Introduction • Attacks • Features • Installation • Usage
This tool is designed for security researchers and penetration testers to analyze and exploit vulnerabilities in Wi-Fi networks. It provides an intuitive interface with a wide range of automated and manual attack techniques to test WPA/WPA2, WPS, and WEP security. With support for both 2.4 GHz and 5 GHz networks, detailed logging and customizable attack options, it offers flexibility for different testing scenarios. This is not a professional tool.
If you find an error, please open an issue (you can write it in english or spanish, as you want).
- DoS (optional handshake capture):
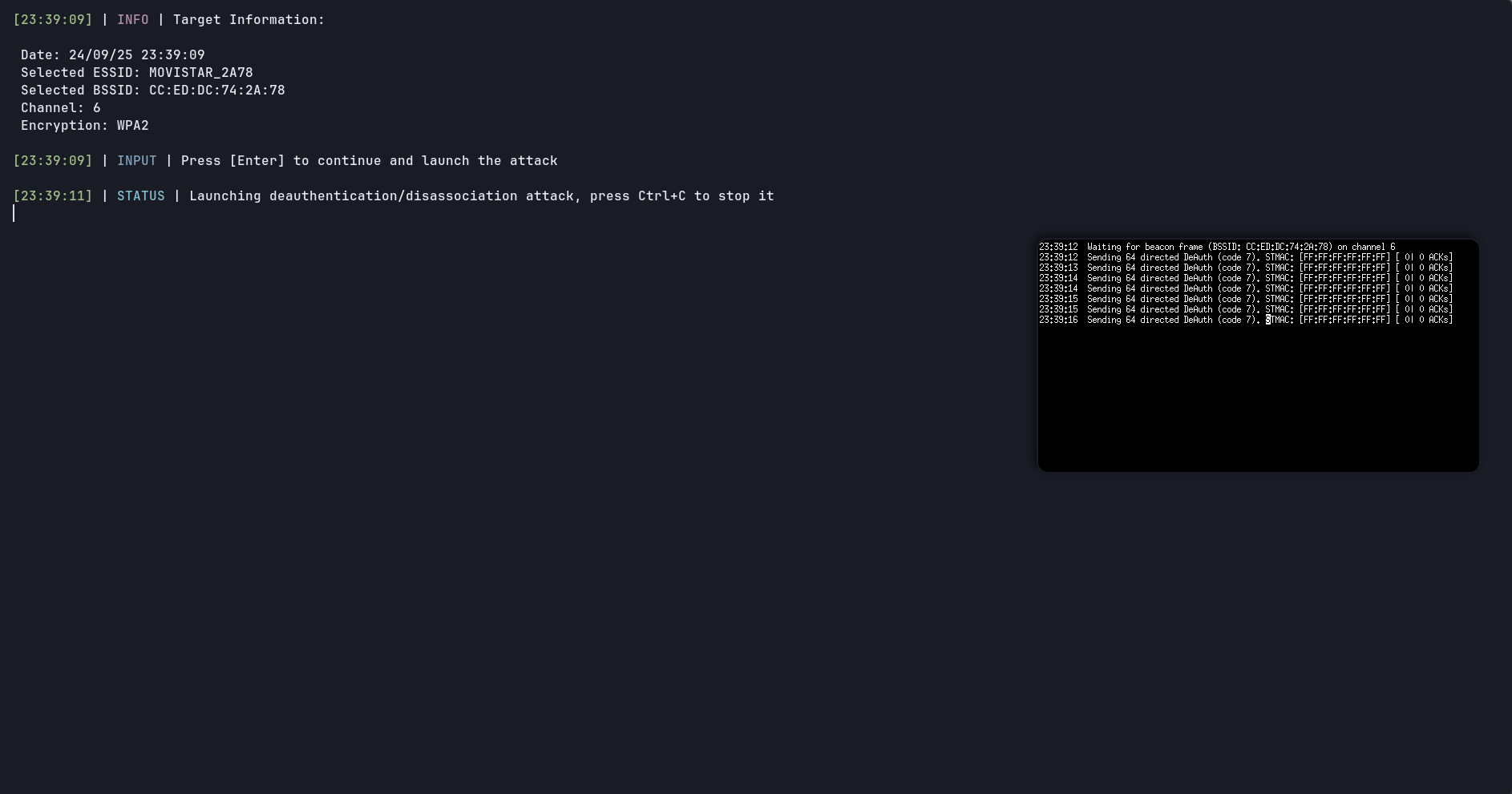
- Deauthentication/Disassociation attack
- WIDS Confusion attack
- Authentication attack
- Beacon Flood attack
- TKIP attack (Michael Shutdown Exploitation)
- WPS:
- Pixie Dust attack
- PIN Bruteforce attack
- Null Pin attack
- WEP:
- ARP Replay attack
