The Simple PostgreSQL Honeypot Server is a lightweight, low-interaction honeypot intended to capture and analyze PostgreSQL reconnaissance and authentication attempts. Written in Python using Twisted, it emulates enough of the PostgreSQL wire protocol to record startup parameters (e.g., user/database), password attempts, and optional raw byte streams for anomaly and potential zero-day protocol research.
- Low-Interaction Honeypot: Emulates PostgreSQL startup + authentication to capture credential attempts.
- Protocol-Aware Parsing: Handles framed PostgreSQL messages (startup + auth) and common SSL probe requests.
- Raw Bytes Telemetry (Optional): Logs raw received and sent bytes in hex for deeper protocol analysis.
- Configurable Settings: Bind host/port via command-line flags.
- Extensive Logging: Records new connections, startup parameters, and password attempts in a single log file.
- Python 3.x
- Twisted (
pip install twisted)
git clone https://github.com/0xNslabs/postgresql-honeypot.git
cd postgresql-honeypot
pip install twistedBy default, raw byte logging is enabled.
python3 postgresql.py --host 0.0.0.0 --port 5432Disable raw byte logging (recommended if you expect high traffic and want smaller logs):
python3 postgresql.py --host 0.0.0.0 --port 5432 --no-raw-bytes-log(You can also explicitly enable it with --raw-bytes-log.)
Logs are written to postgresql_honeypot.log in the project directory and include:
- New connection events (client IP/port)
- Startup parameters (username, database)
- Password attempts
- Raw byte telemetry (hex), when enabled:
PostgreSQL RAW RECV: ...PostgreSQL RAW SEND: ...
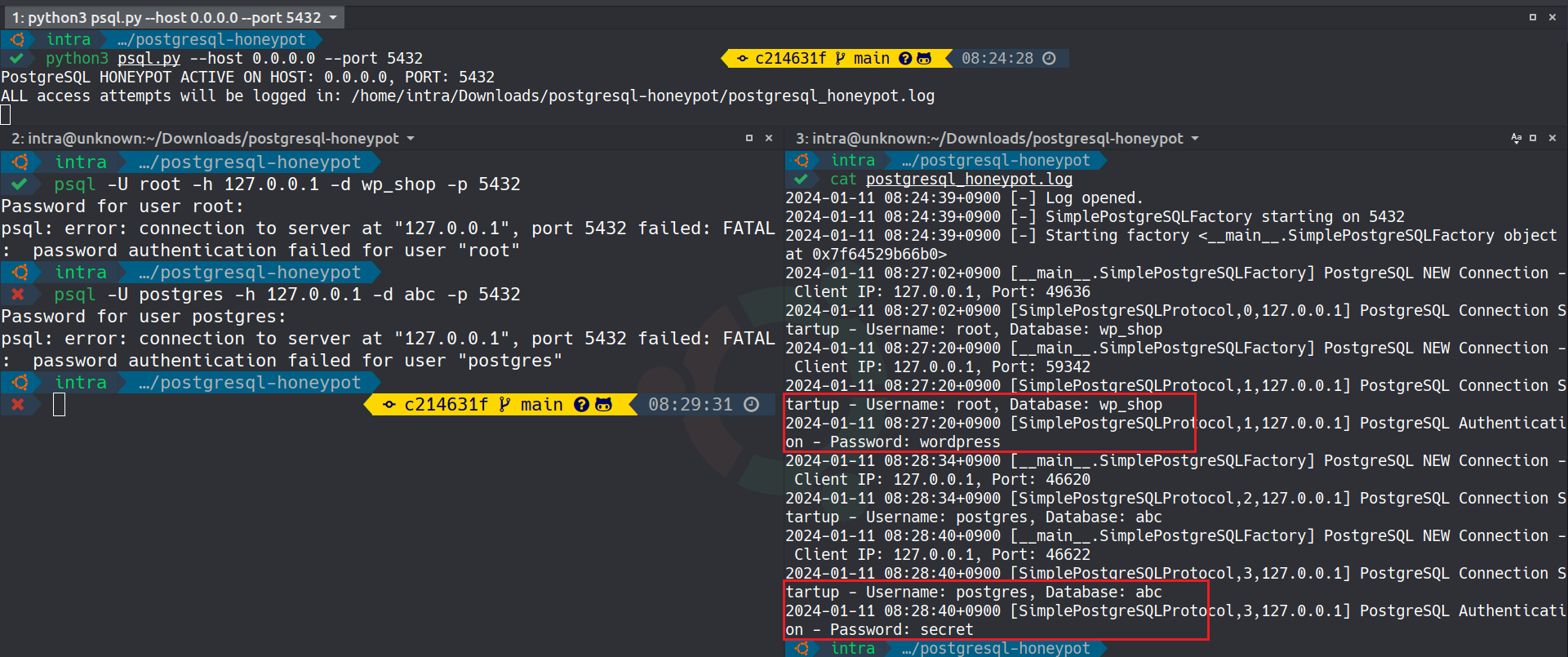 Example capture of PostgreSQL login attempts.
Example capture of PostgreSQL login attempts.
- DNS Honeypot
- FTP Honeypot
- LDAP Honeypot
- HTTP Honeypot
- HTTPS Honeypot
- MongoDB Honeypot
- NTP Honeypot
- PostgreSQL Honeypot
- SIP Honeypot
- SSH Honeypot
- TELNET Honeypot
- Caution: Run honeypots in a controlled environment (segmented network, monitoring, no sensitive assets).
- Compliance: Ensure your deployment and data retention comply with applicable laws and internal policies.
This project is distributed under the MIT License. See LICENSE for details.