The Simple MongoDB Honeypot Server is a Python-based monitoring tool designed to detect and analyze unauthorized MongoDB access attempts. Built on Twisted, it emulates key parts of the MongoDB wire protocol (OP_MSG / OP_QUERY) and logs attacker reconnaissance and authentication activity.
-
MongoDB Wire Protocol Emulation
- Parses and responds to OP_MSG (2013) and OP_QUERY (2004).
- Supports modern handshake commands:
hello/ismaster. - Replies in both OP_MSG and legacy OP_REPLY formats depending on client behavior.
-
Comprehensive Logging (kept compatible with existing logs)
- Connection events (
[CONN]) - Command/metadata extraction (
[CMD]) - Authentication attempt capture (
[AUTH])
- Connection events (
-
Raw Payload Telemetry (for zero-day / fuzzing visibility)
- Logs raw inbound wire bytes as hex (
[RAW]) with message metadata (opCode, requestId, responseTo, length). - Payload dumps are truncated to the first 4096 bytes to keep logs manageable.
- Logs raw inbound wire bytes as hex (
-
Safer Protocol Handling
- Strict message framing and size validation to avoid memory blowups.
- Rejects malformed messages (invalid header or impossible lengths).
-
Configurable Deployment
- Bind host/port and advertised MongoDB version.
- Python 3.9+
- Twisted
- pymongo (provides
bson)
git clone https://github.com/0xNslabs/mongodb-honeypot.git
cd mongodb-honeypot
pip install twisted pymongopython3 mongodb.py --host 0.0.0.0 --port 27017 --version "8.0.9"- Binds to all interfaces (
0.0.0.0) - Listens on MongoDB default port (
27017) - Presents as MongoDB version
8.0.9
Logs are written to mongodb_honeypot.log.
[CONN]: Connection events (client IP/port)[CMD]: Parsed command and client metadata (application/driver/OS) in a JSON-like dict[AUTH]: SASL/SCRAM authentication attempt capture (username + client nonce when present)[RAW]: Raw inbound MongoDB wire message dump (hex), truncated to 4096 bytes
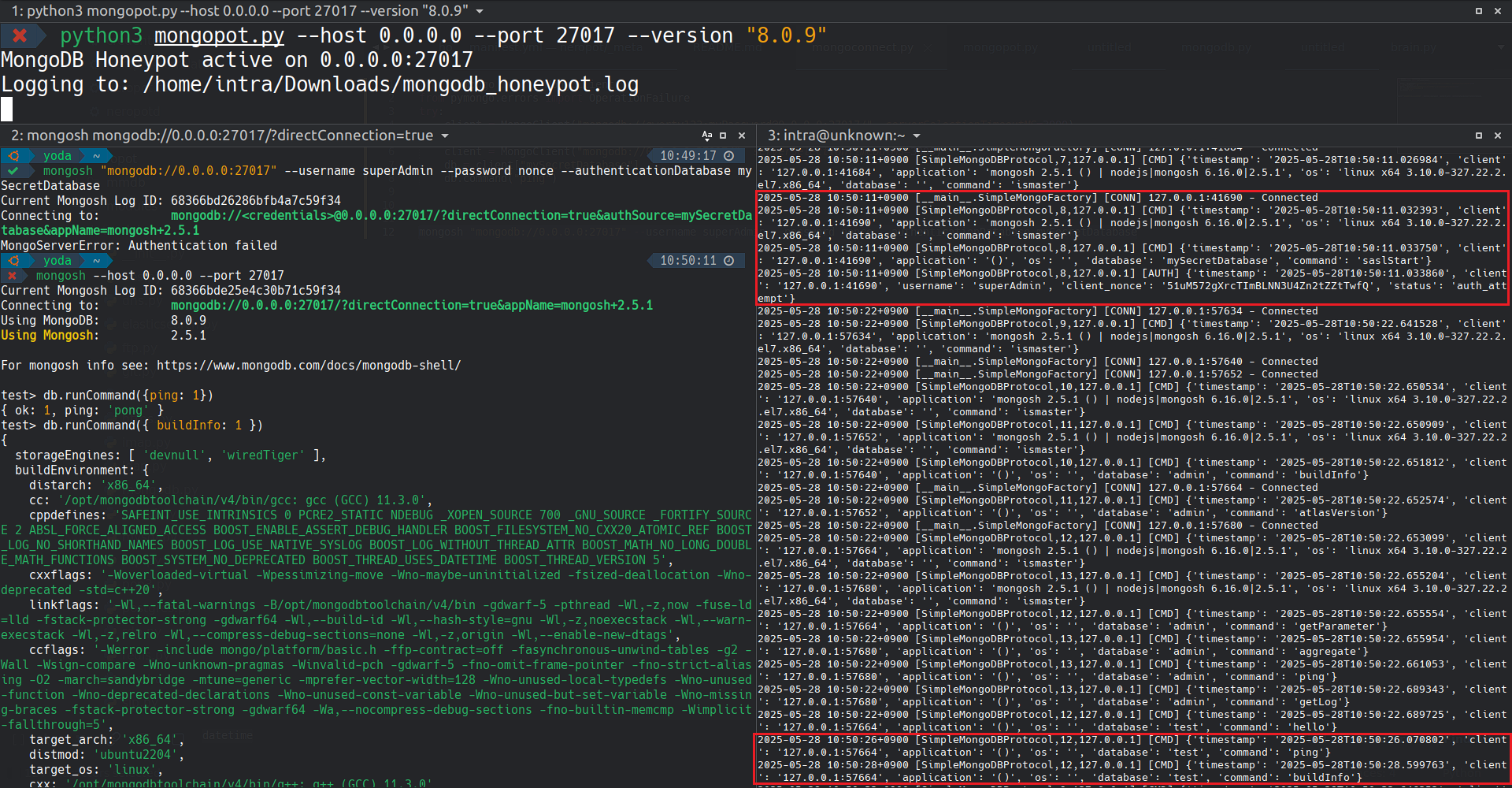
Example of the honeypot capturing authentication attempts and client fingerprinting
- DNS Honeypot - Monitors DNS interactions.
- FTP Honeypot - Simulates an FTP server.
- LDAP Honeypot - Mimics an LDAP server.
- HTTP Honeypot - Monitors HTTP interactions.
- HTTPS Honeypot - Monitors HTTPS interactions.
- MongoDB Honeypot - Simulates a MongoDB database server.
- NTP Honeypot - Monitors Network Time Protocol interactions.
- PostgreSQL Honeypot - Simulates a PostgreSQL database server.
- SIP Honeypot - Monitors SIP (Session Initiation Protocol) interactions.
- SSH Honeypot - Emulates an SSH server.
- TELNET Honeypot - Simulates a TELNET server.
- Caution: Deploy only in controlled environments. Avoid exposing it directly to the public internet without proper containment and monitoring.
- Compliance: Ensure your use complies with local laws, organizational policy, and ethical guidelines.
This project is available under the MIT License. See the LICENSE file for more information.