- HIRTE attack
- Caffe Latte attack
- Fake Authentication attack
- Handshake:
- WPA handshake attack
- PMKID handshake attack
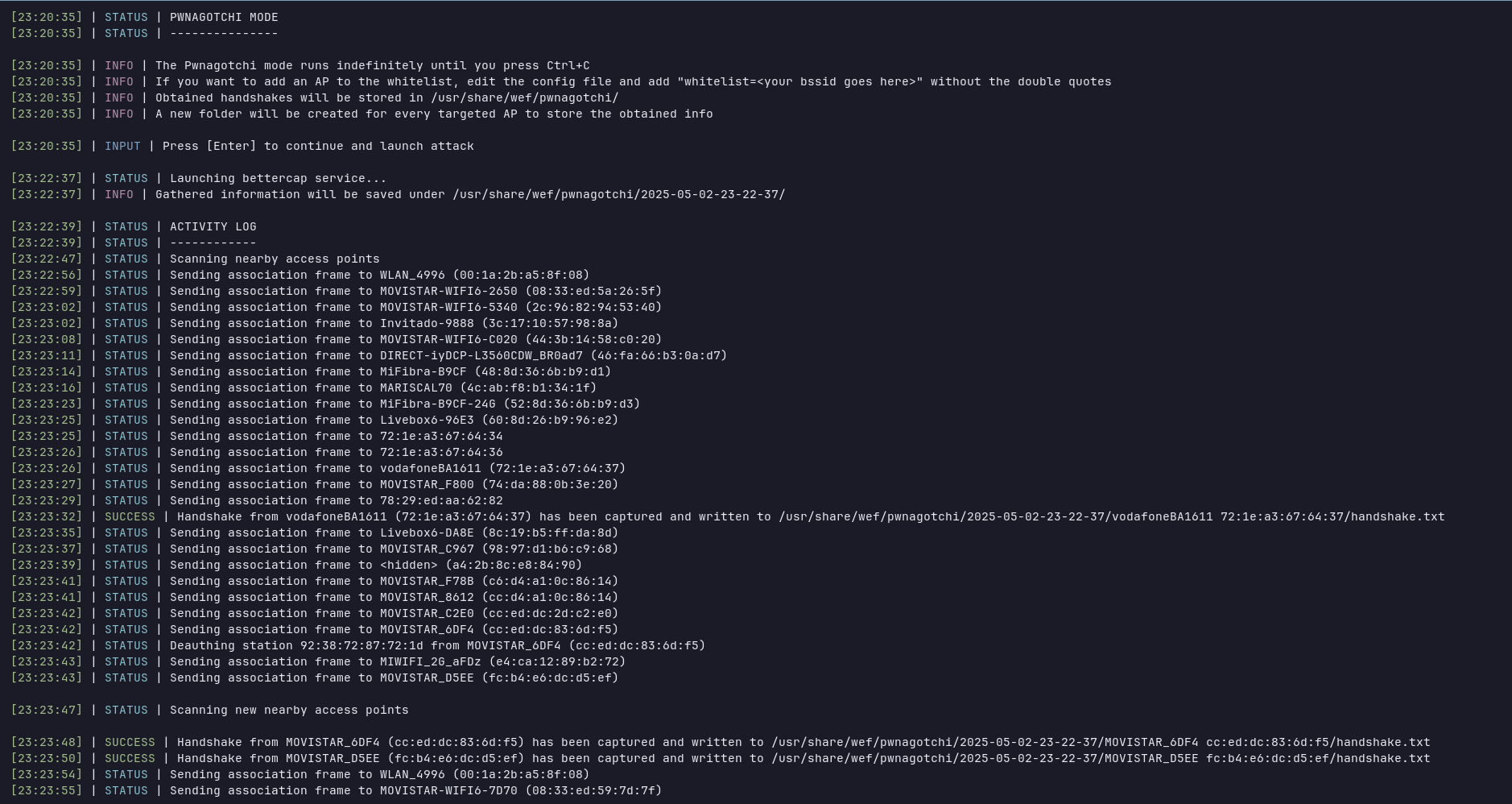
- Pwnagotchi mode
- Rogue AP:
- Evil Twin attack
- BSSID spoofing
- Karma mode
- Enterprise WPA supported
- Deauth supported
- Evil Twin attack
- Other attacks:
- Automatic attack mode (Auto PWN)
- WPA3 dictionary attack
All the mentioned attacks/techniques are explained here on the Wiki
This are some of the most notable features:
☑️ WPA/WPA2/WPA3, WPS, WEP, Rogue-AP, and Handshake Attacks
☑️ Automatic attack mode based on the features of the AP
☑️ Automatic handshake capture
☑️ Online and offline handshake cracking
☑️ Simple login template for Evil Twin attack (multiple languages supported)
☑️ Toggle monitor mode and view information about the network interface (frequencies, chipset, etc.)
☑️ 2.4 GHz and 5 GHz supported
☑️ Informative reports using HTML templates
