-
Notifications
You must be signed in to change notification settings - Fork 69
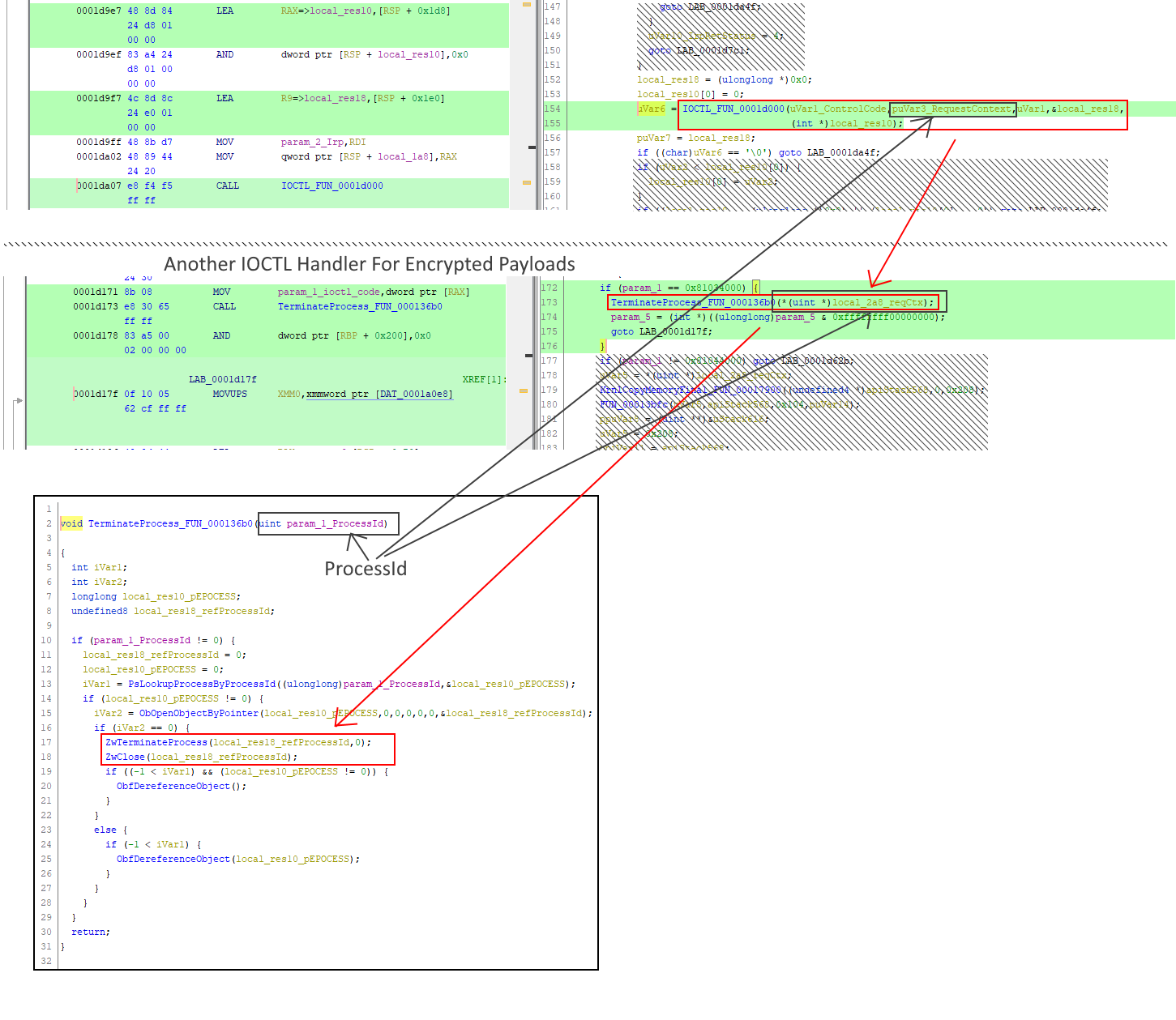
Terminate Process
Kento Oki edited this page Oct 26, 2020
·
4 revisions
The driver has a vulnerable ioctl code for terminating process, with a specific process id.
