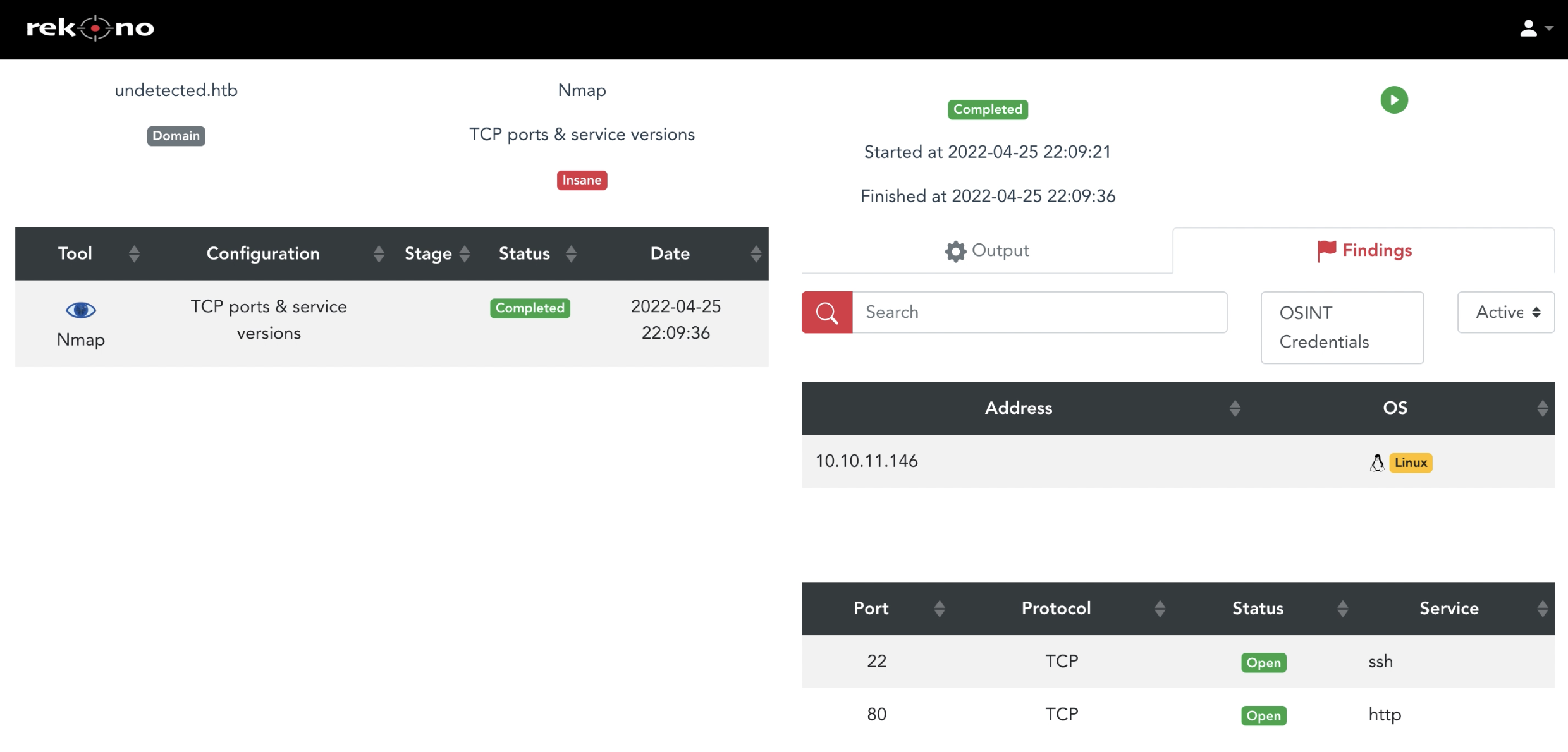
After requesting the execution, Rekono will redirect the user to the task page where it’s possible to review the execution progress and its results. In the next picture, we can see an Nmap execution:
In the case of the process executions, it’s possible to review the pending tool executions and the findings for each one. In the following example, there are some executions already completed and two Dirsearch executions still running:

Moreover, if the auditor needs to review the original tool output, it’s possible by clicking on the Output tab. In the next picture, the original Nmap output is shown:

At project level, it’s possible to review the execution history in the tasks page. As you can see, this includes the target, executed tool or project, status, auditor who requests the execution and the execution date:

Finally, the findings identified during the execution of pentesting tasks against the targets, can be reviewed directly in the platform at project level:

This page displays all the findings information by target and includes multiple filtering options. At first, this page only displays hosts and findings without relations with other findings, like OSINT data. Then, the user can select one finding and the page will show the related findings. For example, if the user clicks on one host, the page will show the ports exposed by this host; then, if the user selects one port, the page will show the technologies and vulnerabilities found in that port. Moreover, when the user clicks on one finding, the details of these findings are shown in the bottom, for example, when is the finding detected, by what tool and other specific finding details.
The supported tools by Rekono can be reviewed in the Tools page, where the user can review the configurations and intensities supported by each tool, and the details about the required input parameters for its execution and its potential results. Moreover, as in the processes page, the user can order tool executions from the tool page:

Nowadays, Rekono supports the following 17 hacking tools:
| Tool | Stage | Description |
|---|---|---|
| theHarvester | OSINT | Get OSINT information like subdomains or emails |
| EmailHarvester | OSINT | Get emails from public sources |
| EmailFinder | OSINT | Get emails from public sources |
| Nmap | Host discovery and port enumeration | Get up hosts, open ports and details about running services |
| Sslscan | Service analysis | Analysis of vulnerabilities in TLS configuration |
| SSLyze | Service analysis | Analysis of vulnerabilities in TLS configuration |
| SSH Audit | SSH service analysis | Analysis of vulnerabilities in SSH services |
| SMBMap | SMB service analysis | Enumeration of SMB shares |
| Dirsearch | HTTP service analysis | Enumeration of endpoints in web services |
| GitLeaks & GitDumper | HTTP service analysis | Get code from exposed Git repositories and then find hardcoded credentials in the source code |
| Log4j Scanner | HTTP service analysis | Check if a web service is vulnerable to Log4Shell |
| CMSeeK | HTTP service analysis | Get information about the CMS used by a web service |
| OWASP JoomScan | HTTP service analysis | Analysis of web services that use Joomla as CMS |
| OWASP ZAP | HTTP service analysis | Analysis of vulnerabilities in web services |
| Nikto | HTTP service analysis | Analysis of vulnerabilities in web services |
| SearchSploit | Exploitation | Look for public exploits |
| Metasploit | Exploitation | Look for public exploits |
Rekono platform includes three clients: web application, command line interface (CLI) and Telegram bot. The Rekono bot makes the pentesting process easy, making the platform available for all users from all devices, including the operations from the target’s creation to the findings revision.
At first, the auditor can create a target using the /newtarget command:

Then it’s possible to request the execution of tools or processes against this target using the /tool or /process commands as shown in the following screenshots:


As you can see, the bot asks the user for the execution details: target, tool or process depending on the command, configuration to apply if it’s a tool execution, wordlist to apply if it’s needed by some tool and the execution intensity. Then the bot asks the user to confirm the task execution, and finally it creates the task.
After the executions, if the user has enabled the Telegram notifications, he will receive the findings details directly in the Telegram chat. In the next picture, you can see the results of an Nmap execution:

Of course, the Rekono bot is protected by authentication, based on a one-time token that should be used to link Telegram chats with Rekono users.
Rekono supports different notification preferences, based on the content and the platform used to receive the notifications. At first, it’s possible to configure what execution results the user wants to receive: all the results of his projects or only his own executions. Then, it’s possible to configure the email notifications or Telegram notifications (already seen in the Telegram bot section). In the next picture, you can see the configuration options:

In the following pictures, you can see an example of user notification via email:

Rekono supports three different user roles: administrators, auditors and readers. The user notifications can be very useful for all of them due to different reasons:
- Administrators are often people with responsibilities in the pentesting exercises, so that they could be interested in being up to date about the work progress.
- Auditors need user notifications to know the latest findings of their automatic analysis, so that they can use this information during their manual testing.
- Readers are often people in charge of follow up vulnerabilities or the target system responsible, so they should be informed about the security situation.
The findings obtained after task executions are processed automatically by Rekono: CVE information is completed using the NVD NIST API, user notifications are sent and findings are imported in Defect-Dojo when the integration is enabled for these Rekono projects. Defect-Dojo is a vulnerability management platform where:
- The findings can be stored to keep traceability of the security situation of the products
- The findings can be reported to the product responsible
- Tickets in bug trackers like JIRA can be created from the findings
- The security risk related to the findings can be treated in a proper way For example, in the next picture you can see the summary information for one Defect-Dojo product:

The findings can be reviewed directly in the Rekono platform, but it is an automation tool, it isn’t a vulnerability management tool, and sometimes a more advanced vulnerability management is needed. So, Rekono includes an integration with Defect-Dojo in an automated way at project level. Defect-Dojo integration is highly customizable, allowing the user to decide how the findings should be imported in the platform and creating the Defect-Dojo products and engagements when needed. In the next picture, the Defect-Dojo integration form can be seen:

The most comfortable way of working is enabling the automatic creation of products and engagements, to let Rekono deal with all Defect-Dojo elements. Remember that the findings only will be imported when the synchronization is enabled at project level. Rekono always imports the original tool outputs in Defect-Dojo when it’s supported, so the original tool tests will appear in Defect-Dojo. In the following image are two Nmap tests imported in Defect-Dojo from Rekono integration:

As the name says, wordlists are lists of words that can be used during pentesting processes to perform enumeration or brute force tasks. Rekono can execute tools that may need wordlists to work correctly, for example, Dirsearch, to find exposed endpoints in web services. For that reason, Rekono also includes wordlist management features directly in the platform, so users can create their own wordlists and upload them to Rekono. All the pentesting resources in Rekono, including wordlists, are shared between all users, so everyone can access the most useful wordlists. By default, Rekono supports some Kali Linux wordlists, shown in the next picture:

Some of this content has been published by PenTest Magazine at October 2022