☑️ Standalone script
☑️ English and spanish supported
As root
git clone --depth 1 https://github.com/D3Ext/WEF
cd WEF
bash wefTake a look at the Wiki where I have more info about the tool
Common usage of the framework (your interface may have other name)
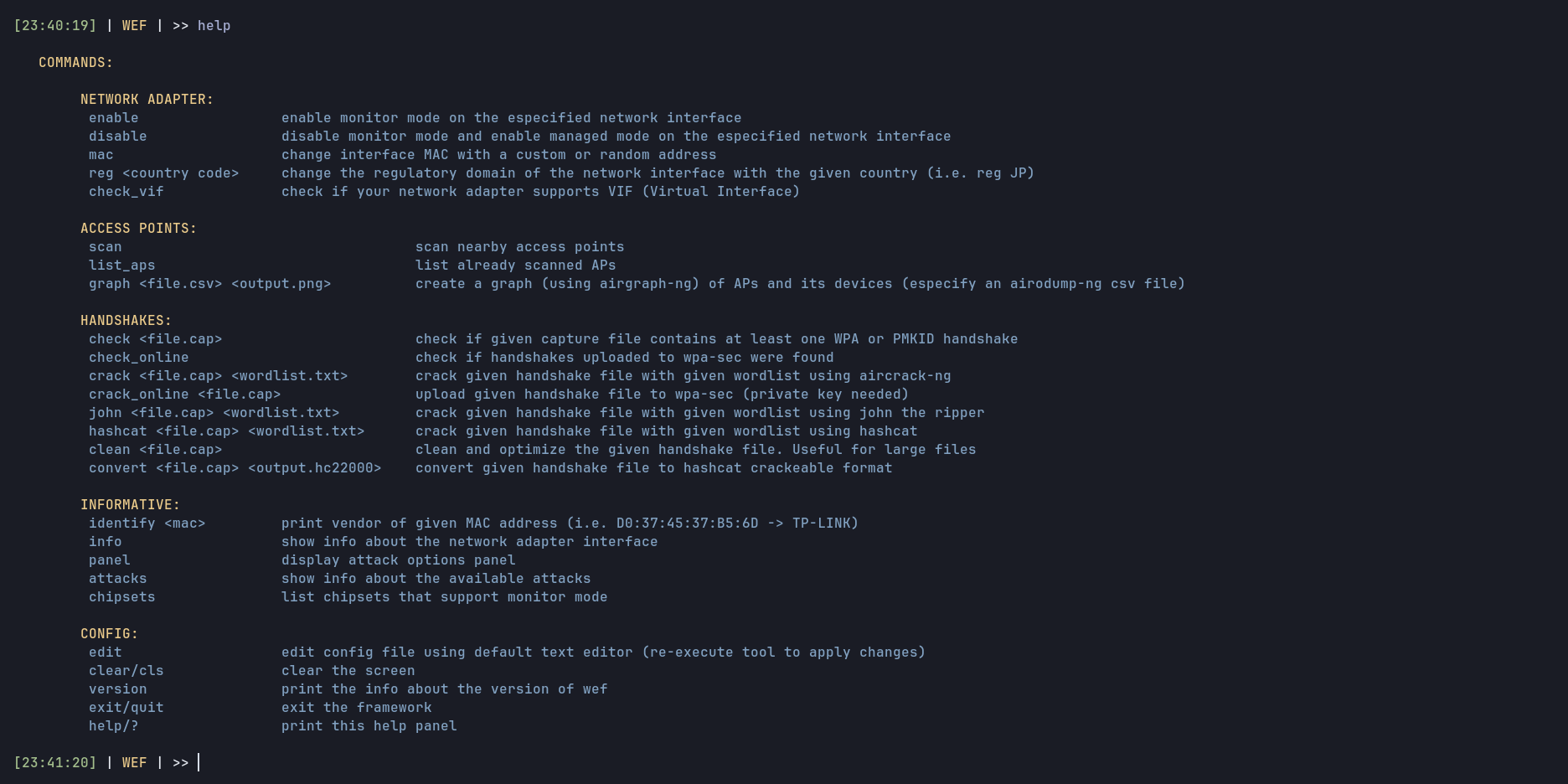
wef -i wlan0Help panel
__ _____ ___
\ \ / / __| __|
\ \/\/ /| _|| _|
\_/\_/ |___|_|
[WEF] WiFi Exploitation Framework 1.6
[*] Interfaces:
wlan0
Required parameters:
-i, --interface) The name of your network adapter interface in managed mode
Optional parameters:
-h, --help) Show this help panel
--version) Print the version and exit
See here for more information about how to use the tool and other related topics
- Custom Evil Twin templates based on target AP vendor (TP-Link, Netgear, etc)
- Even more languages for Evil Twin templates
- More WPA3 attacks: Downgrade, Dragondrain
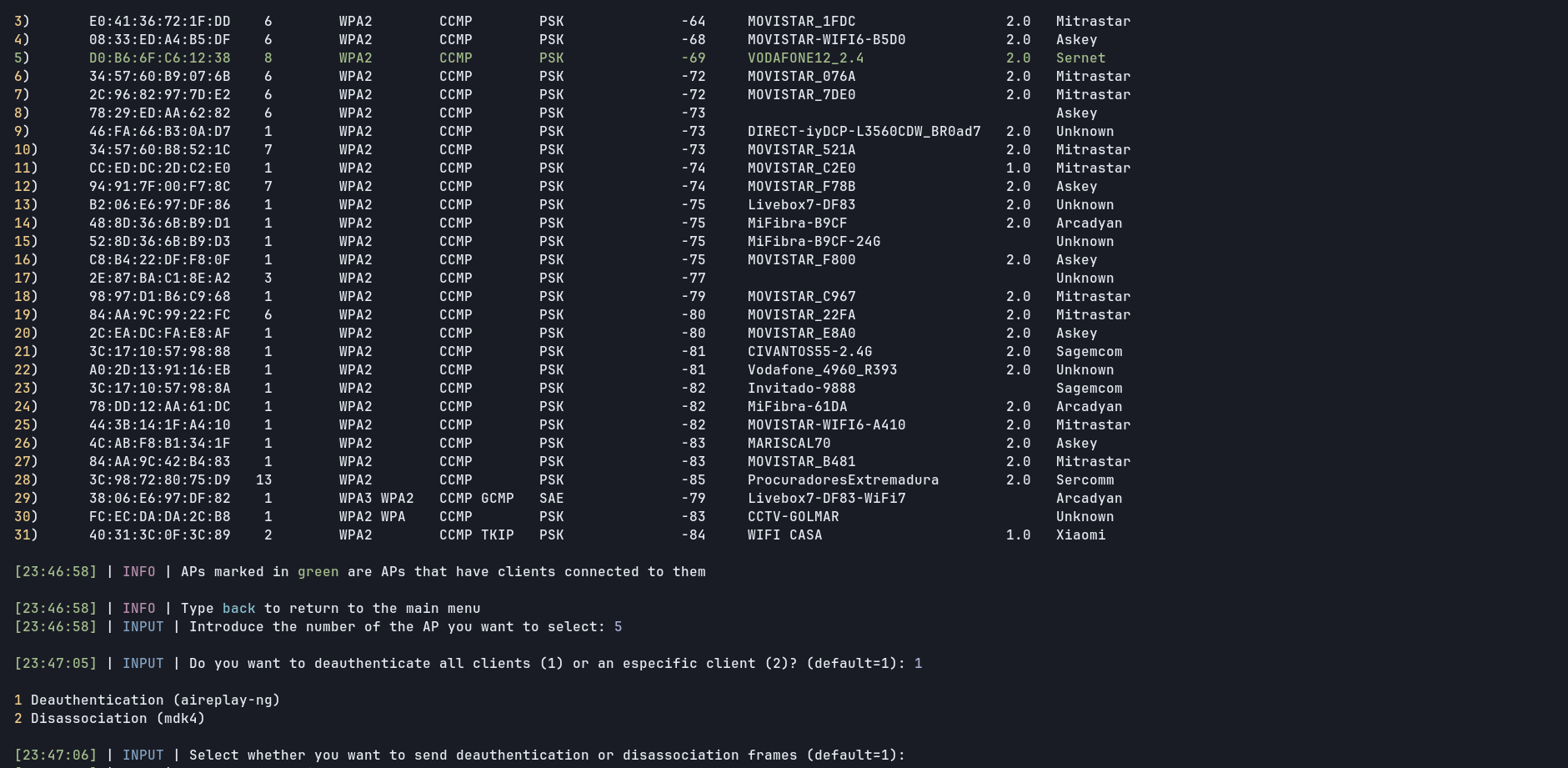