It eventually calls ZwTerminateProcess in the vulnerable driver context (ring-0).
The ioctl code is 0x81034000 as you can see:
PAGE:FFFFF800188CD0F9 cmp ebx, 81034000h
PAGE:FFFFF800188CD0FF jz short loc_FFFFF800188CD16CPAGE:FFFFF800188CD16C loc_FFFFF800188CD16C: ; CODE XREF: sub_FFFFF800188CD000+FF↑j
PAGE:FFFFF800188CD16C mov rax, [rsp+30h]
PAGE:FFFFF800188CD171 mov ecx, [rax]
PAGE:FFFFF800188CD173 call sub_FFFFF800188C36A8
PAGE:FFFFF800188CD178 and dword ptr [rbp+1D0h+arg_20], 0and the sub_FFFFF800188C36A8 is in .text segment:
.text:FFFFF800188C36B0 sub_FFFFF800188C36B0 proc near ; CODE XREF: sub_FFFFF800188C36A8↑j
.text:FFFFF800188C36B0 ; sub_FFFFF800188C4600+27↓p
.text:FFFFF800188C36B0 ; DATA XREF: ...
.text:FFFFF800188C36B0
.text:FFFFF800188C36B0 var_38 = qword ptr -38h
.text:FFFFF800188C36B0 var_30 = byte ptr -30h
.text:FFFFF800188C36B0 var_28 = qword ptr -28h
.text:FFFFF800188C36B0 var_18 = byte ptr -18h
.text:FFFFF800188C36B0 arg_0 = qword ptr 8
.text:FFFFF800188C36B0 Object = qword ptr 10h
.text:FFFFF800188C36B0 Handle = qword ptr 18h
.text:FFFFF800188C36B0 arg_18 = qword ptr 20h
.text:FFFFF800188C36B0
.text:FFFFF800188C36B0 ; __unwind { // __C_specific_handler
.text:FFFFF800188C36B0 test ecx, ecx // if (param1_processid != NULL)
.text:FFFFF800188C36B2 jz locret_FFFFF800188C3779
.text:FFFFF800188C36B8 mov rax, rsp
.text:FFFFF800188C36BB mov [rax+8], rbx
.text:FFFFF800188C36BF mov [rax+20h], rsi
.text:FFFFF800188C36C3 push rdi
.text:FFFFF800188C36C4 sub rsp, 50h
.text:FFFFF800188C36C8 xor ebx, ebx
.text:FFFFF800188C36CA mov dil, 1
.text:FFFFF800188C36CD mov [rax-18h], dil
.text:FFFFF800188C36D1 mov [rax+18h], rbx
.text:FFFFF800188C36D5 mov [rax+10h], rbx
.text:FFFFF800188C36D9 mov ecx, ecx
.text:FFFFF800188C36DB lea rdx, [rax+10h]
.text:FFFFF800188C36DF call PsLookupProcessByProcessId // <- Lookup _EPROCESS
.text:FFFFF800188C36E4 movzx esi, dil
.text:FFFFF800188C36E8 test eax, eax // if (_EPROCESS != NULL)
.text:FFFFF800188C36EA cmovs esi, ebx
.text:FFFFF800188C36ED mov [rsp+58h+var_18], sil
.text:FFFFF800188C36F2 mov rcx, [rsp+58h+Object]
.text:FFFFF800188C36F7 test rcx, rcx
.text:FFFFF800188C36FA jz short loc_FFFFF800188C376A
.text:FFFFF800188C36FC lea rax, [rsp+58h+Handle]
.text:FFFFF800188C3701 mov [rsp+58h+var_28], rax
.text:FFFFF800188C3706 mov [rsp+58h+var_30], bl
.text:FFFFF800188C370A mov [rsp+58h+var_38], rbx
.text:FFFFF800188C370F xor r9d, r9d
.text:FFFFF800188C3712 xor r8d, r8d
.text:FFFFF800188C3715 xor edx, edx