Sort APs by default by power to show which APs are closerWEF now works as a standalone scriptDisassociation is now supported alongside deauthenticationVendors are no longer parsed from a local fileAPs scanning has been improved, now APs with clients are marked in green colourEvil Twin now supports PMKID handshake to check captured passwordsMAC randomization/spoofing improvedFilters for WPS and WPA3 when scanning APsMost attacks were reworked and/or improved, new options are availableGraphical session and windows were reworkedNon-Graphical usage has been improvedAutomatic dependencies installation on main distrosDeep testing on supported distros (Manjaro, Fedora, Parrot, Debian, etc)Requirements were updated. Some more were added although the should be installed on most distrosWPA3 attack optimizedNow certificate files needed for Enterprise Evil Twin are generated automaticallyMore languages supported on Evil Twin templates (czech, danish and romanian)Now wordlists are not needed anymore as dependenciesBetter error handling for most scenariosMultiple bug fixes
See CHANGELOG.md
https://github.com/aircrack-ng/aircrack-ng
https://github.com/aircrack-ng/mdk4
https://github.com/v1s1t0r1sh3r3/airgeddon
https://github.com/FluxionNetwork/fluxion
https://github.com/P0cL4bs/wifipumpkin3
https://github.com/s0lst1c3/eaphammer
https://github.com/derv82/wifite2
https://github.com/wifiphisher/wifiphisher
https://github.com/ZerBea/hcxtools
https://github.com/ZerBea/hcxdumptool
https://github.com/Tylous/SniffAir
https://github.com/blunderbuss-wctf/wacker
https://github.com/evilsocket/pwnagotchi
https://github.com/koutto/pi-pwnbox-rogueap
https://github.com/koutto/pi-pwnbox-rogueap/wiki/01.-WiFi-Basics
The creator has no responsibility for any kind of illegal use of the project.
This project is under MIT license
Copyright © 2025, D3Ext