.text:FFFFF800188C3717 call cs:ObOpenObjectByPointer
.text:FFFFF800188C371D test eax, eax
.text:FFFFF800188C371F jz short loc_FFFFF800188C3733
.text:FFFFF800188C3721 cmp sil, dil
.text:FFFFF800188C3724 jnz short loc_FFFFF800188C3731
.text:FFFFF800188C3726 mov rcx, [rsp+58h+Object] ; Object
.text:FFFFF800188C372B call cs:ObfDereferenceObject
.text:FFFFF800188C3731
.text:FFFFF800188C3731 loc_FFFFF800188C3731: ; CODE XREF: sub_FFFFF800188C36B0+74↑j
.text:FFFFF800188C3731 jmp short loc_FFFFF800188C376A
.text:FFFFF800188C3733 ; ---------------------------------------------------------------------------
.text:FFFFF800188C3733
.text:FFFFF800188C3733 loc_FFFFF800188C3733: ; CODE XREF: sub_FFFFF800188C36B0+6F↑j
.text:FFFFF800188C3733 xor edx, edx
.text:FFFFF800188C3735 mov rcx, [rsp+58h+Handle]
.text:FFFFF800188C373A call cs:ZwTerminateProcess // <- terminate the process
.text:FFFFF800188C3740 mov rcx, [rsp+58h+Handle] ; Handle
.text:FFFFF800188C3745 call cs:ZwClose // <- close the handle
.text:FFFFF800188C374B jmp short loc_FFFFF800188C3755
.text:FFFFF800188C374D ; ---------------------------------------------------------------------------
.text:FFFFF800188C374D mov dil, 1
.text:FFFFF800188C3750 mov sil, [rsp+58h+var_18]
.text:FFFFF800188C3755
.text:FFFFF800188C3755 loc_FFFFF800188C3755: ; CODE XREF: sub_FFFFF800188C36B0+9B↑j
.text:FFFFF800188C3755 cmp sil, dil
.text:FFFFF800188C3758 jnz short loc_FFFFF800188C376A
.text:FFFFF800188C375A mov rcx, [rsp+58h+Object] ; Object
.text:FFFFF800188C375F test rcx, rcx
.text:FFFFF800188C3762 jz short loc_FFFFF800188C376A
.text:FFFFF800188C3764 call cs:ObfDereferenceObject
.text:FFFFF800188C376A
.text:FFFFF800188C376A loc_FFFFF800188C376A: ; CODE XREF: sub_FFFFF800188C36B0+4A↑j
.text:FFFFF800188C376A ; sub_FFFFF800188C36B0:loc_FFFFF800188C3731↑j ...
.text:FFFFF800188C376A mov rbx, [rsp+58h+arg_0]
.text:FFFFF800188C376F mov rsi, [rsp+58h+arg_18]
.text:FFFFF800188C3774 add rsp, 50h
.text:FFFFF800188C3778 pop rdi
.text:FFFFF800188C3779
.text:FFFFF800188C3779 locret_FFFFF800188C3779: ; CODE XREF: sub_FFFFF800188C36B0+2↑j
.text:FFFFF800188C3779 retn
.text:FFFFF800188C3779 ; } // starts at FFFFF800188C36B0
.text:FFFFF800188C3779 sub_FFFFF800188C36B0 endpSince this IOCTL handler has payload encryption measure, we have to encrypt the payload.
And the structure for the request will be like:
typedef struct _MHYPROT_TERMINATE_PROCESS_REQUEST
{
uint64_t response;
uint32_t process_id;
} MHYPROT_TERMINATE_PROCESS_REQUEST, * PMHYPROT_TERMINATE_PROCESS_REQUEST;